Identity Behind Hunters International Ransomware Group’s Dedicated Leak Site Exposed
Published on February 5, 2024 | Last updated on December 18, 2025 | 5 min read

This article focuses on my research to uncover the identity of Hunters International ransomware group’s (Surface Web) Dedicated Leak Site (DLS). It could be an affiliate of Hunters International or anyone (in)directly connected to the group.
Hunters International is a Ransomware-as-a-Service Group (RaaS) that appeared in October 2023 and is possibly a spin-off of Hive ransomware, a group the FBI breached in January 2023. On their official Onion site, Hunters International made the following official statement:
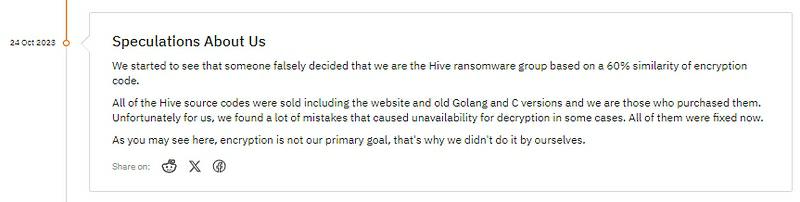
Based on this screenshot, the group’s moderators/threat actors first announced their DLS on October 24, 2023.
Introduction
Hunters International targets Windows and Linux environments for data encryption and exfiltration. Once it completes data exfiltration, it adds a .LOCKED extension to the encrypted files on a victim machine. To date, the group has listed ~38 global victims, spanning industries such as health, automotive, manufacturing, logistics, financial, education, and food.
Hunters International DLS
Hunters International is known for organizing victims by country on their DLS.
By tracing their victim listing timeline, I found they listed their first victim on October 20, 2023. While this indicates the DLS has been functional since that date or before, the site only began garnering views as of October 28, 2023, following reports from various infosec resources of its similarity to Hive ransomware code.
Note: It’s possible that team members were using the website before its official public launch.
Hunters International launched a clear website of their Onion DLS (with the same name) on January 22, 2024.
RaaS groups may launch DLS for several reasons.
- By threatening to expose sensitive data, they can coerce victims into paying the ransom quickly.
- Even if the victim pays the ransom, some groups will still sell the data on the dark web or use it for other malicious purposes to generate additional income.
- By publicizing successful attacks and data leaks, they can enhance their reputation within criminal circles and potentially attract more customers.
- These sites can not only put pressure on the immediate victims but also their partners or customers, which can potentially amplify the impact of attacks and increase the likelihood of ransom payments.
- Ransomware operators like ALPHV, for example, have reported victim data breaches directly to the SEC, exposing the fact the company had not reported in the required four-day regulation window. This tactic can work to tarnish an organization’s business reputation.
Huntersinternational.org
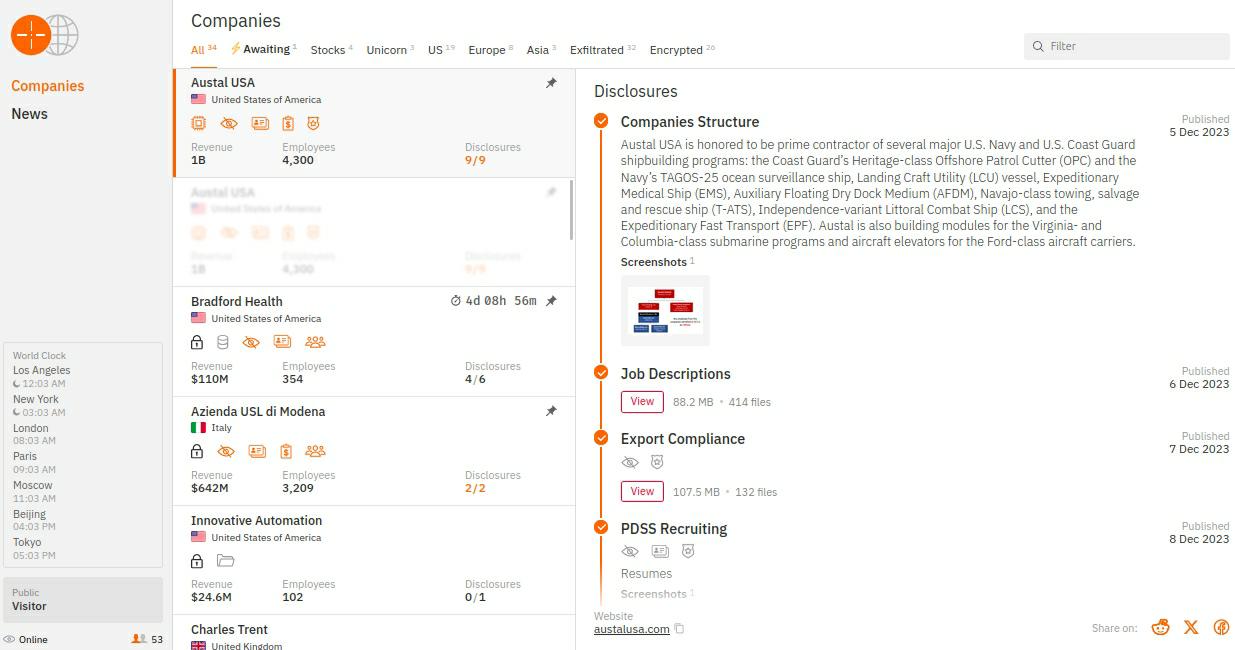
The new domain was previously a legitimate active domain from 2017 to 2021 (for news and blog posts), but had since been deactivated.
