3 min read
The Great Security Lie: Why Buying More Tools (and Renting More Humans) Will Never Save You
From the CEO’s Desk
Raju Chekuri, Chairman, President & CEO of Netenrich,...
 Blog
Blog
3 min read
From the CEO’s Desk
Raju Chekuri, Chairman, President & CEO of Netenrich,...
 Blog
Blog
2 min read
A CISO's Mandate: Stop Traditional Outsourcing, Start Transforming
The...
 Blog
Blog
7 min read
Cyberattacks rarely begin with masterful exploits. They start with small...
 Blog
Blog
5 min read
On a regular Monday morning, Maya, an SOC lead, logs into her company’s asset...
 Blog
Blog
5 min read
Security Operations Centers (SOCs) are busier than ever. However, are they more...
 Blog
Blog
6 min read
The modern Security Operations Center (SOC) is drowning in noise. Each new...
 Blog
Blog
5 min read
Most security teams don’t suffer from a lack of tools; they suffer from too...
 Blog
Blog
5 min read
Attackers move faster than defenders can blink. In 2024, the average breakout...
 Blog
Blog
6 min read
In today's digital landscape, seeing the full risk picture is no longer an...
 Blog
Blog
6 min read
Artificial intelligence (AI) is no longer optional. It has become a necessity...
 Blog
Blog
5 min read
Securing IT infrastructure is never simple, and hybrid cloud environments raise...
 Blog
Blog
6 min read
CISOs face a paradox. Despite multi-million-dollar investments, the average...
 Blog
Blog
2 min read
For more than 15 years,...
 Blog
Blog
4 min read
Strapline: A security data lake is not a dumping ground - it’s a living,...
 Blog
Blog
4 min read
For today’s cloud-native enterprises, “security by default” is a dangerously...
 Blog
Blog
2 min read
Cyber threats are everywhere. Not only that, they come from everywhere. So...
 Blog
Blog
5 min read
Incident response methodology is the...
 Blog
Blog
5 min read
API Security is the practice of protecting the...
 Blog
Blog
4 min read
Security Operations Centers (SOCs) were designed...
 Blog
Blog
2 min read
Most security operations centers struggle with scale, complexity, and context....
 Blog
Blog
4 min read
Cybersecurity in 2025 faces an...
 Blog
Blog
6 min read
Threat actors have continued to bypass advanced security tooling despite the...
 Blog
Blog
3 min read
Security leaders today aren’t just defending infrastructure. They are...
 Blog
Blog
2 min read
April 28 – May 01, 2025 | San Francisco, CA | Moscone Center
Booth #6376 |...
 Blog
Blog
1 min read
Google Cloud Next ‘25 is where innovation in the cloud takes center stage,...
 Blog
Blog
2 min read
Security teams drowning in alerts and starving for insights? DevOps slowed...
 Blog
Blog
5 min read
The rise of sophisticated attack vectors, such as advanced persistent threats...
 Blog
Blog
6 min read
The Chief Information Security Officer (CISO) role has transformed from being...
 Blog
Blog
4 min read
The increasing complexity and scale of cyber threats—fueled by AI and...
 Blog
Blog
5 min read
Security operations (SOC) leaders dream of having a fully scaled unit of...
 Blog
Blog
5 min read
Today adaptable, context-aware SecOps are vital for managing advanced cyber...
 Blog
Blog
4 min read
Low signal-to-noise ratios are slowing you down—here’s how to turn noise into...
 Blog
Blog
3 min read
Traditional SIEMs just aren’t cutting it anymore. They rely on outdated,...
 Blog
Blog
1 min read
Are you ready to take your NFL game day to the next level? Netenrich and...
 Blog
Blog
3 min read
In today's rapidly evolving threat landscape, the need for robust Managed...
 Blog
Blog
3 min read
Security is a delicate balance of trust and vigilance. To truly automate and...
3 min read
In an industry where we pride ourselves on staying one step ahead of threats,...
 Blog
Blog
2 min read
As technology evolves at an unprecedented pace and artificial intelligence...
 Blog
Blog
2 min read
In an era of escalating cyber threats, understanding the evolving landscape...
 Blog
Blog
3 min read
Remember Ferris Bueller? In a way, working in a SOC is like a high-stakes...
3 min read
The traditional Security Operations Center (SOC) is at a critical juncture....
2 min read
“In cybersecurity, the only constant is change.” This age-old adage continues...
 Blog
Blog
4 min read
This is a preliminary report based only on the data leak site (DLS), listed...
