How to Achieve Autonomic Security Operations with Resolution Intelligence Cloud?
Published on September 12, 2023 | Last updated on December 18, 2025 | 4 min read

So, what’s a SOC? Some still believe they need a physical SOC building, where they can see, touch, and manage servers. Others feel it’s necessary to have someone monitoring those servers and other systems 24/7. But instead of asking what a SOC is, the better question is why a SOC at all? Because today, no one needs one — at least not in the traditional sense.
Retire your SOC by designing detections unique to your business
For years, security vendors have been engineering detections — in other words, alerts — based on external global data and what they believe is important. They want detections to be broad and noisy by design to satisfy their customers, who’ve been conditioned to believe that if there’s not enough noise, the vendor isn’t doing a good enough job. Consequently, these same customers wind up needing to hire a lot of people to sift through this noise.
We call those people a SOC. And most SOCs are in panic-driven reaction mode, with too many tier-one analysts spending the majority of their time triaging or responding to a mountain of non-contextualized alerts (aka 24/7 monitoring).
Default content doesn’t work. Products don’t need to be noisy; they need to be accurate. So, reduce noise and raise fidelity by designing — and continuously redesigning, adapting, or finetuning — detections that are unique to an organization’s business and focused on specific, relevant operational data.
Low SOC = low noise, low toil, low stress
At Netenrich, we are using our own Resolution Intelligence Cloud platform to achieve autonomic security operations (ASO).
We focus on quantifiably reducing risk by using advanced data analytics and machine learning algorithms to monitor and tune our processes and systems. Our goal is to understand what’s normal and acceptable across our entire environment so we can engineer detections that drastically reduce false positives while also doing control engineering on the backend to make continual improvements and ensure optimal efficiency.
By becoming an engineering- and data-driven security team as opposed to a reactive, panic-driven one, we’re upleveling everyone to be tier-three contributors. In doing so, we’re not only building a team of high-end, valuable professionals, but we’re also lowering attrition — because no one really wants to work on monotonous routine tasks.
The Resolution Intelligence Cloud platform can automate, for example, log analysis, patch management, and vulnerability scanning while also crunching alerts down to a manageable number so that our staff has more time for other higher-priority tasks. What’s more, we’ve pivoted to do more threat hunting. We meet to discuss exposures, threat intelligence in the wild, what we should be looking for based on our business. By taking a more educational and proactive approach, we’ve overcome skills gaps, shortened our response pipeline, and are able to write localized parameters for more useful detections that again, we feed back into the system.
Continuous detection, response, and more
For us, ASO begins with metrics and data quality. We like data — often saying, the more data, the better — but we also believe that just because you can collect data and telemetry doesn’t mean you should. It has to be the right data. To that end, we focus on filtering, analyzing, and proofing data to ensure high-fidelity signals. The higher the fidelity of the signal, the lower our noise floor is, and the higher our confidence is in needing to address a situation.
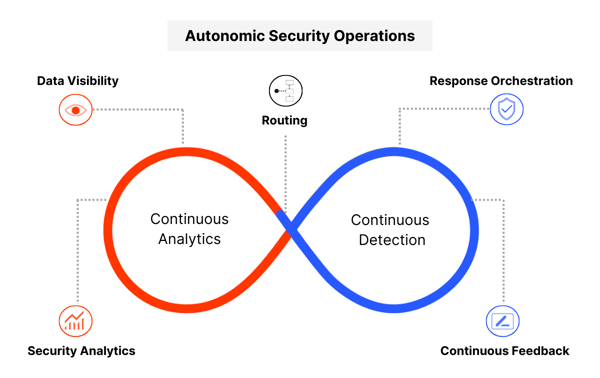
Data visibility
Data quality begins with data visibility, which begins by asking, “What is it?” What’s the asset or entity? What’s the threat? What’s the exposure? What’s the behavior? This step is about discovering what’s in an environment so you can determine what to start collecting data on.
Security analytics
Next comes security analytics, where the question is, “What is it doing?” At Netenrich, we use behavioral modeling to create deeper risk profiles. We look to gain situational awareness and quantify risk. We perform enrichment on particular events or assets to gain greater context. Then, we tie everything together to better understand potential impact. Based on the asset and behavior, is this something we need to care about? Does it exceed our risk capability threshold?
For example, imagine a group of people picketing outside an office. Should you care? Maybe not. But if those people are angry and brandishing pitch forks and torches, maybe you would care. It’s the same with signals. It’s the intention, the behavior, the anomalies in the equation that should determine the level of concern.
Intelligent routing
And if there is an issue, the next question is, who should care about taking a closer look? That’s the concept behind intelligent routing and getting the right information to the right people, right business units, right data owners at the right time. With Resolution Intelligence Cloud, there are impact-based escalation policies that dictate the distribution of ActOns to specific individuals for review and response.
Response orchestration
Next comes response orchestration. “What should we do?”
To determine this at Netenrich, we looked at what our entire SOC team was doing on a daily basis. This included going through their entire workflow for an event, how they would triage, what data elements they needed to stitch together, what data elements they looked for. What we realized is that we could automate the data aggregation and analysis process within Resolution Intelligence Cloud to reduce manual toil and free our team to get more creative about solving tougher issues. Was it simple? No. But was it worthwhile? Absolutely. Time is the great equalizer and we’re taking some back!
Now, when a situation is routed to an end user, that user has a clear picture (ActOn) of what’s affected, what the impact is, what the risks are, what the associated threat intelligence is, and more. This actionable intelligence is also tied into a collaborative workbench, where users can bring in other relevant people as needed — for example, the data owners and the business unit representatives — to decide on a course of action as quickly as possible.
At Netenrich, our DNA may be as operations company, but we understand the power of a combined operations model — aka a blended SOC, NOC, you name it. It’s much more efficient to solve issues together rather than continually passing them back and forth over a fence.
Continuous feedback
The final component is continuous feedback, where the overarching question is always, “How do we improve?”
We’re constantly measuring multiple metrics and looking at historical trends to improve data quality and adapt our workflows. If we’re doing root analysis on an APT, for example, we’re asking questions like: What was the dwell time? How long did it take us to figure out the APT was there?
Then, from every lesson learned, we tune our systems and make changes to improve our process and ultimately, achieve our specific organizational KPIs.
From a taskmaster to self-sufficient approach
For us, the idea of ASO is to design systems like engineers would. In other words, design systems to be self-sufficient and self-healing, not to dole out operational tasks. That’s how to reduce human involvement while also speeding detection and response to minimize any potential damage.
To learn more about how Resolution Intelligence Cloud can help you enhance your current security systems by enabling autonomic security operations — with data visibility, security analytics, intelligent routing, response orchestration, and more — watch the on-demand video Autonomic Security Operations: Manage Risk and Not Alerts.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







