Using Cyber Threat Intelligence with Contextual Data to Prevent Threats
Published on October 26, 2022 | Last updated on July 31, 2025 | 3 min read

The fifth strategy in MITRE’s 11 Strategies of a World-class Cybersecurity Operations Center counsels organizations to prioritize incident response (IR) by defining response steps and escalation paths and codifying them in operating procedures and playbooks.
Netenrich couldn’t agree more.
One of the primary challenges of creating playbooks is that you need to start with effective operating procedures that you can turn into playbooks. That’s where many organizations struggle.
Security orchestration, automation, and response (SOAR) technology helps coordinate, perform, and automate incident response. There are some excellent products out there for automating your playbooks, like Google’s Chronicle SOAR (formerly Siemplify), which we’ve integrated with our Resolution Intelligence Cloud platform. Resolution Intelligence Cloud provides extensive context — correlated alert, asset, user, and related data — to Chronicle SOAR, enabling smarter and faster resolution.
However, since playbooks aren’t our focus, let’s jump to strategy 6 to discuss the key role cyber threat intelligence (CTI) plays in response.
MITRE Strategy 6: Illuminate adversaries with cyber threat intelligence
CHALLENGE: Finding malicious activity and other traces of adversaries can be challenging. SOCs need to be proactive and identify threats before they enter their constituency’s environment.
MITRE says, “Analysis and tailoring of CTI and establishing context enables the SOC to prioritize the actions of detection and prevention to conserve resources, honing the effectiveness of SOC operations.”[1]
Once more, we agree, and we’d like to call out the importance of using context to prioritize actions.
Finding malicious activity and mapping threats against assets isn’t easy. This is especially true when assets are frequently coming on and offline, and when asset information isn’t integrated with security data. Threat intel helps solve this problem by providing insight into the threat landscape and pointing to possible risks, vulnerabilities, and exposures. In other words, you can focus on warding off known threats and minimizing their damage.
It’s crucial — and extremely challenging — to determine whether a specific piece of intelligence applies to a situation or asset. For that, you need context that enables you to determine the risk the intelligence poses to your organization.
To “conserve resources, honing the effectiveness of SOC operations” as MITRE advises, you need to focus on the intelligence that poses the greatest risk. Which begs the question, how do you figure that out? The key questions you need to answer are:
- Is this intelligence relevant to my organization, users, assets, etc.? Which ones and how important are they to the business?
- What is the potential impact of the intel?
- What is the likelihood of that impact happening?
- What is my confidence in the intel?
Context gives you a greater understanding of threats in terms of the risks they pose, their potential impact, and the potential damage they could cause. Context helps organizations prioritize action and fine-tune investigations to find the root cause of urgent problems and plug holes faster.
But how do you make threat intel and context actionable?
Resolution Intelligence provides actionable contextual data
Resolution Intelligence Cloud makes context actionable. Because Netenrich focuses on secure operations — not just security or detection — the platform gives you the context you need to optimize the effectiveness of SOC operations.
Resolution Intelligence Cloud answers and quantifies the four questions above with risk scoring.
Organizations can be much more effective if, for example, they know whether an attack is targeting a high-value business resource or a more isolated, non-critical asset. With Resolution Intelligence Cloud, they can automatically discover and tag assets according to business importance. Moreover, they can map known threats against any asset to see where the organization may not have sufficient log coverage for early detection — even for a particular known threat.
Resolution Intelligence Cloud maps an organization's security posture to the MITRE ATT&CK framework to illustrate detection coverage. This “lay of the land” overview shows risky behaviors, threats, and pre-incident situations correlated with information on related events, assets, and users.
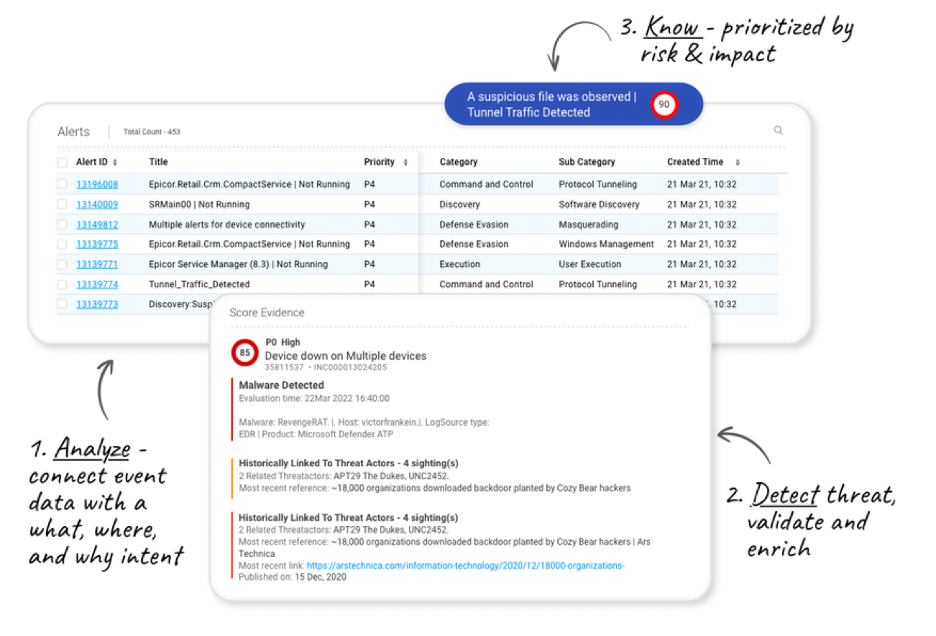
Using advanced data analytics and machine learning, the platform provides ActOns™: curated, contextual data including threat intel and related alerts, assets, and user data that analysts can act on. ActOns are prioritized based on likelihood, impact, and confidence for situations that may become or already are incidents — so analysts know which situations require immediate attention and, just as importantly, which don’t. ActOns aid security analysts respond effectively to intel and suspicious activity before damage or disruption can occur.
Get proactive by focusing on the right threat intelligence
You can only prevent what you know — for example, data from solutions like endpoint detection and response solutions (EDRs) and SOARs lets organizations see what has occurred. But as MITRE says, the right threat intelligence in the right context gives organizations a proactive edge.
Resolution Intelligence Cloud not only helps you take proactive measures in response to threat intel, but as threats evolve, it also helps you predict future adversary behavior and prepare to withstand potential attacks.
So you have the context and framework you need to take advantage of threat intelligence to illuminate adversaries — and stop them.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.