The threat actors reactivated this domain in January 2024 to launch the DLS.
While inspecting the source page of this site, following quotes are found:-
'Keep calm and go hunting.',
'Everybody wants to eat but few are willing to hunt.',
'Imagine life without hunting. Now slap yourself and never do it again.',
'Opening day of hunting season should be a national holiday.',
'If I\'m not hunting, I\'m thinking about it.',
'Live to hunt. Hunt to live.'
These quotes are unusual to be found in a Leak Site of a Ransomware group.
DOMAIN ANALYSIS
The clear web domain of Hunters International Leak site is hosting a service named “Onion Location Framework” which is used to power Dark Web Domain names.

The hidden agenda behind this technique is to gain greater visibility and generate more views (Note: Hunters International was a genuine domain in 2017).
Domain analysis
It appears Hunters International used a fake identity (Mihail Kolesnikov) to register the aforementioned domain.
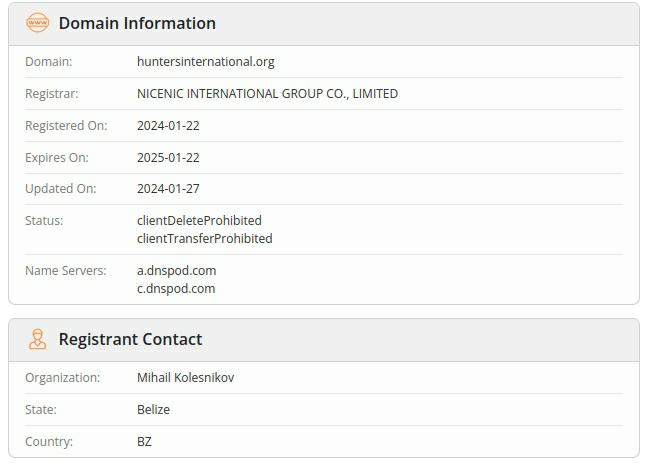
Other cybercriminals have used this same fake identity, which has been tied to multiple malicious indicators, including Rilide Infostealer and Snatch ransomware phishing domains.
The malicious websites registered in the name of Mihail Kolesnikov can be traced to Russia and are mostly registered under the domain name NiceNIC. Below are some hosted sites under this name.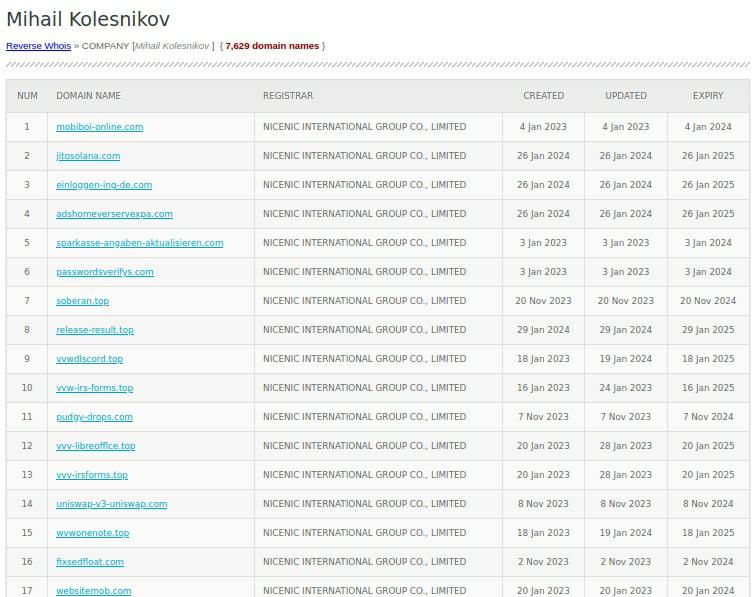
The practice of adopting a criminal identity found on the internet helps groups masks their real identity. This fake persona is used exclusively for offensive cyber activities.