 Blog
Blog
1 min read
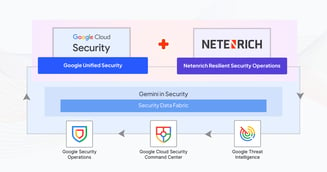
As the first, exclusive pure-play Google SecOps partner, Netenrich is 100%...
 Blog
Blog
5 min read
This article focuses on my research to uncoverthe identity of Hunters...
 Blog
Blog
4 min read
Alpha ransomware, a distinct group not to be confused with ALPHV ransomware,...
 Blog
Blog
1 min read
Visit Netenrich at booth #4424 in Moscone North Expo during RSAC in San...
 Blog
Blog
3 min read
As rising digital connectivity expands the cyber risk plane in 2024, threat...
 Blog
Blog
4 min read
So, what’s a SOC? Some still believe they need a physical SOC building, where...
 Blog
Blog
1 min read
In the ever-evolving landscape of cyber threats, it's not surprising that...
 Blog
Blog
8 min read
This article is not an in-depth reverse-engineering analysis of a ransomware...
3 min read
Beaconing attacks can be difficult—but not impossible—to detect. The more you...
2 min read
With the rise of generative AI models, the threat landscape has changed...
 Blog
Blog
1 min read
Netenrich has entered into a strategic partnership with Cybriant, a leading ...
 Blog
Blog
3 min read
To keep an enterprise up and running, security is essential—and no doubt, why...
 Blog
Blog
2 min read
The internet is a goldmine — but also a jungle — of threat intelligence. You...
 Blog
Blog
2 min read
Detection engineering is the process of designing and implementing systems,...
 Blog
Blog
3 min read
User entity and behavior analytics (UEBA) has been great at solving some...
 Blog
Blog
4 min read
According to the Gartner report, “Automated moving target defense (ATMD)...
 Blog
Blog
2 min read
Netenrich and Google Cloud have joined forces to offer a Fast-Track OEM program...
 Blog
Blog
1 min read
Wondering what to see and who to visit at RSA 2023? Enterprise Management...
 Blog
Blog
2 min read
Ignore the hype: Artificial intelligence (AI) can improve your security posture...
 Blog
Blog
5 min read
If you’re in security, you probably have some tool somewhere showing a lot of...
 Blog
Blog
1 min read
This year, the theme for International Women’s Day is #EmbraceEquity because...
 Blog
Blog
4 min read
Heading into 2023 with digital transformation still top of mind for most...
 Blog
Blog
3 min read
Security information and event management (SIEM) and security orchestration,...
 Blog
Blog
4 min read
Security information and event management (SIEM) is about collecting,...
 Blog
Blog
1 min read
Visit Netenrich at booth #4241 in Moscone South Expo during RSAC in San...
 Blog
Blog
2 min read
At Netenrich, part of what we’re doing is looking "left of bang." Bang (!) is...
 Blog
Blog
2 min read
Threats start with risks. Understanding risks is really just situational...
 Blog
Blog
4 min read
This time of year, people often ask me about highlights from the past year and...
 Blog
Blog
3 min read
"UEBA, it’s just a use case." – Netenrich CISO Chris Morales
He’s not wrong....
 Blog
Blog
5 min read
I recently sat down and interviewed Sharat Ganesh, Google Security product...
 Blog
Blog
4 min read
One vendor uses 5 patterns, the other uses 500 rules. What’s better?
Anyone...
 Blog
Blog
2 min read
MITRE strategy 10 says measure performance to improve performance. It’s...
 Blog
Blog
3 min read
As MITRE points out in strategy 9 of its 11 Strategies of a World-class...
 Blog
Blog
2 min read
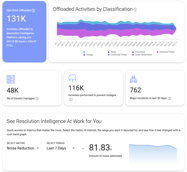
Continuing with our series on ways Resolution Intelligence Cloud helps...
 Blog
Blog
3 min read
MITRE, a U.S.-based tech foundation for the public good, recently released 11...
 Blog
Blog
2 min read
Conversation with Chris Morales, Netenrich CISO, originally published on...
 Blog
Blog
2 min read
Security analysts face plethora of alerts while lacking the means and...
 Blog
Blog
2 min read
Source: Originally published in MSSP Alert on Aug 15 2022
 Blog
KEEP READING
Blog
KEEP READING
 Blog
Blog
2 min read
Resolution Intelligence platform integrated with Google Chronicle is the...
