A Prism of Data—Focused on Risk Management
Published on October 12, 2022 | Last updated on September 23, 2025 | 2 min read

In our blogs, “Data in Context Is Everything to Security Operations” and “Give SOCs the Authority to Be a Top Business Priority," we began discussing ways organizations can bring to life some of the strategies in MITRE’s new book, 11 Strategies of a World-class Cybersecurity Operations Center.
Here, we focus on the third strategy. You’ll see a pattern emerging: Secure operations requires that everyone is working from the same data.
MITRE SOC Strategy 3: Build a SOC structure to match your organizational needs
CHALLENGE: What’s appropriate for one organization may not work for another; there are many models to build from.
Cybersecurity is more than a technical problem, it’s an organizational problem. And while it’s not possible to have absolute protection in a connected world, you can lessen the odds and impact of cyberattacks by taking a risk-based, business-aligned approach to managing cybersecurity and building an effective SOC structure.
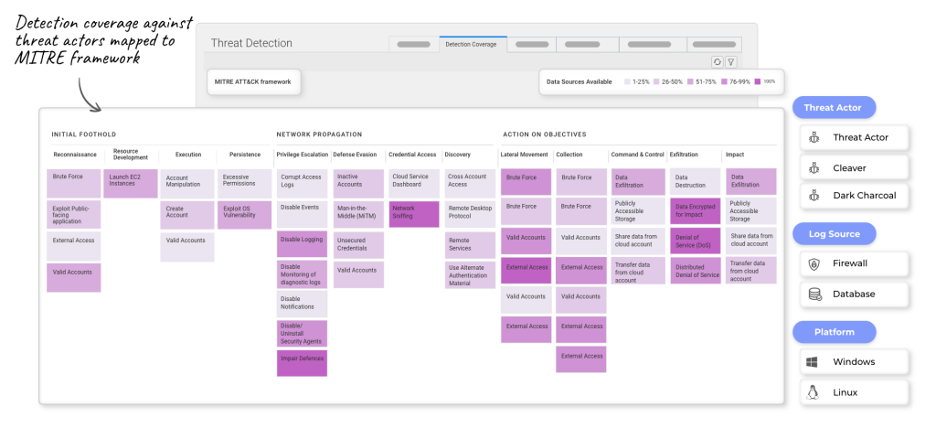
Per MITRE’s first recommended strategy, organizations need to know what they are protecting and why. With that knowledge, they then need to dig deeper to understand where they are vulnerable — and the MITRE ATT&CK® Framework is a great resource for assessing cyber risk. A global knowledge base of cyber adversary behavior compiled into a taxonomy of tactics and techniques across the threat lifecycle, ATT&CK® takes a threat actor’s point of view to help organizations understand how the bad guys conceive, prepare for, and execute attacks.
SOCs can use the ATT&CK taxonomy to understand the “footprint” of known, real-world attacks and identify where their organization may be vulnerable. Next, they can focus on minimizing the greatest risks in the most cost-effective manner to meet their business’ risk tolerance. For example, by implementing a platform like Resolution Intelligence Cloud, they can:
- Apply attack surface management (ASM) strategies and leverage threat research for more proactive identification and remediation of vulnerabilities on key assets.
- Detect patterns of risky behavior most relevant to your company, industry, and known exploits.
- Correlate events from multiple detection sources and use behavioral analytics not only to find and respond to threats more quickly, but also proactively shape and strengthen defenses.
- Gain the context to know if situations require action with ActOns™. These highly contextualized, pre-incident tickets correlate detections, user and asset data, evidence, ATT&CK mapping, and graphs, reducing noise by 80% and saving analysts hours of research time. Prioritized by cyber risk and impact to the business, ActOns let them — and by them, we mean all key stakeholders on a ticket — know where to focus their attention.
Building situational awareness by bridging silos
“You can’t fight in here. This is the war room!” said President Merkin Muffley.
Both iconic and ironic, the line from Dr. Strangelove is meant to amuse. But what if there were no fighting in war rooms? Like the virtual war rooms in Resolution Intelligence Cloud that you can initiate from the ActOn console. These war rooms streamline processes, eliminate redundant work, and most importantly, facilitate collaboration and faster decision-making across siloed departments. In these war rooms, everyone is on the same page, turning alert detections into actions with a focus on solving the most critical, confirmed issues first. In these war rooms, there’s no fighting — except against threat actors.
Here are some examples of what happens in Resolution Intelligence Cloud's ActOn war rooms:
- SOC experts chat with IT managers to shut down devices that are at risk. When another team member starts a shift, the handover is easy because conversations and actions are documented in one place.
- Service-provider security experts work directly with their customers, sharing insights and conferring on appropriate actions to take for swift resolution. They can review what happened — from ActOn to actions — to ensure there are no repeats.
- Converge people, process, and tools into cohesive and consolidated digital operations.
Building the right structure for a modern SOC may require re-imagining and breaking down traditional constructs. It’s not about SecOps. It’s not about ITOps. It’s not about CloudOps. It’s about secure operations across all ops, which requires enhanced transparency and better use of data — the more, the better — from across the entire organization for a common operational picture (COP) that helps make the business as secure and successful as possible.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.






