Exposing Alpha Ransomware: A Deep Dive into Its Operations
Published on January 29, 2024 | Last updated on December 18, 2025 | 4 min read
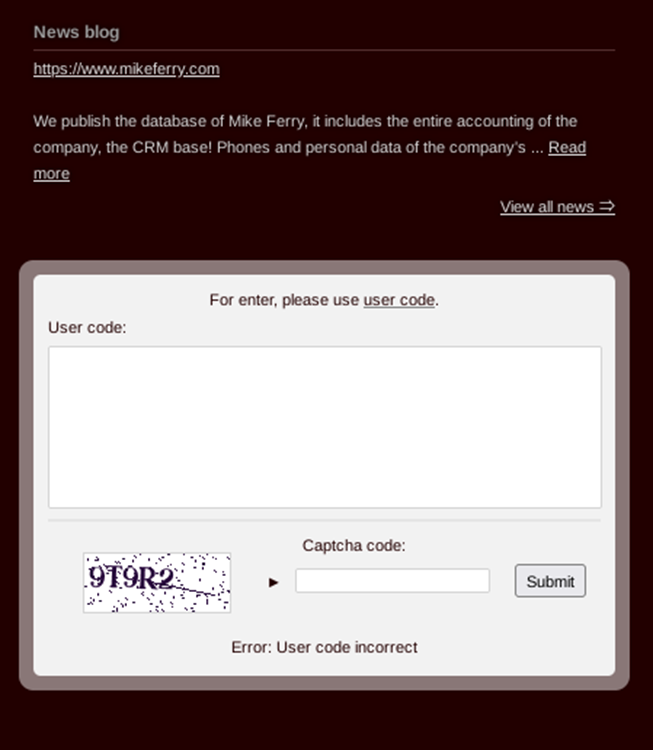
Alpha ransomware, a distinct group not to be confused with ALPHV ransomware, has recently emerged with the launch of its Dedicated/Data Leak Site (DLS) on the Dark Web and an initial listing of six victims’ data. As a developing story, I will continue to provide updates.
Generally, ransomware operators launch DLSs after a series of successful victimizations. Hence, we cannot assume their time of operation with the launch of DLS. It would be a few months before their DLS introduction. This also depends upon how effective the ransomware is in garnering victims at a faster rate. Here’s what I know so far.
Introduction: Alpha ransomware
Alpha ransomware, which first appeared targeting victims back in May 2023, came to my attention while I was checking the threat actor’s TOX ID, also active since May 2023.
At the time of writing, this ransomware is NOT prevalent. Its infection rates are lower than competitors and there is not yet an active sample out in the wild to analyze.
The only sample listed (but not yet recorded anywhere) is SHA1: c2b73063a4a032aede7dfd06391540b3b93f45d8.
Like other ransomware groups, Alpha appends a random 8-character alphanumeric extension to encrypted files, such as:
46140264-Readme.txt
79508AE9-Readme.txt
8C362A73-Readme.txt
E145AA52-Readme.txt
A75BE48B-Readme.txt
Analyzing Alpha group’s behavior
As an anchor point, let’s analyze the ransom note pattern.
During initial stages (May 2023), the group had not created a very compelling ransom note. As evidenced by the following, they had also either forgotten to include or not yet decided upon the name “Alpha”.
Your data have been stolen and encrypted.
Dont try to RECOVER, DELETE or MODIFY any files, this will make it impossible to restore.
We will help you in restoring your system, also decrypt several files for free.
You can contact us only via TOX messenger, download and install Tox client from: https://tox.chat/download.html
Add a friend with our TOX ID.
Our TOX ID: 98D120C9033653042E290627914B890A3291013F7377A976A028051C52440C71487D5F14DDA2
-----------------
Your personal decryption key:
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
With their next victim (June 2023), they revised the note to read:
Hello from Alpha Locker.
Your data have been stolen and encrypted.
Don't try to RECOVER, DELETE or MODIFY any files, this will make it impossible to restore.
We will help you in restoring your system, also decrypt several files for free.
You can contact us only via TOX messenger, download and install Tox client from: https://tox.chat/download.html
Add a friend with our TOX ID.
Our TOX ID: 98D120C9033653042E290627914B890A3291013F7377A976A028051C52440C71487D5F14DDA2
-----------------
Your personal decryption key:
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Still not satisfied, they once again revised the ransom note in November 2023, as follows :
-=-=-=- Alpha ransomware -=-=-=-
-=- Your data have been stolen and encrypted -=-
-=- You won't be able to decrypt them without our help -=-
-=- Dont try to RECOVER, DELETE or MODIFY any files, this will make it impossible to restore -=-
-=- We will help you in restoring your system, also decrypt several files for free -=-
-=- Contact us for price and get decryption software -=-
Note that this server is available via Tor browser only Follow the instructions to open the link:
mydatae2d63il5oaxxangwnid5loq2qmtsol2ozr6vtb7yfm5ypzo6id.onion
1. Type the address "https://www.torproject.org" in your Internet browser. It opens the Tor site.
2. Press "Download Tor", then press "Download Tor Browser", install and run it.
3. Now you have Tor browser. In the Tor Browser open mydatae2d63il5oaxxangwnid5loq2qmtsol2ozr6vtb7yfm5ypzo6id.onion
4. Copy your personal decryption key and paste it in the window that appears, enter the captcha and click the button submit.
