Discovering the ADHUBLLKA Ransomware Family: Tracing the Roots of LOLKEK, BIT, OBZ, U2K, TZW Variants
Published on August 24, 2023 | Last updated on December 18, 2025 | 8 min read
This article is not an in-depth reverse-engineering analysis of a ransomware variant. Rather, it discusses the methods and different techniques used to uncover previous ransomware campaigns.
When a ransomware is successful out in the wild, it is a common to see cybercriminals use the same ransomware samples — slightly tweaking their codebase — to pilot other projects. For example, they may change the encryption scheme, ransom notes, or command-and-control (C2) communication channels and then, re-brand themselves as a “new” ransomware.
These slight tweaks can confuse security researchers during the classification process. It is important to attribute the observed/detected indicators of compromise (IOCs) to the respective malware/ransomware. However, because the newly re-branded names are also tied to the old malware, it can create duplicates, in some instances.
As a result, analysts/researchers can hit a roadblock while investigating for an IOC hash if they see multiple malware families bond to an uploaded sample. For example, when someone leaked Babuk ransomware code, a plethora of new ransomware, such as Rorschach, Mario, ESXi, RTM Locker, and more, were quick to appear on the scene. The same happened when Conti source code was leaked. In these cases, confirmation often requires reverse engineering.
In this research, we tracked down a similar case.
Case study: ADHUBLLKA ransomware
In August 2023, a new ransomware strain (Filename: r.exe) caught our attention. Our analysis showed that the newly found ransomware, active since August 1, 2023, is a spin-off of an earlier variant called ADHUBLLKA ransomware, which first appeared on January 13, 2020.
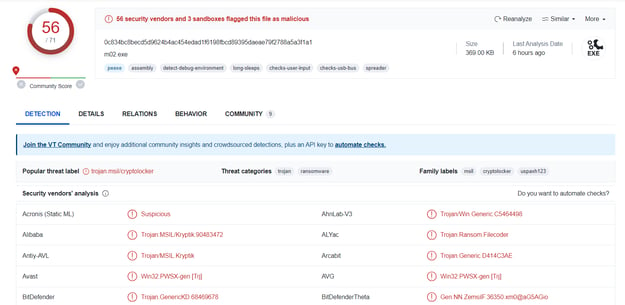
In VirusTotal, you can find the following information on this case (MD5: 0f77484639b1193ad66e313040c92571b):
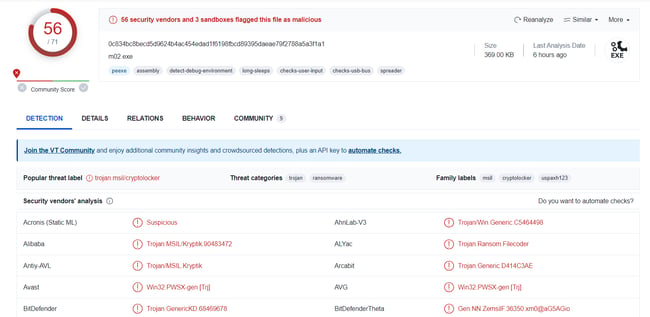
Multiple engines have already detected this ransomware and by tracking its genealogy, we find traces of CryptoLocker, which has been prevalent since 2016. Since many of the malware code bases get an exact match, we can’t conclude it is CryptoLocker. Instead, we must look at additional parameters, like contact emails, ransom notes, and execution method, as these all play a vital role in analysis.
The ransom note reveals several important details.
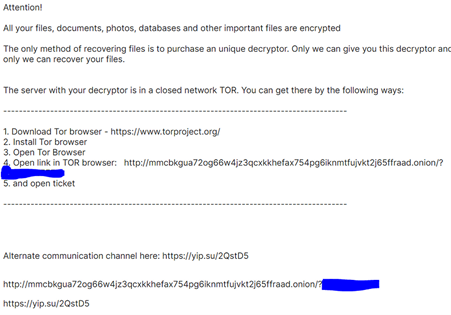
The threat actor asks victims to communicate via a TOR-based victim portal to obtain decryption keys following ransom payment.
