Outpacing Breaches: Why Continuous Security Validation and Alignment Win
Published on November 12, 2025 | Last updated on January 9, 2026 | 7 min read

Key Takeaways
- Continuous security validation and alignment mean always staying a step ahead, not just catching up.
- Automated validation and closed-loop fixes make risk manageable, no more panic when an alert hits.
- With Netenrich MDR, CISOs deliver real-time proof - not just reports - to auditors, boards, and customers.
Cyberattacks rarely begin with masterful exploits. They start with small lapses, a forgotten firewall rule, a disabled endpoint agent, an exposed cloud bucket. These gaps in control are quiet, ordinary, and easily overlooked. But left unchecked, they are the cracks that adversaries prize most.
What is missing? Continuous Security Validation (CSV) and Attack Surface, Controls (security controls), and Threats (ACT): operational disciplines that include ongoing technical validation and ensuring that the results of validation drive coordinated action across IT, security, compliance, and business domains, so that risk management and remediation efforts are not just technically sound but also strategically integrated and prioritized. CSV and ACT ensure that every security and risk response lines up with business and compliance goals, turning continuous validation findings into unified action across teams and processes. This alignment is what closes the gap between pure technical validation and real enterprise-wide risk reduction.
When organizations test defenses continuously in production, embedding remediation into everyday workflows, they move beyond occasional threat checklists to a state of ongoing, provable assurance, ready for compliance, crisis, and board scrutiny.
Why Continuous Security Validation and ACT are Mission-Critical for Modern Enterprises
Continuous security validation and ACT are emerging as the backbone of enterprise resilience. They continuously connect assets, controls, and threats in one loop, exposing posture drift and misaligned defenses in near real time. This allows CISOs to discover and remedy security control failures before they're exploited by attackers. In a world where the cost of each breach has skyrocketed to an average of $4.88 million globally, faith in stationary tools and periodic audits comes at a premium.
Most breaches are not due to missing technology but rather controls failing and misconfigurations.
- According to IBM, “human error, misconfigurations, and system glitches together were the root cause of breaches.”2
- More broadly, the Verizon report further states that the human element (misconfiguration, error, misuse of privilege) is present in 82% of breaches.3
- SentinelOne’s 2025 report data provides a cloud optic: 23% of cloud incidents stemmed from misconfiguration, and over one quarter of organizations suffered breaches from configuration errors.4

According to a 2025 report, most security breaches are due to failed controls and misconfigurations.
Pie chart of the root causes of enterprise breaches.
© Netenrich 2025
Meanwhile, the benefits of CSV and ACT stack up:
- Reduce Mean Time to Detect (MTTD): Regular testing surfaces control failures and exposures in mere minutes (hours), rather than in weeks or months.
- Boost Posture Visibility: Real-time visibility over drift, asset exposure, and misconfigurations leads to accurate and precise risk management, replacing speculation with data.
- Simplify Compliance: CSV exports live exportable compliance reports to meet the needs of regulators, auditors, and customers for evidence that is substantiated daily in concrete terms.
How Can CISOs Identify Gaps in Security Controls?
Almost all enterprise security portfolios still have blind spots despite massive investments. Verizon DBIR analysis finds that the vast majority of corporate breaches last year have mostly been triggered by errors, wrong settings, and process changes that are almost never detected post-incident.5
Common sources of exposure:
- The absence of a live, automated testing process: The latest control in existence will not survive until the next environment or application update. Cloud deployments, SaaS onboarding, DevOps refreshes, or changes may be ahead of quarterly reviews.
- Siloed reporting and feedback: People working in Security, IT, DevOps, GRC, and business units each have a complete set of inventories that are partial, sometimes outdated.
- Default, misaligned, or obsolete configurations: If you want to mitigate against this, mergers, staff changes, and remote work cause inadvertent risk as settings drift, privileged accounts live on, and temporary exceptions become permanent.