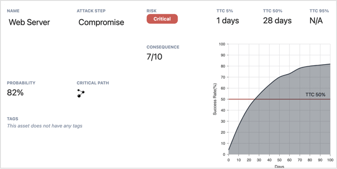 Blog
Blog
4 min read
Digitalization initiatives evolved faster than digital operations in 2020, and...
 Blog
Blog
4 min read
Newly available survey results from Dimensional Research confirm the growing...
 Blog
Blog
3 min read
Cyrptocurrency scams are on the rise impacting businesses and workers. Be aware...
 Blog
Blog
3 min read
“Burnout is a real concern, not only for security professionals,...
 Blog
Blog
2 min read
Troy Abegglen, Customer Success Manager at Netenrich, was the speaker at a...
 Blog
Blog
4 min read
With digital transformation being the goal, learn how to modernize IT...
 Blog
Blog
6 min read
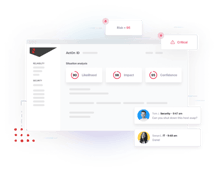
See how our classification and context features power an...
 Blog
Blog
3 min read
Cybersecurity risks often go through the roof when your organization goes...
 Blog
Blog
4 min read
As Netenrich rolls out our Resolution Intelligence Cloud™ ITOps platform, it...
 Blog
Blog
2 min read
Abhishek Bhuyan, Senior Product Architect at Netenrich, and Matt Bromiley, SANS...
 Blog
Blog
3 min read
Short answer: all the time. Since that doesn’t happen, there are some powerful...
 Blog
Blog
3 min read
Brandon Hoffman, Netenrich CISO, was a panelist in the recently completed...
 Blog
Blog
3 min read
Every CISO or IT leader has experienced the tough conversations informing the...
 Blog
Blog
2 min read
I had the delight in talking with fellow security experts about...
 Blog
Blog
4 min read
Attack surface management (ASM) and cyber threat intelligence provide...
 Blog
Blog
4 min read
How Attack Surface Exposure (ASE) accelerates resolution of digital...
 Blog
Blog
3 min read
Technology has become a vital part of your business endeavors. The year 2020...
 Blog
Blog
3 min read
Netenrich leads efforts to help managed service providers modernize IT services...
 Blog
Blog
4 min read
For most of us, 2020 was a year like no other, defined by the most disruptive...
 Blog
Blog
2 min read
“The second you say you’re a SaaS platform, people start asking questions...
 Blog
Blog
3 min read
Pulling security activities out of the NOC into dedicated Security Operations...
 Videos & Webinars
Videos & Webinars
Raju Chekuri, CEO and Chairman of Netenrich, discusses why Netenrich selected...
 Videos & Webinars
Videos & Webinars
1 min read
Raju Chekuri, CEO and Chairman of Netenrich, talks about security challenges...
 Videos & Webinars
Videos & Webinars
Netenrich Enterprise Security Architect Michael Perrault discusses how...
 Videos & Webinars
Videos & Webinars
2 min read
This video explains how the Netenrich Resolution Intelligence Cloud platform...
 Videos & Webinars
Videos & Webinars
3 min read
This video explains how Resolution Intelligence Cloud helps organizations...
 Videos & Webinars
Videos & Webinars
1 min read
In this video, we demonstrate how to search for data and information of...
 Videos & Webinars
Videos & Webinars
1 min read
This video demonstrates how the Resolution Intelligence Cloud platform...
 Videos & Webinars
Videos & Webinars
1 min read
ActOns are linked to services and escalation policies. In this video, we...
 Videos & Webinars
Videos & Webinars
This video demonstrates how Resolution Intelligence Cloud™ employs...
 Videos & Webinars
Videos & Webinars
2 min read
In this video, we'll demonstrate how an ActOn enables operators to aggregate...
 Videos & Webinars
Videos & Webinars
Netenrich and Cybriant join for a lively discussion on how Cybriant is pushing...
 Videos & Webinars
Videos & Webinars
Casey John Ellis, co-founder of Bugcrowd and Disclose.io, joins us on this...
 Videos & Webinars
Videos & Webinars
1 min read
3,000+ alerts per month and a 95% false positive ratio… Sound familiar? Add the...
 Videos & Webinars
Videos & Webinars
1 min read
Managing security and digital operations has become far more challenging due to...
 Videos & Webinars
Videos & Webinars
Google Cloud security experts Dr. Anton Chuvakin and Timothy Peacock lead a...
