Adaptive Cloud Security for
AWS Environments
The only service that correlates AWS cloud posture with real-time runtime signals to prioritize the risks that actually matter to your business.
Unifying Posture and
Runtime for AWS
Netenrich moves beyond static risk lists by correlating CNAPP posture findings with live runtime telemetry.
We transform raw AWS data into high-confidence security incidents with clear attack paths and automated response guidance.

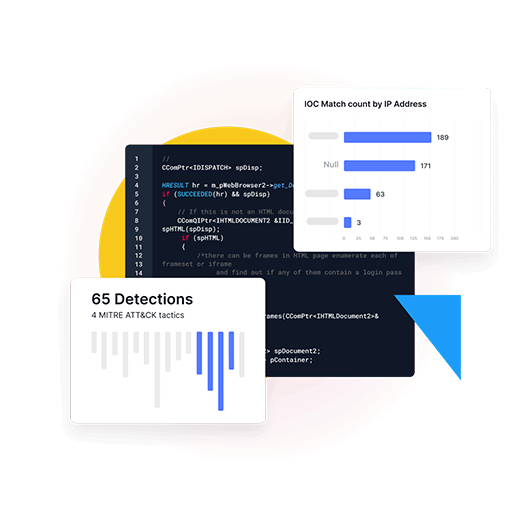
Adaptive Runtime CDR
Deliver 24x7 threat detection and response across identity, control plane, network, and workloads.
-
Continuous Ingestion Ingests AWS CloudTrail, VPC Flow Logs, EKS audit logs, and Lambda execution logs.
-
Behavioral Detection Detects account takeover, API abuse, and credential compromise.
-
MITRE ATT&CK Mapping Maps detections to cloud-relevant TTPs to surface real attacker behavior.
Adaptive CDR + Posture
Operationalizes cloud security posture by correlating configuration findings with live threat signals.
-
Evidence-Driven Prioritization Identifies misconfigurations that actively enable observed attack paths.
-
Posture Roadmap Focuses remediation on the 5-10 posture issues that materially reduce risk.
-
Critical Promotion Promotes findings to "critical" status when associated with live exploitation.
Built on Netenrich Resolution Intelligence Cloud™
Our proprietary platform is the engine of our service. It unifies security data, applies AI-driven analytics, and orchestrates autonomous response actions across your multi-cloud environment.
Evidence-Backed Verdicts
Uses Likelihood, Impact, and Confidence (LIC) scoring to deliver actionable incidents.
Situation Formation
Correlates logs into attack timelines, situational context, and blast radius analysis.
Vendor-Agnostic Ingestion
Seamlessly integrates and correlates findings from Wiz, Orca Security, and Google SCCE.
.gif?width=1152&height=698&name=Reacting%20to%20a%20stream%20of%20Isolated%20Alerts%20Old%20Way%20%26%20New%20Way%20With%20Netenrich%20RIC%20(1).gif)
What This Solves for AWS Teams
Targeting the most critical vectors in modern cloud environments.
Identity & Access Abuse
Detect credential compromise—the #1 cloud attack vector—by monitoring IAM role, policy, and AssumeRole activity in real time.
API & Control Plane Security
Stop account takeover and privilege escalation by monitoring AWS CloudTrail Management and Data Events for unauthorized API misuse.
Detection Coverage Confidence
Gain visibility into exactly which AWS assets are monitored and identify telemetry gaps or blind spots before attackers find them.
Outcome Delivery Model
Onboarding & Enablement
Log integration, entity mapping, and baseline activation of the detection engine.
Continuous Protection
24x7 monitoring, investigation, and automated containment playbooks for identity and resources.
Improvement & Maturity
Monthly detection effectiveness reviews, architectural recommendations, and executive risk reporting.
Ready for High-Confidence AWS Security?
Get SOC-ready narratives, full attack timelines, and actionable ActOns powered by Netenrich.
Frequently Asked Questions (FAQs)
-
1. What is an AI SOC and why does it matter for CISOs?
An AI SOC uses autonomous SOC automation to cut false positives, reduce analyst toil, and accelerate response, giving CISOs stronger visibility, control, and operational efficiency.
-
2. What’s the difference between Agentic AI SecOps and Autonomous Security Operations?
Agentic AI involves intelligent agents that reason, adapt, and coordinate across workflows; essentially the tooling, from a SecOps perspective. Autonomous Security Operations is the outcome: resilient, always-on security where AI handles the noise and analysts focus on what matters.
-
3. How does Netenrich AI-driven SOC automation improve security operations?
Netenrich’s AI-driven SOC automation eliminates alert fatigue by automating known threats, repetitive tasks, and triage.
-
4. Does Autonomous SOC replace my security team?
No. Autonomous SOC augments your SOC analysts by automating repetitive tasks so they can focus on strategic investigations and risk management.
-
5. How quickly can a CISO see value from Netenrich ?
Most organizations see measurable efficiency gains within weeks. Netenrich delivers rapid onboarding, automation of high-volume tasks, and early reduction in alert fatigue.
Work from a common operational view
Siloed security and digital ops leads to gaps and inefficient duplication of tools, processes, and people. Resolution Intelligence Cloud provides a common operational view and situational awareness aligned to business risk. And it facilitates collaboration within and between teams.
- Strengthen your security posture
- Improve performance and up time
- Boost analyst effectiveness
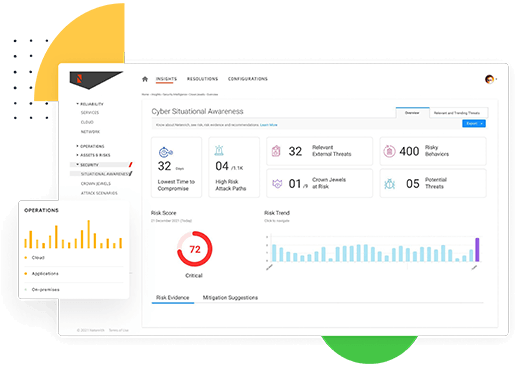
Out-innovate hackers with anomaly detection & situational awareness
Hackers are relentlessly innovative. It's futile to fight them with traditional, reactive methods.
- Identify unknowns without detection rules with advanced anomaly detection (think next-next-gen UEBA)
- Be proactive with actionable insights from data over time, correlated and mapped to the MITRE ATT&CK framework
- Identify and resolve what matters most to the business — stop wasting time on alert noise
- Communicate across functions and coordinate response fast