Data in Context Is Everything to Secure Operations
Published on October 5, 2022 | Last updated on December 18, 2025 | 3 min read

MITRE, a U.S.-based tech foundation for the public good, recently released 11 Strategies of a World-class Cybersecurity Operations Center — an amped-up practical guide to enhancing digital defenses and improving Security Operations Center (SOC) efficacy.
The book goes deep into how the right approaches can help organizations — of any size or IT/SOC maturity level — overcome a multitude of challenges to optimize operations. And with Netenrich’s Resolution Intelligence Cloud, they can execute these approaches and shift ops forward with data analytics and a predictive approach. This is the first in a series deconstructing MITRE's 11 strategies and showing how Netenrich's Resolution Intelligence Cloud with Chronicle, Google's Cloud Native SIEM, can improve your security and risk posture and protect your digital operations.
MITRE SOC Strategy 1: Know what you are protecting and why
THE CHALLENGE: Cybersecurity operations exist to support their organizations’ missions, so they need context for the data that they see and the action they take.
The accelerated pace of business transformation is generating an explosion of infrastructure assets, applications, and data. We’re talking volumes of data that analysts must investigate to discover the most critical issues.
Too much information (TMI) is rarely a good thing — and many organizations struggle with having to limit the security data they ingest and store because it’s too expensive. On the flip side, if they don’t have all the relevant data — from assets, apps, and users — they’ll create blind spots and increase vulnerability.
But what if you could turn TMI into a good thing, leveraging all your security data for threat forecasting and early detection without breaking the budget?
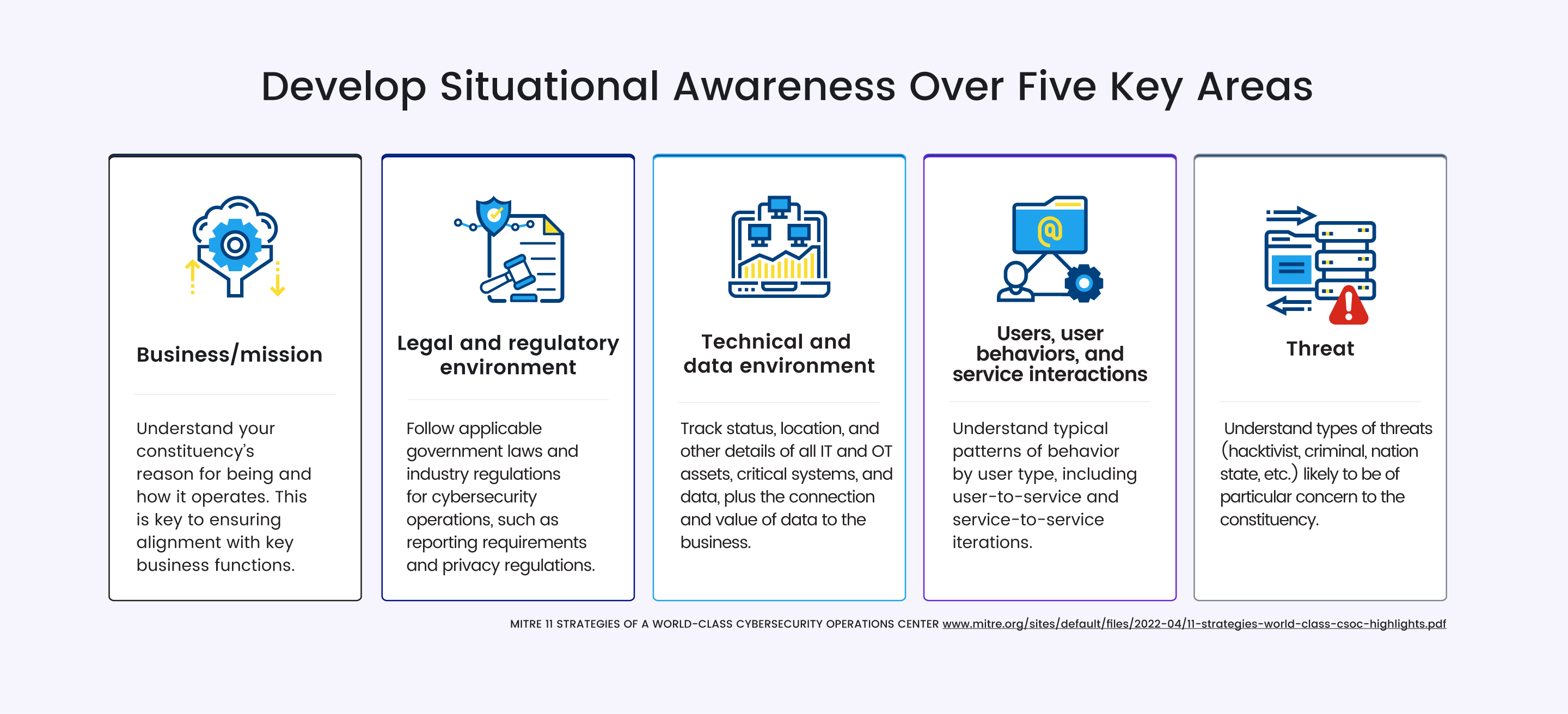
MITRE suggests that SOC teams start by developing better situational awareness[1] across five key areas:
- The business/mission (what to prioritize)
- Legal and regulatory environment (what you have to do)
- Technical and data environment (what you are monitoring)
- Users, user behaviors, and service interactions (also what you are monitoring)
- Threat (what adversaries are trying to do).
