Single Pane of Glass Gives a Clear View of Security Operations
Published on November 9, 2022 | Last updated on December 18, 2025 | 3 min read

Previous strategies in MITRE’s 11 Strategies of a World-class Cybersecurity Operations Center stressed the importance of collecting the right data — both threat intelligence (external) and log/sensor data (internal) — from the right tools.
While MITRE concedes that every tool and piece of data can add value, it also states that integration is crucial to deriving the most value. Thus, SOCs should look to bring all tools and data together into a single architecture that supports analyst workflow.
MITRE Strategy 8: Leverage tools to support analyst workflow
CHALLENGE: SOCs bring vast amounts of disparate data together into an information architecture. Analysts need to be able to quickly evaluate the data, turn the data into information, and use the information to fulfill their mission.
There is no one-size-fits-all workflow management solution. Depending on size and maturity, an organization may turn to:- A security orchestration, automation and response (SOAR) solution.
- A security information and event management (SIEM) platform.
- A combination of a SOAR and a SIEM.
- Or a mix of other threat detection and case management tools.
MITRE discusses at length the abilities, benefits, and shortcomings of several tools, but also states that “reducing the number of panes of glass and providing integration between them is the best strategy with an emphasis on automation and integration for repeated tasks, escalation, and incident handling.”
The goal is to provide analysts with information they can use immediately and effectively, without distracting or exhausting them, without requiring extensive training — and without busting budgets.
SOAR vs. SIEM vs. other tools: What pane of glass is the best pane of glass?
SOARs can integrate with a variety of disparate systems to collect threat data and automate repeatable processes. SIEMs can be used for threat detection and hunting, incident analysis, workflow and escalation, configuration monitoring, and more. Both are used as aggregation points for different tools and platforms.
So, why not choose one of these as the single pane of glass?
To begin, some traditional SIEMs have failed to deliver on their promises to increase visibility, enable the detection of security events, and support incident response. They don’t ingest all the data you need in a cost-effective, actionable, or timely way. Moreover, as MITRE points out, “Some SOCs struggle to realize the value proposition of SIEM, in large part due to their complexity, as effective correlation rule writing and upkeep can be resource consuming.”
For SOARS, it’s much the same story. Though they can integrate with other tools, it’s not easy to do so. Integration requires technical expertise to implement and manage. Plus, SOARs orchestrate a response. They don’t detect threats or determine where the greatest security risks to the business are.
Bottom line, SOARs and SIEMs require a deft, often cost-prohibitive touch to reap maximum benefits.
From a single pane of glass comes a common operational picture
Despite shortcomings of certain solutions, the notion of an aggregation point remains important — because perspective and visibility matter, visibility across all digital operations. And if fewer panes are better, wouldn’t that single pane of glass across security and digital operations still be the best option?
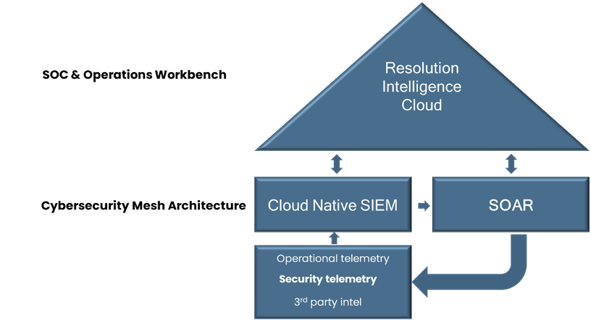
As illustrated below, Resolution Intelligence Cloud sits at the apex of aggregation points. Not only does it glue everything together, but it also sifts through, correlate, and contextualizes all telemetry data, at petabyte scale and Google speed. Resolution Intelligence Cloud dramatically reduces alert noise, presenting actionable insight and evidence based on real-time analytics of both security and operations data as well as asset and user data.
With it, SOCs gain a complete operational picture (COP) and thus, the situational awareness needed to identify true threats and drive the right action based on business risk.
Using the platform, SOC teams can leverage the unique capabilities and strengths of each security tool without needing to continually pivot between tools. They can directly dig deeper into alerts to investigate further and as necessary, establish war rooms. In a war room, they can instantly collaborate (or escalate) with key stakeholders — including digital operations and business stakeholders — to decide the best course of action (incident handling) for high-priority alerts.
Bonus! Resolution Intelligence Cloud stores petabytes of data for a long time
Most security tools offer neither petabyte scale nor long-term telemetry retention — and most that do charge you for all that data and availability. But to find threats, SOCs need scale, data over time, and speed — especially since the average time to identify and contain a data breach is 277 days. (To put that into perspective, the average gestation period for a human is 266 days.)
Historical hot data allows them to retrace an attacker’s steps to understand exactly what happened with an incident. For instance, how attackers gained access to the network, where they went, and what they may have exfiltrated, damaged, or deleted. If stored telemetry data is limited, SOCs may never learn exactly how an incident started — or worse, may miss threats or incidents altogether, especially those with long dwell times. Either way, insufficient data limits their ability to forecast threats and prevent future incidents.
Resolution Intelligence Cloud ingests and analyzes petabytes of data at speed, uses machine learning and behavioral analytics to find potential incidents and actual incidents called ActOns. The platform also prioritizes ActOns based on likelihood, business impact, and confidence so SOC analysts know where to focus. Plus, it automates level-1 and level-2 tasks.
Resolution Cloud Intelligence puts MITRE’s “best strategy” into action by:
-
Getting SOCs to one single pane of glass.
-
Providing integration between technologies.
-
Storing all your telemetry, hot, for a year without penalty.
-
Identifying what matters most and reducing alert noise so analysts know where to focus.
-
Automating level-1 and level-2 tasks.
In short, the platform helps meet the aforementioned goal, providing analysts with information they can use immediately and effectively. Without distracting or exhausting them. Without requiring extensive training. And without busting budgets.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







