Red CryptoApp: A New Threat Group in the Ransomware World
Published on April 3, 2024 | Last updated on July 31, 2025 | 4 min read

This is a preliminary report based only on the data leak site (DLS), listed victims, and other observed patterns. A detailed investigation will require samples not yet publicly available.
Red CryptoApp is a new ransomware group that emerged in March 2024.
At present, they have published the data of 11 victims on their DLS and announced one victim. Their DLS first appeared on March 29, 2024, under the title “Wall of Shame.”
33zo6hifw4usofzdnz74fm2zmhd3zsknog5jboqdgblcbwrmpcqzzbid.onion
It is notable that unlike other ransomware DLSs, Red CryptoApp did not use a vanity Onion domain.
In the image below, it’s clear the group leaked the data of all 11 victims on the same date, March 5, 2024. This suggests the group may have kickstarted their operations a while back, but waited for an optimal time to publish all victim data together to make a bigger splash and gain more attention in the ransomware community.
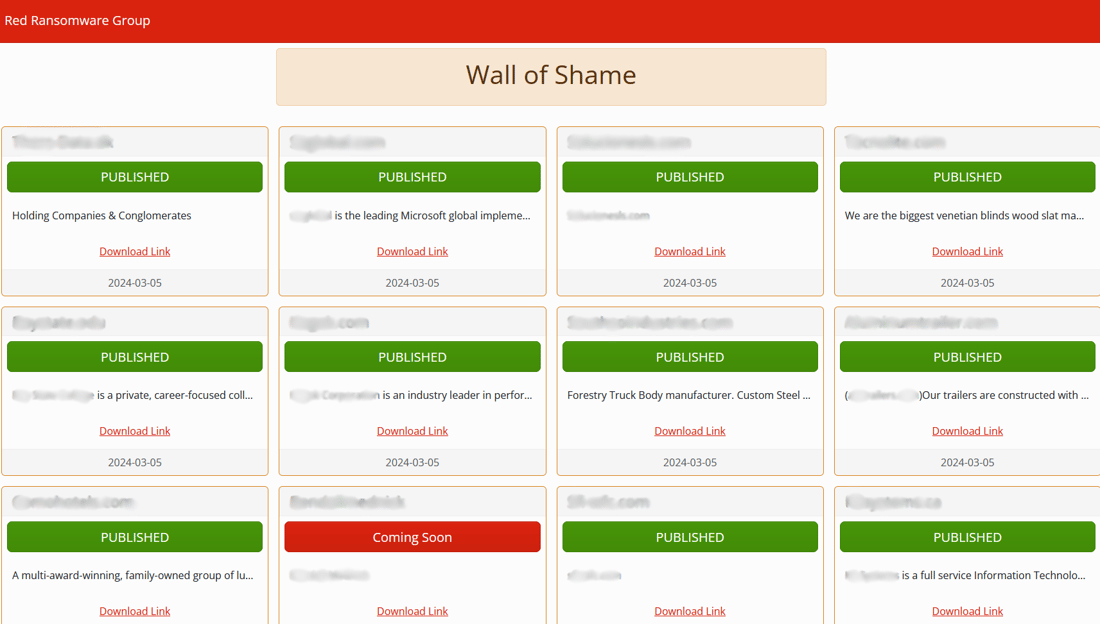
Once infected, all files are appended with .REDCryptoApp extension.
Based on my investigation of the victim files, the group likely began to target its victims in mid-February 2024. To note: The ransom note is dated February 18, 2024. It is also likely the group started to ramp up their activities in early 2024, and it leaked victim data in March 2024.
