Security Podcasts for CISOs & SOC Leaders
🎙️ The Last Drift | Where Security Leaders Get Real
No more breach recaps. The Last Drift brings candid CISO conversations on simplifying complexity, adapting SOCs, and leading with data.

Featured Podcast:
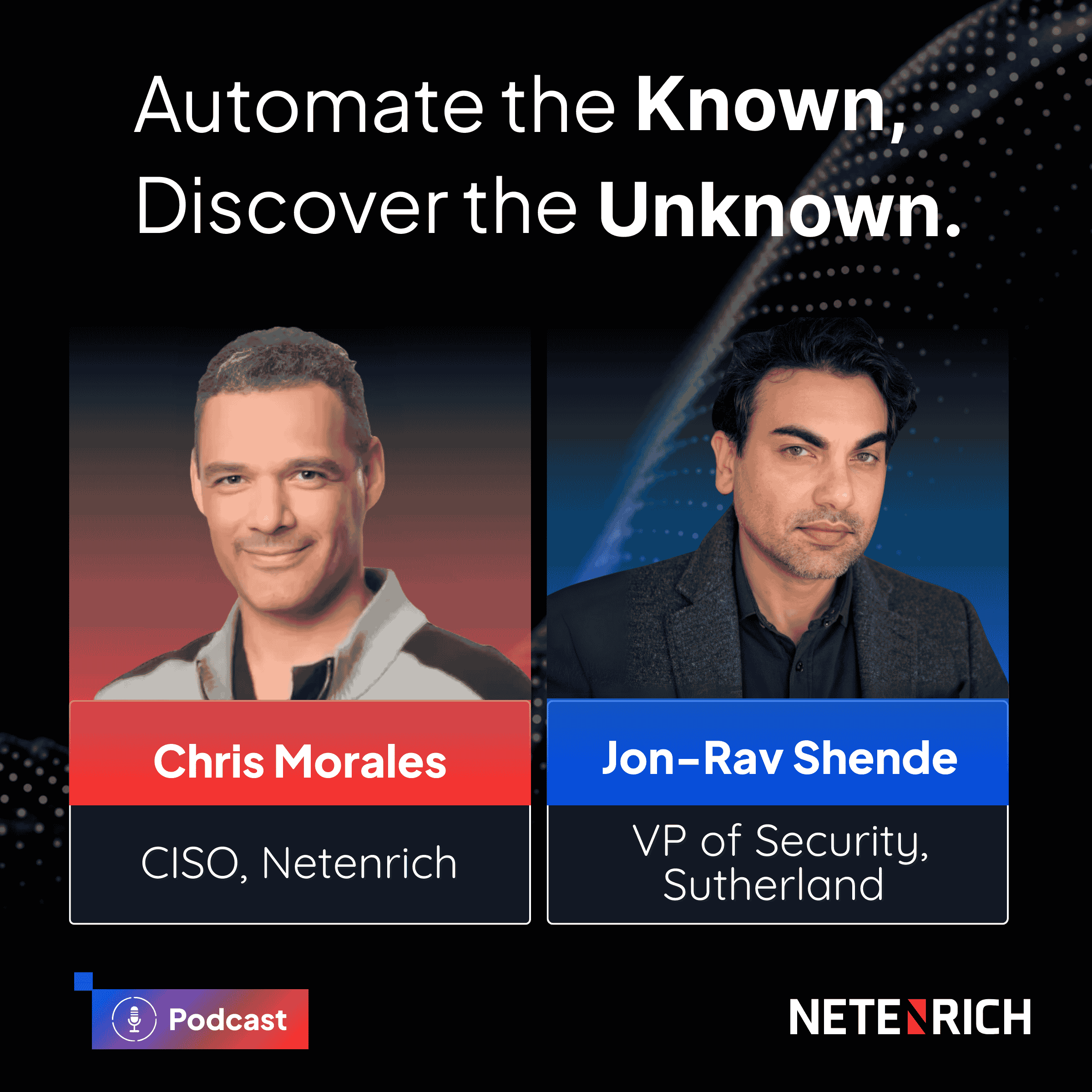
Automate the Known, Discover the Unknown
Sept 2025
Why today’s SOC can’t keep up with burnout, tool sprawl, and blind spots - and how CISOs can flip the script with automation-first strategies that uncover risks others miss.
25 mins On-Demand Hosted by Chris Morales & Jon-Rav Shende
Why Do Security Leaders Listen?
First-hand insights from global CISOs & SecOps experts
Real-world lessons on navigating complexity at scale
Practical frameworks for SOC transformation and adaptive security
Exclusive access to Netenrich research & insights
Meet Your Hosts
We’re here to challenge outdated playbooks and give CISOs a realistic path forward - less noise, more measurable outcomes.


Raju Chekuri
President and CEO

Chris Morales
CISO & Head Of Security Strategy

















Learning the Path to the Autonomous SOC - Netenrich
CISO
Netenrich brought unparalleled clarity and control to our once‑complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-informed approach has ensured our operations align seamlessly with our growth strategy.
CISO
Netenrich brought unparalleled clarity and control to our once‑complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-informed approach has ensured our operations align seamlessly with our growth strategy.
CISO
Netenrich brought unparalleled clarity and control to our once‑complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-informed approach has ensured our operations align seamlessly with our growth strategy.
CISO
Netenrich brought unparalleled clarity and control to our once‑complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-informed approach has ensured our operations align seamlessly with our growth strategy.
CISO
Netenrich brought unparalleled clarity and control to our once‑complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-informed approach has ensured our operations align seamlessly with our growth strategy.
CISO
Netenrich brought unparalleled clarity and control to our once‑complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-informed approach has ensured our operations align seamlessly with our growth strategy.
DEATH Labs Playlist
About Netenrich
- At Netenrich, we live and breathe security operations. Every podcast draws from decades of experience helping enterprises modernize SOCs and lead with intelligence.
- Netenrich Adaptive MDR Services powers smarter detection, faster response, and real-time risk insights, trusted by hundreds of organizations across healthcare, finance, and technology.




.png?width=100&height=101&name=Vector%20(4).png)