The raw WHOIS data shows that sensitive fields, such as name, street, and phone, are masked due to privacy concerns. However, not all identities will stay safe for long.
Real identities
During a deeper domain analysis, I found two email addresses linked to the Hunters International DLS:
oyewolelawrence@gmail.com
cacmountofvictory@gmail.com
Of these, the following was used to sign up for a privacy service tied to Hunters International:
REAL IDENTITY EXPOSED
=====================
Domain: huntersinternational.org
IP: 193.106.175.48
Location: RUSSIA
Hosting Provider: IQ HOST
ASN: AS50465
Registered with: NICENIC
NOTE: This does not mean these identities control the entire infrastructure of Hunters International; only that these persons/personas are (in)directly involved with the group.
For security reasons, I cannot share how I pinpointed the threat actors.
First email address analysis
Researching the name OYEWOLE LAWRENCE and based on same-name matches, I found it is highly probable this name is Nigerian.
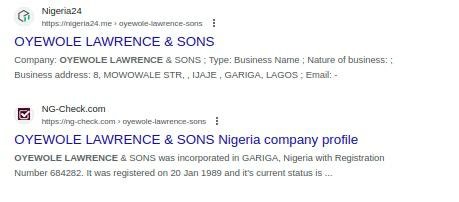
This could be genuine or another decoy from the group to conceal their identity. Thus, we cannot take the bait.
Let’s take a deep dive into threat actor’s email address. While checking for breached records, I found that the same email address appeared five or more times on Have I Been Pawned (HIBP):
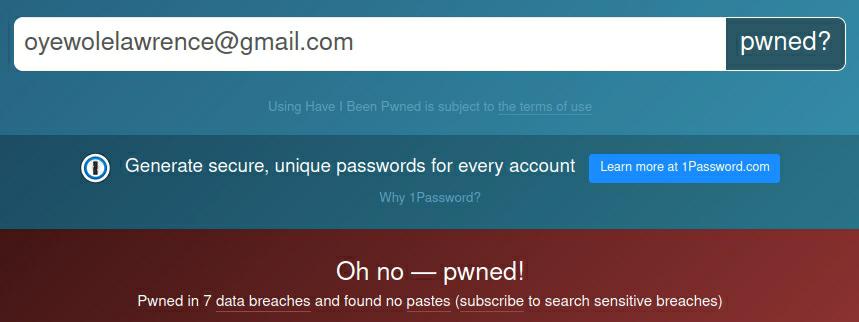
The listed leaked databases (with years of breaches) are:
BITTLY: 2014
EXPLOIT.IN: 2016
LINKEDIN: 2016
CLEARVOICE SURVEY: 2021
PDL DATA BREACH: 2019
TWITTER: 2023
Based on this list, the threat actor(s) has been using this email address for a long time for various network activities.
Wanting to know more, I dug deeper, researching the leaks myself to find the plain-text password of the threat actor. Here’s what I uncovered.
e97bb3b1 (previous Gmail Password)
jesusthelord (Used in forums and other services)
I also found a LinkedIn profile for “LAUREL GRACE” that uses the same email address but is currently inactive:
https://www.linkedin.com/in/laurel-grace-02373a24
Second email address analysis
I considered the second email address (cacmountofvictory@gmail.com) because it had the same recovery email address in Gmail service.
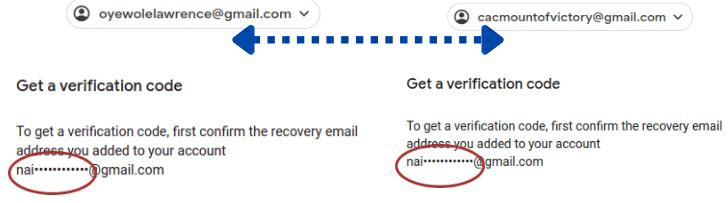
Details of the second identity are:
Email: cacmountofvictory@gmail.com
Registrant Name: Olowo Kehinde
Organization: Cac Mount Victory
Registrar: 007Names
Activity Date: April 17, 2017
A search for the name “OLOWO KEHINDE” pointed, once again, to Nigeria.