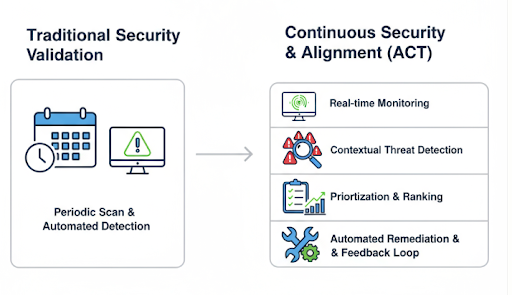
Continuous validation with ACT: real-time, contextual, prioritized
Diagram comparing periodic security checks to ACT, which adds real-time monitoring, contextual threat detection, prioritization, and automated remediation.
© Netenrich 2025
EasyJet: Lessons from Unchecked Void
A widely reported breach at EasyJet in 2020 demonstrates the perils of control failure and configuration drift in the airline sector. In this instance, attackers accessed sensitive customer information through a flaw in the airline’s cloud app and storage environment. Investigations into the incident indicated that misconfigurations and weaknesses in continued security validation in the cloud contributed to the exposure. The breach exposed about 9 million customer records - such as email addresses and travel information - and led to extensive regulatory scrutiny with the UK Information Commissioner’s Office, along with reputational and remediation costs.
If EasyJet had been applying continuous security validation - automated testing, real-time monitoring of storage access, and frequent fixing of misconfigurations - the company could have found and patched the exposure in hours rather than months. Businesses using CSV have found themselves spotting a gap earlier, starting closure workflows quickly, and being less likely to suffer lengthy incidents and regulatory issues as a result, industry analysts say.6
What Tools Help Validate Security Defenses?
Today, security defenses cannot depend on static controls or audit records for periodic threat analysis. Today's threat landscape has ushered in a new era for automated testing. Breach and Attack Simulation (BAS) and Adversarial Exposure Validation (AEV) are among potent, real-time solutions for enterprises willing to continuously test and improve their ability to withstand and defend against these breaches.
- BAS Platforms accurately simulate tactics, methods of operation, and procedures (TTPs) of advanced attackers.
- BAS tools, such as SCYTHE, SafeBreach, AttackIQ, Pentera, and Google Mandiant, test existing security controls on simulated attacks within an organization’s ecosystem. Instead of theoretical coverage or assumptions, these solutions perform the same exploits, lateral movements, and privilege escalation techniques as the real threats do.
They show, in real time, whether security investments are effectively stopping the threat or not, if they will fail in a realistic emergency.
Adversarial Exposure Validation (AEV) platforms expand upon this approach by augmenting the testing context with an even wider risk context.
- AEV doesn’t simply automate red-teaming or penetration testing-it's a continuous audit of the evolving attack surface that adapts to changes in business risk, asset inventories, and external threat intelligence.
- Every time it’s updated, whether it’s a new integration with the cloud, deployment of a software product, or new real-world attack data, AEV recalibrates its validation processes.
Several AEV services tie testing efforts back to frameworks, like MITRE ATT&CK, which guarantees controls are perpetually evaluated toward the most pertinent and quickly changing behaviors of adversaries.
Together, BAS and AEV move Enterprise Security from “set and forget” to an always-on, evidence-driven assurance cycle.
Rather than sitting around waiting for the next audit or the next surprise, organizations receive continuous actionable feedback that allows their security, operations, and executive teams to identify exposures in real time and then get them on the right track. Leading industry analysts [e.g., Gartner, Forrester] view these kinds of tools as critical for organizations to future-proof their security program for tomorrow’s change-driven environment.
Table: Top BAS/AEV Capabilities for Enterprises
| Capability | Value |
|---|---|
| Automated Testing | Discover issues within hours |
| Actionable Reporting | Track remediation, not just alerts |
| SIEM/XDR Integration | Expedite resolution from detection |
| MITRE ATT&CK Mapping | Align with real-world attacker methods |
Automated validation platforms provide persistent, actionable responses to the effectiveness of their enterprise controls
Table summarizing BAS and AEV values in enterprise defense
© Netenrich 2025
NOTE: All reference tools are industry-endorsed and approved by industry analysts and are not a public source.
