4 min read
Red CryptoApp: A New Threat Group in the Ransomware World
This is a preliminary report based only on the data leak site (DLS), listed victims, and other observed patterns. A detailed investigation will...
KEEP READINGRakesh Krishnan is a Senior Threat Analyst at Netenrich. Passionate in Cyber Security and conducts OSINT Investigations on Cyber Incidents.
Rakesh's top published blogs:
ALPHA Ransomware launched DLS:
https://medium.com/coinmonks/alpha-ransomware-launched-dls-9812b502e6a2
Discovering ADHUBLLKA Ransomware Family:
https://medium.com/coinmonks/discovering-adhubllka-ransomware-family-tracing-roots-of-lolkek-bit-obz-u2k-tzw-variants-ce77d2461ac7
FRAUDGPT: THE VILLAIN AVATAR of CHATGPT:
https://medium.com/coinmonks/fraudgpt-the-villain-avatar-of-chatgpt-f5c9c9f70f2a
SBI YONO PHISHING SCAM: Criminals Collecting User Information:
https://medium.com/coinmonks/sbi-yono-phishing-scam-criminals-collecting-user-information-4e479a17b6e1
CHASING CHAOS RANSOMWARE — Unveiling 2017 Instagram Hack Incident!:
https://medium.com/coinmonks/chasing-chaos-ransomware-unveiling-2017-belarus-hack-incident-82cf90547c10
4 min read
This is a preliminary report based only on the data leak site (DLS), listed victims, and other observed patterns. A detailed investigation will...
KEEP READING
5 min read
This article focuses on my research to uncoverthe identity of Hunters...

4 min read
Alpha ransomware, a distinct group not to be confused with ALPHV ransomware,...
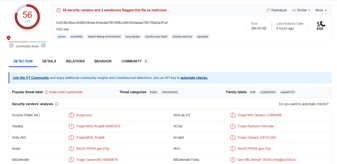
8 min read
This article is not an in-depth reverse-engineering analysis of a ransomware...
2 min read
With the rise of generative AI models, the threat landscape has changed...
2 min read
Jul 25, 2025 by Michael Beavers
Most security operations centers struggle with scale, complexity, and context....
1 min read
Jul 20, 2023 by Netenrich
Netenrich has entered into a strategic partnership with Cybriant, a leading ...
4 min read
Jul 18, 2023 by John Pirc
To keep an enterprise up and running, security is essential—and no doubt, why...
2 min read
Apr 8, 2025 by Netenrich
Google Cloud Next ‘25 is where innovation in the cloud takes center stage,...
8 min read
Feb 20, 2025 by Netenrich
The Chief Information Security Officer (CISO) role has transformed from being...
4 min read
Sep 17, 2024 by Raju Chekuri
Traditional SIEMs just aren’t cutting it anymore. They rely on outdated,...
9 min read
Nov 12, 2025 by Netenrich
Cyberattacks rarely begin with masterful exploits. They start with small...
8 min read
Nov 11, 2025 by Netenrich
On a regular Monday morning, Maya, an SOC lead, logs into her company’s asset...
7 min read
Nov 11, 2025 by Netenrich
Security Operations Centers (SOCs) are busier than ever. However, are they more...

















The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