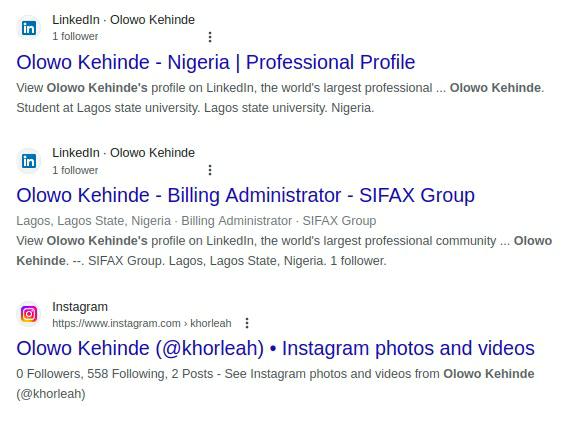
This research shows the threat actors or their affiliates are likely to have a strong connection to Nigeria.
Tracking IP address
While checking the reputation score of the hosted IP (193.106.175.48), I found that the same IP had previously been associated with loseriedia[.]xyz, which is hosted as a C2 for the RedLine Stealer botnet. It also hosted several phishing domains related to a gift card in 2023.
While digging into the server architecture, I found that Hunters International domain is hosted on a Linux Debian machine powered by an nginx server.
Fingerprint of Huntersinternational.org
Host Key Fingerprint: 48b0a224697ead43ca1272c34a4777662049964913f083a40a5458a4ee1f78
TOR Onion domains
Here is a list of Onion domains maintained by Hunters International on Dark Web:
TOR ONION DOMAINS
=================
https://hunters55rdxciehoqzwv7vgyv6nt37tbwax2reroyzxhou7my5ejyid.onion/
https://hunters55atbdusuladzv7vzv6a423bkh6ksl2uftwrxyuarbzlfh7yd.onion/
https://hunters33dootzzwybhxyh6xnmumopeoza6u4hkontdqu7awnhmix7ad.onion/
https://hunters33mmcwww7ek7q5ndahul6nmzmrsumfs6aenicbqon6mxfiqyd.onion/
It’s important to note that the group has managed to maintain different vanity domain names for the leak blog and victim portal.
The domain that starts with hunters55 is the leak blog. And the domain that starts with hunters33 is the victim portal.


As the group had used a vanity address generator for v3 Onion domains, we can assume with high probability that the group is using a GitHub tool named mkp224o to generate their Onion domains.
Healthcare, a specially targeted sector
Based on the victim list, the group is mainly targeting healthcare systems in United States and Europe. At the time of writing, Hunters International has compromised the following healthcare-related companies:
Bradford Health
Blackstone Valley Community Health Care
Fred Hutchinson Cancer Research Center
Azienda USL di Modena
Covenant Care
Crystal Lake Health Center
Deegenbergklinik
Dr. Jaime Schwartz MD, FACS
Recently, Integris, the largest Oklahoma-owned health system in the United States, was hit by ransomware. The modus operandi of Hunters International was also observed with Fred Hutchinson Cancer Research Center, where patients received a threat email to pay $50 to prevent the sale of their data on the Dark Web. While not yet listed at the time of writing, there is a high probability that Integris will appear on Hunters International DLS in the future.
Conclusion
The threat actors likely began their malicious activities in 2017 (or earlier) and are still active. While there may be a connection to Nigeria, it’s also possible that Hunters International adopted a fake identity/persona.
IOC
TOR Domain
==========
hunters55rdxciehoqzwv7vgyv6nt37tbwax2reroyzxhou7my5ejyid.onion
hunters55atbdusuladzv7vzv6a423bkh6ksl2uftwrxyuarbzlfh7yd.onion
hunters33dootzzwybhxyh6xnmumopeoza6u4hkontdqu7awnhmix7ad.onion
hunters33mmcwww7ek7q5ndahul6nmzmrsumfs6aenicbqon6mxfiqyd.onion
Email Addresses
===============
oyewolelawrence@gmail.com
cacmountofvictory@gmail.com
Surface Web Domain: huntersinternational.org
IP:193.106.175.48
ASN: AS50465
Domain Fingerprint (SHA256): 48b0a224697ead43ca1272c34a4777662049964913f083a40a5458a4ee1f78a6
Soon after I posted about my quick finding in Twitter and LinkedIn, the DLS was not reachable. This may have been a result of my posts, or the group may have disconnected to load a new batch of victims.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