TOR Address: mmcbkgua72og66w4jz3qcxkkhefax754pg6iknmtfujvkt2j65ffraad.onion
Alternate communication channel: https://yip.su/2QstD5
Diving deeper into the Dark Web, we can extract more information about the negotiation phase.
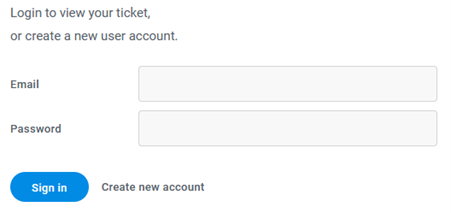
mmcbkgua72og66w4jz3qcxkkhefax754pg6iknmtfujvkt2j65ffraad.onion
The ransomware group advises infected victims to contact them directly and open a ticket for further negotiation, such as sample file submission, payment negotiation, and finally, receiving the decryption keys post payment.
Once the ticket is submitted, a channel is created on the fly and this default message automatically pops up:
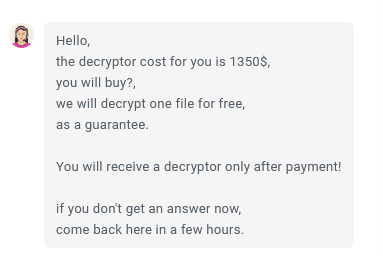
As evidenced with this correspondence, the ransomware operator appears unwilling to negotiate, holding firm on the initial demand for decryption keys.
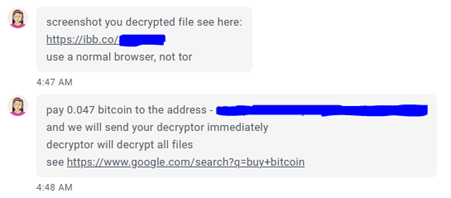
The operator would not provide a decrypted sample screenshot to the victim directly, but instead, provided one on ImgBB, an image hosting service. This confirms there is a working decryptor present with the group.
Communicated IPs
104.18.14.101
20.99.184.37
192.229.211.108
23.216.147.61
Decryption Key Cost: $1350 or 0.047BTC
NOTE: To clear his/her tracks, the threat actor could delete the message sent to their victims as well as any created tickets once they are resolved.
File execution
The file is named “r.exe”. Once executed, it begins to launch malicious tasks, such as process injection or dropping a malicious executable (AddInProcess32.exe) in a victim environment and initializing the infection chain. All files will be encrypted with “.MMM” extensions appended to the affected files.
All the encrypted files contain the string “CRYPTO LOCKER” along with the encrypted gibberish text.
![]()
To explore further, you can refer/analyze the sample file from this Joe Sandbox Report.
Tracing the ransomware family
While tracing this ransomware sample, you must consider a few parameters, such as sample, ransom note, and email addresses, to find the ransomware root.
It’s clear this is not limited to a single family. A genealogy can be found here:
ADHUBLLKA (DEATH RANSOM) — > BIT — > LOLKEK — > OBZ — > U2K — > TZW
Here is a listing of the hashes observed in the wild for each variant with timeline:
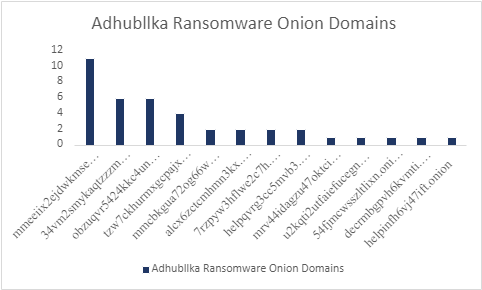
This graph shows the top infected/supplied ransom notes, where the victims are asked to contact the TOR domain address.
All the v2 Tor Onion links now are defunct.
Ransom note analysis
Here, we can analyze a few ransomware notes from different variants that dropped ransom notes onto victim computers.
2019 Variant
Attention!
All your files, documents, photos, databases and other important files are encrypted
The only method of recovering files is to purchase an unique decryptor. Only we can give you this decryptor and only we can recover your files.
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
Alternate communication channel here: http://helpqvrg3cc5mvb3.onion/
2022-23 Variants
Attention!