5. Start a chat and follow the further instructions.
-----------------
Your personal decryption key:
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
After analyzing the encrypted extension, I found that the group had initially used only “random numbers” to append to the infected file. However, in later revisions, they switched to an “alphanumeric 8-character” extension.
This behavior, combined with the fact their newly launched DLS is unstable and frequently offline, shows the group to be relatively new and still in the process of setting up operations.
Exploring DLS
The Alpha ransomware group titled their DLS “MYDATA”. Based on behavior analysis, this name is not catchy and thus, will likely change.
For those interested, you can reach their Dark Web site at: mydatae2d63il5oaxxangwnid5loq2qmtsol2ozr6vtb7yfm5ypzo6id.onion
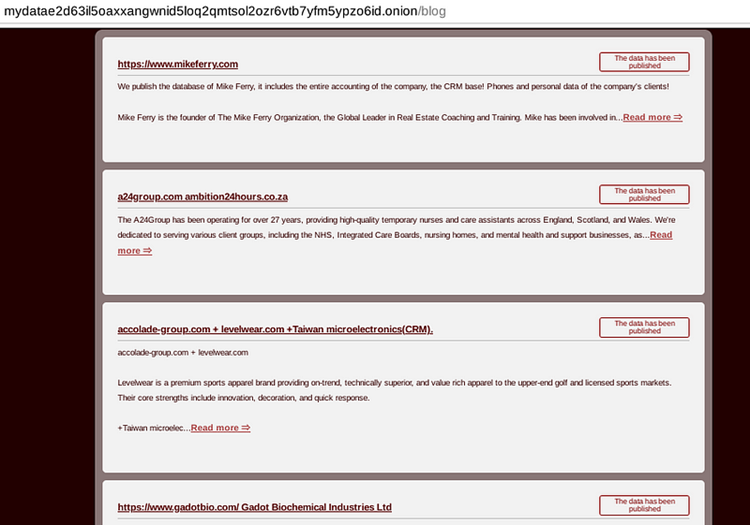
Alpha ransomware DLS
Now, let’s dig deeper into each functionality found in the Alpha panel.
To begin, the group uses a conventional approach to communicate with victims, providing them with a personal decryption key to log into the following panel, where all parties can initiate talks and directly negotiate the ransom.
Victim login prompt
After logging in, victims will see several options:
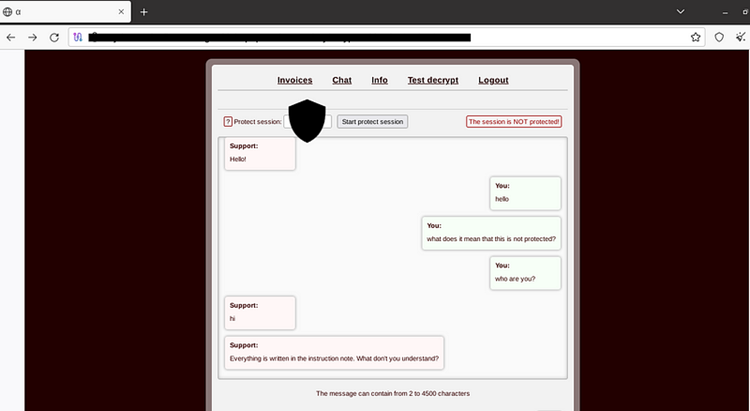
Victim panel for communication
If you look closely at the above screenshot, you’ll see the small Greek letter “Alpha” (α) on the tab as well as separate section names:
INVOICE, CHAT, INFO, TEST DECRYPT, LOGOUT
By generating a key between the victim and the threat actor, this panel also protects chat sessions.
Invoices: Allows victims to check their assigned ransom amount.
Chat: Enables negotiation with the Alpha group.
Info: Contains “How to” information.
Test decrypt: Allows victims to submit three sample files (less than 1MB) for decryption tests.
Logout: Ends the session.