Exploring the victim panel
Red CryptoApp provides victims with a unique TOR URL to negotiate with them. When navigating to the unique URL, the page appears as follows:
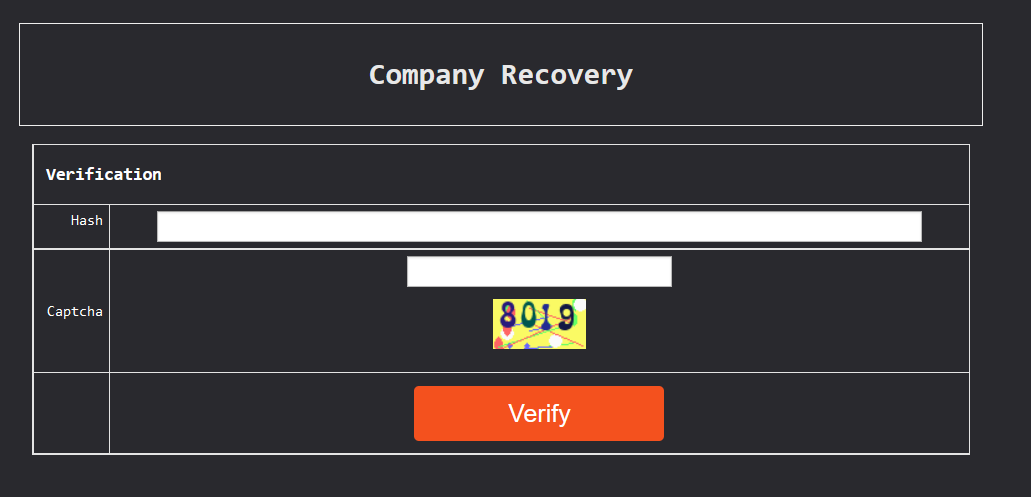
Titled “Company Recovery,” this page prompts victims to provide their “Hash” (a unique ID for each victim) and solve the captcha to log into the chat window.
NOTE: Each company victim is provided with a 64-alphabetic code.
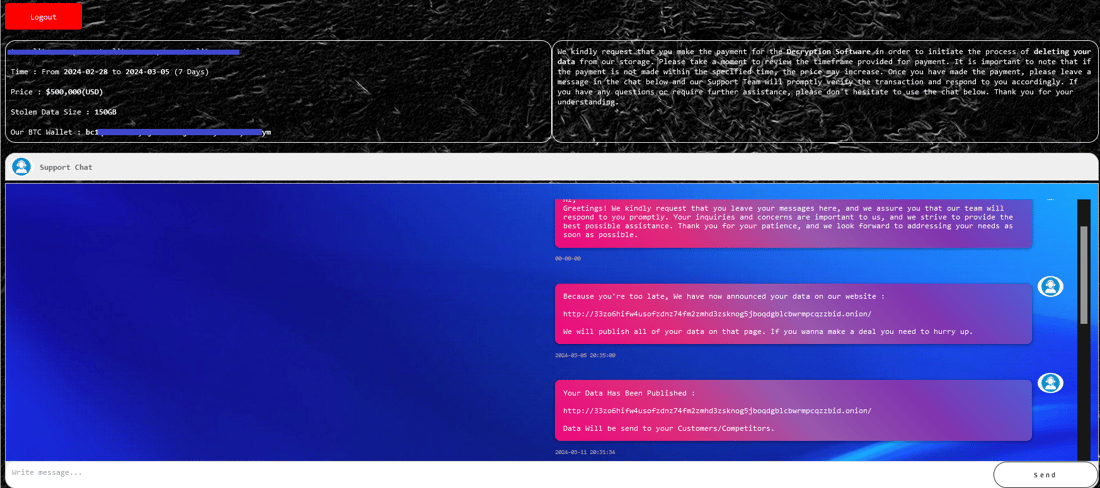
The left pane in the chat box displays the necessary victim information, including Victim Name, Timeframe for Negotiation, Ransom Demand, Data Size and Bitcoin Wallet Address. In this case, there is a ransom demand of $5 million to an undisclosed victim.