All your files, documents, photos, databases and other important files are encrypted
The only method of recovering files is to purchase an unique decryptor. Only we can give you this decryptor and only we can recover your files.
Alternate communication channel here: https://yip.su/2QstD5
U2K Variant
Attention!
All your files, documents, photos, databases and other important files are encrypted
The only method of recovering files is to purchase an unique decryptor. Only we can give you this decryptor and only we can recover your files.
The server with your decryptor is in a closed network TOR.
TZW Variant
Attention!
All your files, documents, photos, databases and other important files are encrypted
The only method of recovering files is to purchase an unique decryptor. Only we can give you this decryptor and only we can recover your files.
The server with your decryptor is in a closed network TOR.
The above ransom notes indicate that the group has changed their communication channel from v2 TOR Onion URLs to v3 TOR URL. This is because the TOR community deprecated v2 Onion domains.
It is important to note that an additional sentence — “The server with your decryptor is in a closed network TOR.” — can only be seen in two new variants: TZW and U2K.
Additionally, the notes show that the group also used a URL shortener service to redirect to a Freshdesk ticketing site.
Expanding https://yip.su/2QstD5 leads you to a Freshdesk support site, bit7.freshdesk.com.
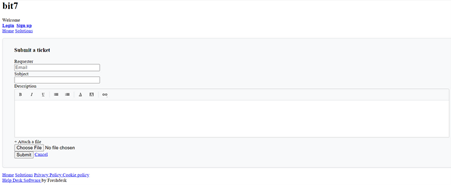
Further investigation revealed that this link (bit7.freshdesk.com/support/tickets/) appeared on December 27, 2019, in Pastebin, which is used by U2K Ransomware, a 2022 variant of ADHUBLLKA ransomware.
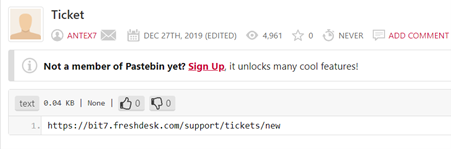
The newer variant of ADHUBLLKA ransomware, U2K, used the Freshdesk ticketing tool to communicate with its victim, confirming that the Freshdesk ticketing tool was active for last three years, but is no longer available.
By checking the profile of Antex7, we can see there are three pastes from this profile, where the other two pastes have the IP address listed as 192.3.157.96:3306, which is associated with LimeRAT.
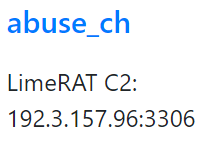
When the short URL: yip.su/2QstD5 was again loaded at another timeline (2022), this message appeared:

This signifies that the threat actor is maintaining a direct line of communication via email filessupport@cock.li for victims in case the TOR site goes down or the ticketing service is cancelled.
It is also important to note that this email address has been seen with multiple ransomware variants at different timelines, which seems to prove that the threat actor(s) have been the same since 2019.
URLs used in each Ransomware Projects
=====================================
alcx6zctcmhmn3kx.onion: JOPE,DeathRansom
decrmbgpvh6kvmti.onion: DOCM
helpinfh6vj47ift.onion: DOCM
7rzpyw3hflwe2c7h.onion: ADHUBLLKA, Bit
54fjmcwsszltlixn.onion: Bit
24cduc2htewrcv37.onion: Bit
helpqvrg3cc5mvb3.onion: Bit
mmeeiix2ejdwkmseycljetmpiwebdvgjts75c63camjofn2cjdoulzqd.onion: MME, GlobeImposter XLS, Bit, Lolkek
mmcbkgua72og66w4jz3qcxkkhefax754pg6iknmtfujvkt2j65ffraad.onion: Lolkek
mrv44idagzu47oktcipn6tlll6nzapi6pk3u7ehsucl4hpxon45dl4yd.onion: Bit,
yip.su/2QstD5: MME, OBZ,
Why ADHUBLLKA?
ADHUBLLKA is chosen as an anchor point due to the large number of reports covering the same email address pr0t3eam@protonmail.com, which belongs to the ransomware group and the sample spotted (MD5: 77d0a95415ef989128805252cba93dc2) in 2019, which still has relevancy with the 2023 variant.