But, while standalone BAS and AEV provide significant advantages, what leaders in most organizations need is integration: a controlled, feedback-rich approach that directly connects detection to remediation, supported by the ability to report the results. While standalone validation tools are powerful, their true value is unlocked when their findings are integrated directly into a detection and response workflow. This is precisely the gap Netenrich Adaptive MDR is designed to fill.
How Does Netenrich MDR Provide Ongoing Validation?
Netenrich Adaptive MDR provides validation by means of a holistic solution integrating real-time detection, sophisticated threat emulation, and automated remediation. Unlike static review processes, its model is integrated right within enterprise workflows, so each critical stage from detection to closure is both continuous and auditable.
Unified telemetry. It begins with massive streams of telemetry being ingested from the entire security and operations stack. It also provides signals received from endpoints, networks, cloud, and SaaS environments through which all of those signals are aggregated in a single analysis pipeline. By synthesizing these disparate data sources, the system can monitor enterprise posture on an ongoing basis, identifying even small changes or deficiencies that are not visible.
Cloud-native analytics and attack simulation. Next, Netenrich harnesses cloud-native analytics and artificial intelligence to run real-time attack simulations and locate gaps. Such simulated adversary tactics look for weak points in identity management, device status, cloud permissions, and in the larger organization’s supply chain footprint. Continuous and adaptive testing can result in proactive defenses against evolving threats, identifying configuration drift, or decay before it can be exploited. By automating the validation of known configurations and controls, Netenrich frees analysts from repetitive checks so they can focus on novel threats and strategic posture improvements.
Closing gaps with automated remediation. When a potential gap or failure occurs, the answer does not end with a warning, but rather closes a hole, strengthens the cybersecurity defense against attacks, and moves into a broader attack arena. It is automatically integrated with other ticketing and engineering systems, such as Jira. A failed control or found drift immediately initiates the creation and issuance of a resolution task that is assigned to the relevant team or stakeholder directly. This integration ensures visibility and prompt accountability, and reduces the time lag between detection and remediation - attacking concerns while they are small and easily correctable.
Verified closure and compliance reporting. Finally, each closure itself is automatically verified and reported back to compliance and board dashboards. End-of-quarter evidence hunts or manual sums of fixes no longer need to happen. Rather, it is consistently recorded in real time so auditors and executives have proof of action and not after-the-fact reassurance. In this new model, compliance transforms from a periodic checkbox exercise into a strategic enabler, giving the organization constant, provable evidence that its defenses are effective and ready.
Netenrich orchestrates instant, automatic closure from detection to documentation
Feedback loop to issue feedback over ticketing and remediation in MDR
© Netenrich 2025
What Are the Results of Continuous Testing?
Continuous testing in today's security programs is measurable. The impact of continuous testing is transformative, leading to measurable reductions in breach rates as organizations identify and remediate misconfigurations before attackers can exploit them.
Automation and recurring validation cycles not only greatly narrows the MTTD (mean time to detect) and MTTR (mean time to respond) to threats, but also can often cut incident response time from days or weeks to a mere few minutes or hours.
Continuous testing has one of the most significant benefits, which is that it can turn learning from an incident into preventive security measures. Instead of root cause analysis taking place only once the damage has been caused by a crisis, organizations can identify issues and weaknesses in their control environment beforehand as part of their daily routines. Automated testing uncovers these deficiencies early, enabling incident learnings to be captured, written into playbooks, and performed as part of day-to-day actions.
Brand reputation and regulatory exposure are also immensely enhanced. By surfacing failings long before the media or an external regulator does, organizations avoid the high costs – financial and reputational – of public breaches. In an age when one security mishap can lead to a wide range of distrust, and potentially liability and PR damage in the eyes of potential customers, persistent validation is an operational safety net to ensure that the organization’s credibility and stakeholder confidence stay the same.
Ultimately, continuous validation further empowers CISOs and risk leadership to provide board-ready, data-driven reporting without the same ambiguity that the past was known for. Rather than theoretical coverage or self-attested compliance, continuous security validation empowers CISOs to change the conversation with the board.
The question is no longer “Are we safe?” but rather “Here is the evidence of how we are measurably safer and more resilient than we were last quarter.” This shift from hopeful assurance to provable resilience is the future of enterprise security.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.