 Videos & Webinars
Videos & Webinars
In this episode, we are joined by Dr. Anton Chuvakin, Office of the CISO, at...
 Videos & Webinars
Videos & Webinars
We are joined this week by John Giglio, director of cloud security for SADA,...
 Videos & Webinars
Videos & Webinars
Netenrich’s John Bambenek chats with Merys Raymer, Partner Engineering at...
 Videos & Webinars
Videos & Webinars
1 min read
John Pirc, VP and Head of Product Management at Netenrich, explains how...
 Videos & Webinars
Videos & Webinars
2 min read
Netenrich's VP and Head of Product Management, John Pirc, discusses how...
 Videos & Webinars
Videos & Webinars
1 min read
John Pirc, VP and Head of Product Management, Netenrich, explains how the...
 Videos & Webinars
Videos & Webinars
2 min read
Netenrich's VP and Head of Product Management, John Pirc, outlines the...
 Videos & Webinars
Videos & Webinars
John Pirc, Netenrich's VP and Head of Product Management, talks about how...
 Videos & Webinars
Videos & Webinars
Netenrich's John Pirc, VP and Head of Product Management, highlights the six...
 Videos & Webinars
Videos & Webinars
Raju Chekuri, Chairman and CEO of Netenrich, says that security is causing a...
 Videos & Webinars
Videos & Webinars
Sharat Ganesh, Head of Product Marketing at Google Chronicle, shares his...
 Videos & Webinars
Videos & Webinars
Jonas Kelley, Google Cloud's Head of MSSP Partnerships, shares his thoughts on...
 Videos & Webinars
Videos & Webinars
Jonas Kelley, Head of MSSP Partnerships, Google Cloud, answers John Pirc, VP of...
 Videos & Webinars
Videos & Webinars
The Head of Product Marketing at Google Chronicle, Sharat Ganesh, offers his...
 Videos & Webinars
Videos & Webinars
Sharat Ganesh, Product Marketing Head at Google Chronicle, highlights the...
 Videos & Webinars
Videos & Webinars
Sharat Ganesh, Head of Product Marketing at Google Chronicle, asks John Pirc,...
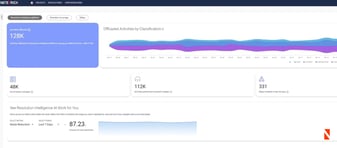 Videos & Webinars
Videos & Webinars
Resolution Intelligence Cloud boosts digital ops productivity with AIOps and...
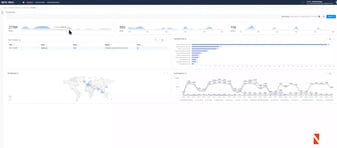 Videos & Webinars
Videos & Webinars
Join David Swift, Netenrich's Principal Cybersecurity Strategist and Platform...
 Videos & Webinars
Videos & Webinars
Many organizations overlook too many of their digital assets when it comes to...
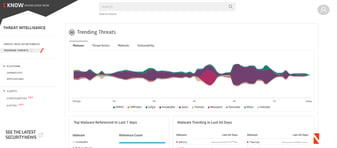 Videos & Webinars
Videos & Webinars
Simon Aldama, a Netenrich Advisor, demonstrates Resolution Intelligence's Cyber...
 Videos & Webinars
Videos & Webinars
Netenrich's Resolution Intelligence streamlines incident management to avoid...
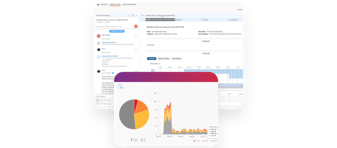 Videos & Webinars
Videos & Webinars
1 min read
Continuing to buy more tools and hire more people does not necessarily lead to...
 Videos & Webinars
Videos & Webinars
John Bambenek, Principal Threat Hunter, explains how low-detection phishing...
 Videos & Webinars
Videos & Webinars
SOC teams are suffering from overwork while threats, infrastructure, data, and...
 Videos & Webinars
Videos & Webinars
1 min read
The pandemic rapidly accelerated digital transformation for organizations...
 Videos & Webinars
Videos & Webinars
John Pirc, VP of Product Management at Netenrich, details the current...
 Videos & Webinars
Videos & Webinars
John Bambenek, Principal Threat Hunter, explains how FontOnLake targets Linux...
 Videos & Webinars
Videos & Webinars
1 min read
To deliver competitive digital experiences, enterprises need Resolution...