Moreover, DeathRansom’s note and contact emails (which contain “death” as a main keyword) are different from ADHUBLLKA. This is despite the fact that it uses ADHUBLLKA as the extension after encrypting the files in a scenario. However, PCRisk confirmed that the group behind ADHUBLLKA ransomware had updated its version where TOR support exists and “.readme” extensions are added to the encrypted files instead of ADHUBLLKA. It is also notable that Lolkek samples encrypt the file with the “.readme” extension. Hence, we can classify them as an ADHUBLLKA variant.
NOTE: It can be considered as LOLKEK ransomware, but because it appeared after ADHUBLLKA (comparing timelines), the roots are traced to the ADHUBLLKA family.
In another instance, the older onion address alcx6zctcmhmn3kx.onion is associated with DeathRansom, which indirectly links to ADHUBLLKA ransomware. This hash 860b89a4138f744adbe41cee1de0848f was identified in May 2019 and categorized as ADHUBLLKA.
Confusion with GlobeImposter
The above discussed ransomware sample or other associated samples have also been tagged as GlobeImposter ransomware, which appeared in 2016. In various sandbox engines, it is still classified as GlobeImposter due to the code re-usage match parameter.
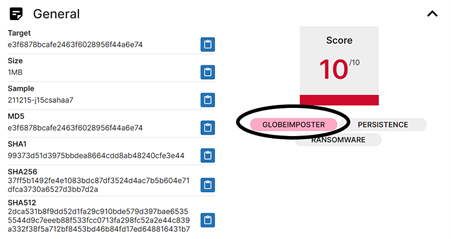
Here, we cannot classify it as GlobeImposter as the infection chain and method of ransom negotiation are different from the current active scenario.
In the case of GlobeImposter, there are a large number of encrypted file extensions used (instead of using single extension) and the emails/TOR domains used by threat actors do not overlap with any current ransomware campaigns.
Even if they have changed their modus operandi by changing their toolset or improvised their method of Dark Web communication, we can still consider this as part of the ADHUBLLKA (DeathRansom) family, as the same (observed tactic) is ongoing and has not come to an end since 2019.
Key points
- This ransomware strain, which targets individuals and small businesses, demands ransoms in the range of $800 to $1600 from each client. This is evident from previous variants.
- ADHUBLLKA is also seen in various other cyberattack campaigns. Popular threat actor group TA547 used ADHUBLLKA variants in their campaigns targeting various sectors of Australia in 2020.
- All the malicious files of the ADHUBLLKA ransomware variants are commonly file-named with their MD5 or SHA256 hash names, such as “MD5.vir” or “SHA256.bin”.
- The infected filenames (䶲䶮䶴䷣䷭䷢䷡䷠䶳䷠䷟䷞䷆䷩䷢.exe) are in Mandarin.
- TZW is the final variant that has appeared (as of now) from the ADHUBLLKA ransomware family. It also uses the same portal for victim communications.
- We can see that this ransomware was active for a long while on the Dark Web before the release of version 3 Onion URLs, as version 2 URLs were also used in earlier infections.
- Currently, this Ransomware family has not announced any DLS (Data Leak Site) on Dark Web at this moment, but once it gets a strong foothold; their DLS can be expected in near future.
Conclusion: Despite different timelines and names, all variants belong to ADHUBLLKA ransomware family
This ransomware has been highly active since 2019 and with a few observed changes, notably the v3 TOR domain names and other parameters.
There are various other names assigned to the same piece, such as ReadMe, MMM, MME, GlobeImposter2.0, which all again belong to the ADHUBLLKA ransomware family.
In the future, this ransomware may be rebranded with other names; or other groups may use it to launch their own ransomware campaigns. However, as long as the threat actor does not change their mode of communication, we will be able to trace all such cases back to the ADHUBLLKA family.