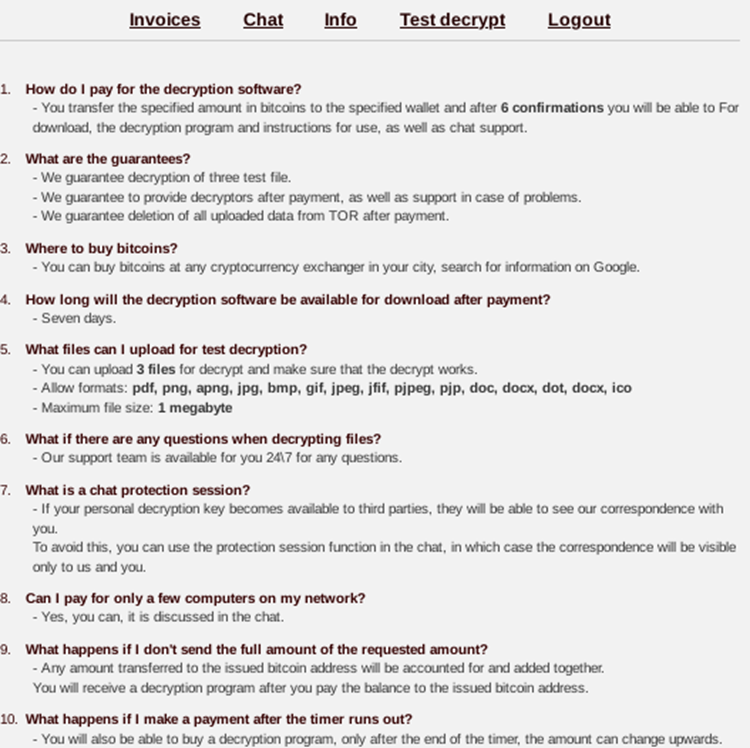
Info session in Alpha panel
It’s highly likely the Alpha group used Cloudflare Onion Service to add a layer of security to the hosted Onion domains.
While navigating to the data the group has leaked/published, I found that they maintain another TOR domain, exclusively to host the leaked resources.
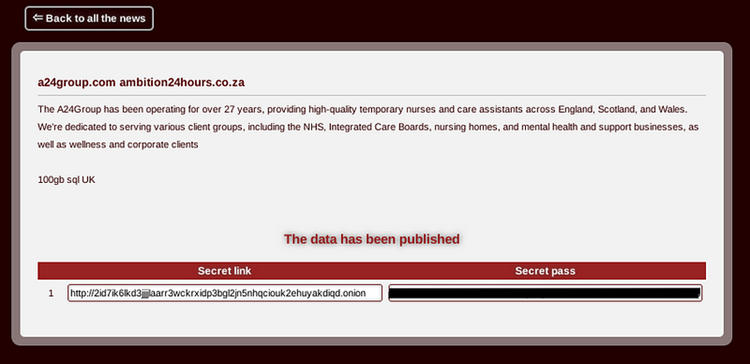
The victims’ list can be tracked at the following domain:
2id7ik6lkd3jjjjlaarr3wckrxidp3bgl2jn5nhqciouk2ehuyakdiqd.onion
For each victim, the group assigned a unique password to access the leaks under the same domain.
Victimization span numerous industry sectors
At the time of writing, there are six victims listed from the following locations:
2 victims from UK 🇬🇧
3 victims from US 🇺🇸
1 victim from Israel 🇮🇱
Affected industry sectors include: electrical, retail, biochemical, apparel, health, and real estate.
Threat actor details
My investigation uncovered the following:
TOX ID: 98D120C9033653042E290627914B890A3291013F7377A976A028051C52440C71487D5F14DDA2
Bitcoin Address: bc1qff2u797mrekxtcnr68p2gqarnjxvy575jug430
Ransom Demand: 0.2720BTC
Conclusion
Based on the panel and other factors, such as lack of consistency in its ransom demand, I believe the Alpha ransomware group is talented, but also amateurish in this space.
In the coming days, I’d expect more victims as the group becomes more visible, making headlines after collecting more digital footprints. Continued monitoring and analysis will be essential to better understand and mitigate the threat posed by this emerging ransomware variant.
UPDATE 1 (02/12/2024): EXPLORING FILE HOSTING
Earlier, the group used dedicated Onion domains for each listed victim, but has since moved away from this approach and adopted the OnionShare service to host compromised/leaked data.
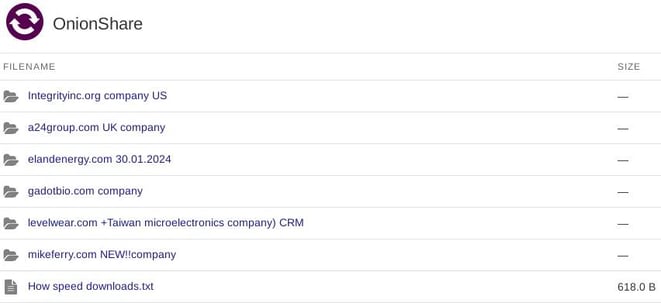
NOTE: OnionShare is an open-source tool that allows anyone to share files securely and anonymously and host websites.
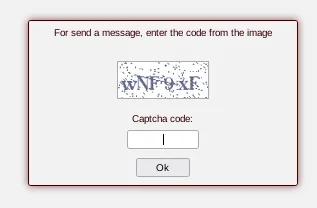
While communicating with Alpha members, I also found that to send each message (chat with Alpha), a Captcha verification is enabled to thwart any kind of automation from the visitors.
I also observed that the hosted contents are in a slow network. Hence, the download speed will be slower in the TOR network. However, Alpha members also advertised (via the following announcement) a high-speed, dedicated server, which promises faster downloads:
if you need a fast download. the price is 100 000$ for 1 company data. fix price.
you will get a dedicated server with fast internet connection
This signifies that the group is testing and evolving. Hence, we can expect more activities from Alpha in the coming months.
Read Rakesh's cybersec research and threat intel blog on Medium and follow him on LinkedIn.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.