 Videos & Webinars
Videos & Webinars
The current state and challenges of cybersecurity with Chuck Harold of...
 Videos & Webinars
Videos & Webinars
1 min read
Reverse the tide of operational complexity to reduce noise, improve incident...
 Videos & Webinars
Videos & Webinars
1 min read
Learn how to identify the right risks and mitigate them quickly in the digital...
 Videos & Webinars
Videos & Webinars
Raju Chekuri, CEO of Netenrich, and Justin Crotty, SVP of Channels at...
Learn about Digital Experience Monitoring and analytics approach to digital...
 Videos & Webinars
Videos & Webinars
Maximize end-user customer experience across your users' interactions with your...
 Videos & Webinars
Videos & Webinars
Learn why it's becoming more important to have security embedded across all...
 Videos & Webinars
Videos & Webinars
Learn how service providers can be more successful and efficient at identifying...
 Videos & Webinars
Videos & Webinars
Justin Crotty, VP of Channels and Simon Aldama, Sr. Director of RiskOps...
 Videos & Webinars
Videos & Webinars
Take IT Operations to the next level by enabling stability, resilience, and...
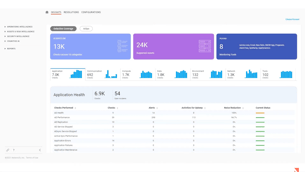 Videos & Webinars
Videos & Webinars
Modernize NOC and SOC Ops to reduce IT’s workload while delivering better...
 Videos & Webinars
Videos & Webinars
Core to business initiatives and delivering outcomes. Solving security problems...
 Videos & Webinars
Videos & Webinars
Rich Lane discusses the significance of data-driven operations and how to...
 Videos & Webinars
Videos & Webinars
Bringing in new tools won’t get you where you need to go. It's best to...
 Videos & Webinars
Videos & Webinars
Protect assets in the cloud, outsourced critical infrastructure, and other...
 Videos & Webinars
Videos & Webinars
Learn how automation can help you correlate information and identify patterns...
 Videos & Webinars
Videos & Webinars
More than 6,000 vCenter installations potentially at risk as RCE exploits...
 Videos & Webinars
Videos & Webinars
Learn how MSPs are innovating services for scale and growth.
 Videos & Webinars
Videos & Webinars
Fine tune your service offerings with a data-driven digital operations (Digital...
 Videos & Webinars
KEEP READING
Videos & Webinars
KEEP READING
 Videos & Webinars
Videos & Webinars
1 min read
Join Netenrich experts John Bambenek and Rich Lane to learn how a...
 Videos & Webinars
Videos & Webinars
1 min read
Ops teams buy tools to gain visibility into their environments but still can’t...
 Videos & Webinars
Videos & Webinars
1 min read
In an industry plagued with buzzwords, “RiskOps” is an idea whose time has...
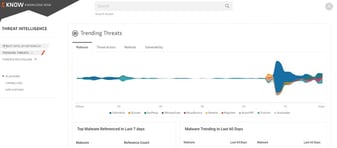 Videos & Webinars
Videos & Webinars
1 min read
Cybersecurity is war, so why not borrow concepts from U.S. armed forces? Join...
 Videos & Webinars
Videos & Webinars
1 min read
About ActualTech Media EcoCast Events: The EcoCast is a smaller version of our...
 Videos & Webinars
Videos & Webinars
Chris Morales (Netenrich), Chris Crowley (Montace), and Eric Parizo (Omdia)...
 Case studies
Case studies
4 min read
As digital transformation increases in...
 Case studies
Case studies
4 min read
Cloud Software Group (CSG), a $4.5 billion global software leader, embarked on...
 Case studies
Case studies
4 min read
Facing a crisis of trust after its previous MDR vendor failed to disclose a...
 Case studies
Case studies
2 min read
A prominent regional bank with over 80 branches across Southern California,...
 Case studies
Case studies
2 min read
A major healthcare technology company, with over $800M in revenue had relied on...
 Case studies
Case studies
3 min read
Resolution Intelligence Cloud™ operationalizes security at service-provider...
 Case studies
Case studies
2 min read
Netenrich's Resolution Intelligence Cloud's contextualized data enables a large...
 Case studies
Case studies
3 min read
Discover how Netenrich's Resolution Intelligence Cloud helps MultiCare with its...
 Case studies
Case studies
2 min read
Read how Resolution Intelligence Cloud™ transformed SysTools, a cybersecurity...
 Case studies
Case studies
3 min read
Netenrich helps a service provider build scalable, agile enterprise service...