How do you develop situational awareness? With contextualized data.
Data silos create blind spots and impede situational awareness
Data is meaningless without context. Sure, your car’s blinking check engine light indicates there’s an “issue,” but it’s not enough to tell you whether this is an emergency that may cause your car to explode or just a heads up that it’s time for scheduled maintenance. In short, it’s not a complete picture. The complete picture requires more data, leading to situational awareness.
In the cyber world, situational awareness is the basis for sound decision-making and improving outcomes. To establish it across security and digital operations, you need a common operational picture (COP)[2] — which is exactly what Resolution Intelligence Cloud + Google Chronicle provides.
If you can’t pinpoint a problem, how can you resolve it?
Resolution Intelligence Cloud applies real-time data analytics, context, and correlation to identify patterns and anomalies across hybrid infrastructures that predefined rules can’t. After all, to define a rule, you have to be aware of the threat.
Resolution Intelligence Cloud turns an abundance of security and digital operations data into actionable intelligence — a clear, contextualized picture and advanced risk scoring — that allows SOC teams to determine which situations are incidents, prioritize them, and make faster, better informed security decisions in collaboration with other key stakeholders.
This picture is not static and can change quickly. Resolution Intelligence Cloud’s machine learning capabilities are also constantly improving detection and automated responses over time to prevent or mitigate risks to mission-critical services — which vary by organization. As MITRE mentions, a legal firm may prioritize data confidentiality while a financial services company prioritizes data integrity, and a power company prioritizes availability and, literally, keeping the lights on.
Not all data is created equal
All data is good, but it takes a lot of good data to get to the right data.
Historically, data ingestion, storage, and anything close to real-time analysis has been expensive. But without adequate data, not only from all security and operations telemetry but also over time, SOCs cannot determine when and if something is going wrong and how critical that something wrong may be.
The good news is that today, data intake doesn’t have to be limited or expensive. Leveraging Google Chronicle as its security data lake, Resolution Intelligence Cloud ingests and unifies security telemetry — across endpoints, applications, hybrid infrastructure, and user behavior — at petabyte scale, but at low cost, and provides “hot data” for a year. Telemetry that’s enriched with threat feeds, OSINT data, CVE information, and expert insights to provide even further granularity and context for investigation and triage. Thus, CISOs no longer have to choose between budgetary constraints and adequate security. They can scale to capture all the data they need.
What’s more, in a single console, the platform gives SOC teams actionable insights called ActOns. These highly contextualized, pre-incident tickets give analysts the information they need — including a business risk score based on likelihood, impact, and confidence — to drive informed decisions and actions, whether that’s proactively strengthening the organization’s security posture or hastening response and remediation across an expanding attack surface.
[1] Situational awareness: The perception of environmental elements and events with respect to time or space, the comprehension of their meaning, and the projection of their future status.
[2] Common operational picture (COP): A single identical display of relevant information shared by more than one command. A common operational picture facilitates collaborative planning and assists all echelons to achieve situational awareness. Source: Joint Publication [JP] 3-0.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