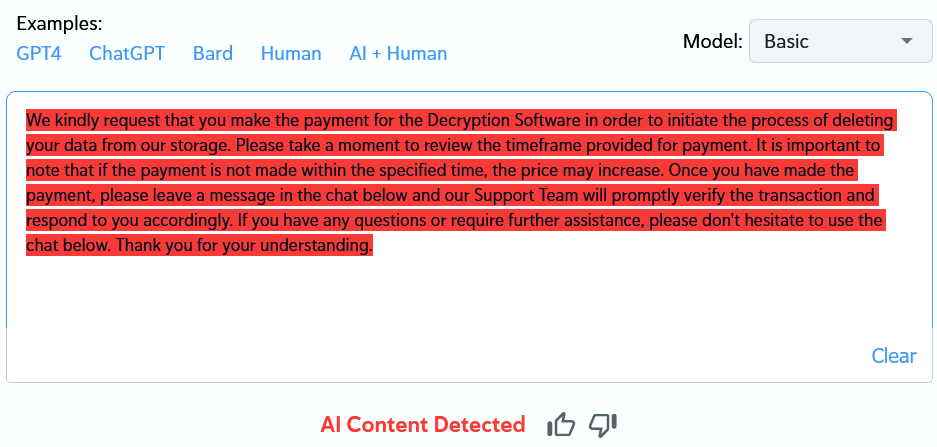
In analyzing the text in the right pane, I found it was AI-generated. This serves as concrete evidence that ransomware groups use AI tools.
Victim analysis
Based on analysis of victim information, we can deduce the following:
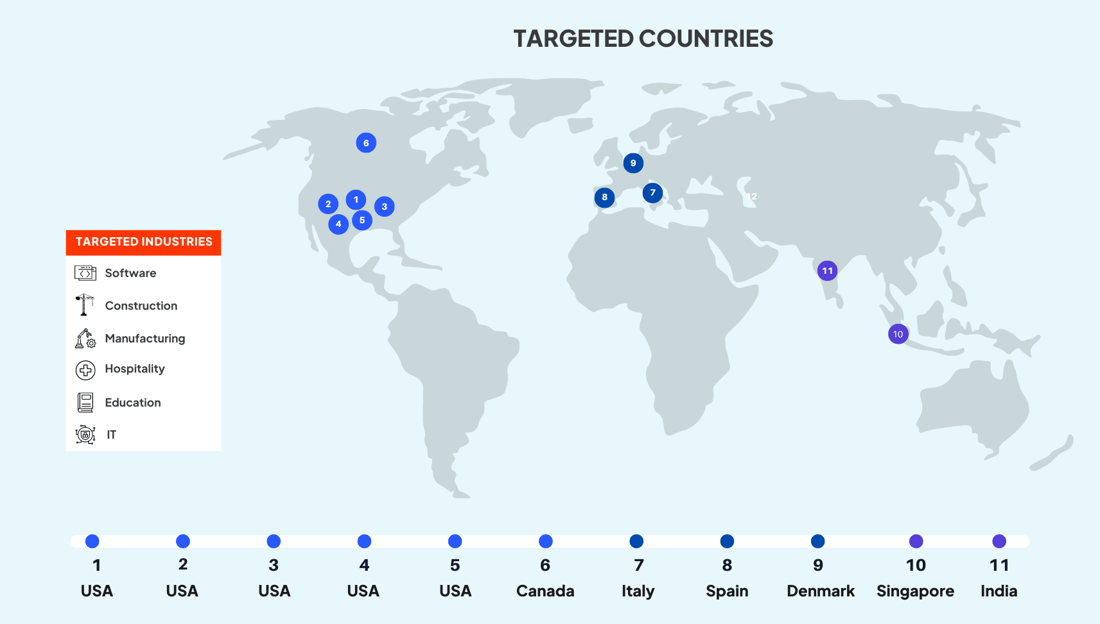
- At the time of writing (ATTOW) and with five total victims, the United States is the most targeted country.
- Other country targets include Denmark, India, Spain, Italy, Singapore, and Canada.
- The most targeted industries are software and manufacturing.
- Other observed targeted sectors include education, construction, hospitality, and IT.
Breach analysis
The Red CryptoApp group maintains two TOR domains. It is using one dedicated TOR domain to host leaked victim data and as of now, the second (below) to host the breached data of the 11 victims:
q7uspeblxi35hfd4jzy5evyz7ipjqtezww7giejgwpp5xdnjwxk5sdad.onion
All victim data is in a folder named “Dataprojects” archived as ZIP along with each victim name.
Ransom note analysis
Below is the ransom note used by the Red CryptoApp group to exfiltrate more information.