 Data Sheets
Data Sheets
2 min read
Migrating to Google...
 Data Sheets
Data Sheets
3 min read
Netenrich SecOps Operate...
 Data Sheets
Data Sheets
4 min read
Because a One-Size-Fits-All MDR ... Fits No One!
Not all businesses operate the...
 Data Sheets
Data Sheets
2 min read
Resolution Intelligence Cloud is a cloud-native data analytics platform for...
 Data Sheets
Data Sheets
3 min read
Resolution Intelligence Cloud™ is a cloud-native data analytics platform for...
 Data Sheets
Data Sheets
3 min read
Resolution Intelligence Cloud is a cloud-native platform for managing digital...
 Data Sheets
Data Sheets
2 min read
Attack Surface Exposure (ASE) combines security expertise and artificial...
 Data Sheets
Data Sheets
2 min read
Monitoring is... |
 Guides
Guides
5 min read
 Guides
Guides
5 min read
 Guides
Guides
6 min read
 Guides
Guides
4 min read
 Guides
Guides
5 min read
 Guides
Guides
8 min read
 Guides
Guides
3 min read
Google Chronicle, part of Google SecOps, is a powerful tool for security data...
 Guides
Guides
5 min read
Netenrich's Adaptive MDR™ solution is designed to enable proactive and...
 Guides
Guides
8 min read
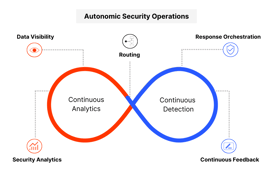
What exactly is Autonomic Security Operations (ASO), and why do many of the...
 Guides
Guides
27 min read
Implement MITRE’s recommended world-class SOC strategies using the Netenrich...
 Guides
Guides
6 min read
Implement an open mesh architecture for cybersecurity — and all digital...
 Guides
Guides
8 min read
Secure operations — different from security operations and security...
 Guides
Guides
11 min read
This guide explains seven times to attack your attack surface, what you...
 Guides
Guides
5 min read
This guide helps CISOs, CIOs, and their boards to manage cybersecurity risk...
 Guides
Guides
6 min read
This is an MSSP Technology Checklist of threat detection and security...
 Guides
Guides
4 min read
This guide helps CISOs, CIOs, and their boards to manage cybersecurity risk...
 Guides
Guides
2 min read
Right-size tool strategies, bridge skills gaps, and align operations with...
 Guides
Guides
9 min read
The attack surface is the sum of all internet-facing digital assets,...
 Guides
Guides
5 min read
Security tests serve different needs and have different methodologies. In...
 Guides
Guides
4 min read
People often get the terms attack surface, and attack vector confused....
 Reports
Reports
1 min read
Netenrich commissioned a third-party organization to conduct a security survey...
 Reports
Reports
1 min read
Matt Bromiley, a SANS Certified Instructor, reviews Netenrich's Resolution...
 Reports
Reports
The latest survey results from Dimensional Research highlight the growing need...
 Reports
Reports
This research reviews key findings from a global survey on how companies manage...
 Reports
Reports
Read what SANS says about Netenrich's Attack Surface Intelligence (ASI)* and...
 Reports
Reports
Netenrich teamed up with EMA to outline the steps for implementing situational...
2 min read
Jul 25, 2025 by Michael Beavers
Most security operations centers struggle with scale, complexity, and context....
1 min read
Jul 20, 2023 by Netenrich
Netenrich has entered into a strategic partnership with Cybriant, a leading ...
4 min read
Jul 18, 2023 by John Pirc
To keep an enterprise up and running, security is essential—and no doubt, why...
2 min read
Apr 8, 2025 by Netenrich
Google Cloud Next ‘25 is where innovation in the cloud takes center stage,...
8 min read
Feb 20, 2025 by Netenrich
The Chief Information Security Officer (CISO) role has transformed from being...
4 min read
Sep 17, 2024 by Raju Chekuri
Traditional SIEMs just aren’t cutting it anymore. They rely on outdated,...
9 min read
Nov 12, 2025 by Netenrich
Cyberattacks rarely begin with masterful exploits. They start with small...
8 min read
Nov 11, 2025 by Netenrich
On a regular Monday morning, Maya, an SOC lead, logs into her company’s asset...
7 min read
Nov 11, 2025 by Netenrich
Security Operations Centers (SOCs) are busier than ever. However, are they more...

















The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