ATT&CK MATRIX techniques
T1091: Replication through Removable Media
T1055: Process Injection
T1036: Masquerading
T1562.001: Disable or Modify Tools
T1497: Virtualization/Sandbox Evasion
T1158: Hidden Files and Directories
T1027: Obfuscated Files or Information
T1406.002: Software Packing
T1056: Input Capture
T1124: System Time Discovery
T1518.001: Security Software Discovery
T1057: Process Discovery
T1120: Peripheral Device Discovery
T1083: File and Directory Discovery
T1082: System Information Discovery
T1080: Taint Shared Content
T1091: Replication Through Removable Media
T1560: Archive Collected Data
T1573: Encrypted Channel
T1090: Proxy
T1486: Data Encrypted for Impact
IOC
MD5 hashes
==========
77d0a95415ef989128805252cba93dc2
e3f6878bcafe2463f6028956f44a6e74
2f121145ea11b36f9ade0cb8f319e40a
291bea114eb566d39f69d8c2af059548
e4e439fc5ade188ba2c69367ba6731b6
0f77484639b1193ad66e313040c92571
121f5beface8337c7105cc6a257a87ed
341c316be98f624f7321d198c5345bc9
1f640e3f37ec3b93c958c5910eb6a3e7
860b89a4138f744adbe41cee1de0848f
5990a32cddde5978959321237f9b0ee1
22dce5b7daed8cfb14aa9e8e7eed1d2f
43c89b8dc5f9cac3d143238ba74c9002
8ba537f8d00a73d6cc1cc5dffa566ed1
2c72015e22b53c215403979536bce826
e58b77e4de54b09be77c852436a904b6
fc9ca0a85e47088d25483dd47fba3244
d0c67160c740f62c25b0558e9563a824
5355cce5601f471579f6154708d87fd7
518a38b47292b1e809c5e6f0bb1858be
3e7591082b36244767c1b5393a44f846
71852d35ddc0e13d2d830fcf6d185171
ab8f0580cc0d74e0215e7de19515c8a6
55044ed5d04a20844fcedb17a3f5bb31
842d42bb052a77759c8f55d46021b2e0
1a7ddd5e16d0fc9c3969d1c63e5c6cda
a735ff10e359539181c1eca593091ee6
6953d6e1a2d8df8e0d2e76263e8b3115
29250c34e78857b17ee2576f68757d01
13d8c2f2cdf5f6208c3e999621019304
21dd14135e2dc4b22591ab35cf98b115
09d5701f1f4a6d50f9833fc78d3f2371
d14aab030b254bae3c6977c71cbc8a0b
a15419df02ffae775b6231dd77fd9c6f
ae3353674bf514175deda25b96496a83
de9d7afe742c551522bafb785c706f4f
0e5bd98bcf1ef9bef39f19f41e1aabfb
0148dc4f8a43b7fa1c31578f1a3c13bf
34b2b644c22861346ed07b4c7eeea7fb
da07dd4894c10fe94eba4f32ae4a57e6
IP Addresses
==========
194.85.61.76
109.70.26.37
8.209.75.209
47.91.93.231
47.75.127.193
5.101.49.142
91.239.235.200
20.80.129.13
23.35.69.10
23.35.69.32
23.35.69.35
23.35.69.42
23.35.69.48
23.35.69.66
162.0.235.197
13.107.4.50
162.159.129.233
162.159.130.233
162.159.133.233
162.159.134.233
162.159.135.233
20.99.184.37
192.229.211.108
104.18.14.101
23.216.147.61
23.216.147.64
13.107.4.52
20.190.160.17
20.190.160.20
20.190.160.22
20.99.132.105
40.126.32.133
162.159.130.233
162.159.133.233
162.159.134.233
162.159.135.233
20.99.184.37
192.229.211.108
104.18.14.101
23.216.147.61
23.216.147.64
13.107.4.52
20.190.160.17
20.190.160.20
20.190.160.22
20.99.132.105
40.126.32.133
Domains
==========
162.159.130.233
162.159.133.233
162.159.134.233
162.159.135.233
20.99.184.37
192.229.211.108
104.18.14.101
23.216.147.61
23.216.147.64
13.107.4.52
20.190.160.17
20.190.160.20
20.190.160.22
20.99.132.105
40.126.32.133
Contact emails
==========
Pr0team@protonmail.com
filessupport@onionmail.org
filessupport@cock.li
rick5@xmpp.jp : Jabber
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