Attention!
----------------------------
| What happened?
----------------------------
We hacked your network and safely encrypted all of your files, documents, photos, databases, and other important data with reliable algorithms.
You cannot access your files right now, But do not worry You can get it back! It is easy to recover in a few steps.
We have also downloaded a lot of your private data from your network, so in case of not contacting us these data will be release publicly.
Everyone has a job and we have our jobs too, there is nothing personal issue here so just follow our instruction and you will be ok.
Right now the key of your network is in our hand now and you have to pay for that.
Plus, by paying us, you will get your key and your data will be earse from our storages and if you want you can get advise from us too, in order to make your network more than secure before.
----------------------------
| How to contact us and get my files back?
----------------------------
The only method to decrypt your files and be safe from data leakage is to purchase a unique private key which is securely stored in our servers.
To contact us and purchase the key you have to get to the link below :
Onion Link :
http://33zo6hifw4usofzdnz74fm2zmhd3zsknog5jboqdgblcbwrmpcqzzbid.onion/XXXXXXXXXXXXXXXX/XXXXXXXXXXXXXXX/login
Hash ID : XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
!Important! : This is a unique link and hash for your network so don't share these with anyone and keep it safe.
----------------------------
| How to get access to the Onion link ?
----------------------------
Simple :
1- Download Tor Browser and install it. (Official Tor Website : torproject.org)
2- Open Tor Browser and connect to it.
3- After the Connection, Enter the Onion Link and use your Hash ID to login to your panel.
----------------------------
| What about guarantees?
----------------------------
We understand your stress and worry.
So you have a FREE opportunity to test a service by instantly decrypting for free some small files from your network.
after the payment we will help you until you get your network back to normal and be satesfy.
Dear System Administrators,
Do not think that you can handle it by yourself.
By hiding the fact of the breach you will be eventually fired and sometimes even sued.
Just trust us we've seen that a lot before.
----------------------------
| Follow the guidelines below to avoid losing your data:
----------------------------
!Important!
-Do not modify or rename encrypted files. You will lose them.
-Do not report to the Police, FBI, EDR, AV's, etc. They don't care about your business. They simply won't allow you to pay. As a result you will lose everything.
-Do not hire a recovery company. They can't decrypt without the key. They also don't care about your business. They believe that they are smarter than us and they can trick us, but it is not. They usually fail. So speak for yourself.
-Do not reject to purchase, Exfiltrated files will be publicly disclosed.
The group used a unique ransom note not found elsewhere. I can also confirm the note was written by a human and not AI-generated. However, a portion of the ransom note was found in a Maze ransomware note from 2020.
“Dear System Administrators,
Do not think that you can handle it by yourself.
By hiding the fact of the breach you will be eventually fired and sometimes even sued.
Just trust us we’ve seen that a lot before.”
The same note was seen in this tweet by the Maze ransomware group.
From this, we cannot conclude if this group is a spin-off of Maze ransomware, but more evidence could help co-relate the two groups in the near future.
Infrastructure analysis
The Red CryptoApp group is using Apache servers to power their DLS.
33zo6hifw4usofzdnz74fm2zmhd3zsknog5jboqdgblcbwrmpcqzzbid.onion
The threat actors also tried to disable response caching by setting the date Thu, 19 Nov 1981 08:52:00 GMT. This is a common method used by threat actors.
In analyzing the modified data, I found that this ransomware DLS has been active since December 2023.
The breach domain is powered with the following configuration:
Leak Site: q7uspeblxi35hfd4jzy5evyz7ipjqtezww7giejgwpp5xdnjwxk5sdad.onion
Server: Apache/2.4.58 running on Win64
Based on this, we can assume the group primarily uses a Windows machine and an Apache server.
Conclusion: more leaks from Red CryptoApp likely
Analysis of the victim list suggests Red CryptoApp has been operational since at least December 2023. The group has potential and may likely announce more leaks.
This is an ongoing investigation and developing story. We will provide updates as we have them. Subscribe to the Netenrich blog to stay tuned for the latest developments in the cybersecurity world.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







