Beyond UEBA: A New Approach to Anomaly Detection and Situational Awareness
Published on June 6, 2023 | Last updated on September 23, 2025 | 3 min read

User entity and behavior analytics (UEBA) has been great at solving some significant shortcomings of SIEM (security information and event management) detection rules. If you can write a rule, you already know about the types of threats you’re trying to detect. But what about the unknowns lurking in your systems? Or finding the right thresholds for a rule? Or assigning a single threshold for all values of an attribute?
UEBA is designed to automatically identify normal and then find abnormal for users and entities. For example, Joan, a software developer, suddenly logs into the payment system (she’s never done that before); and she sets up a new payment account in a country you don’t do business with; and large sums start moving into that account.
Breaking boundaries: From UEBA to “game-changing” behavior analytics and situational awareness
As threats continue to evolve, so too must UEBA. It's all about innovating toward more proactive defense — one of the four main elements of an automated moving target defense (AMTD) model — with the goal of making a threat actor's job not only more difficult, but more costly.
Today, traditional implementations of UEBA track behavior on an attribute — but only if the attribute is associated with an entity or user, for example, an IP address/machine or a user/account. With this approach, UEBA cannot track processes, including rare and anomalous processes, at an environment level.

So, if you want to monitor for ransomware attacks by tracking the behavior of different processes executed in an environment, you’re out of luck.
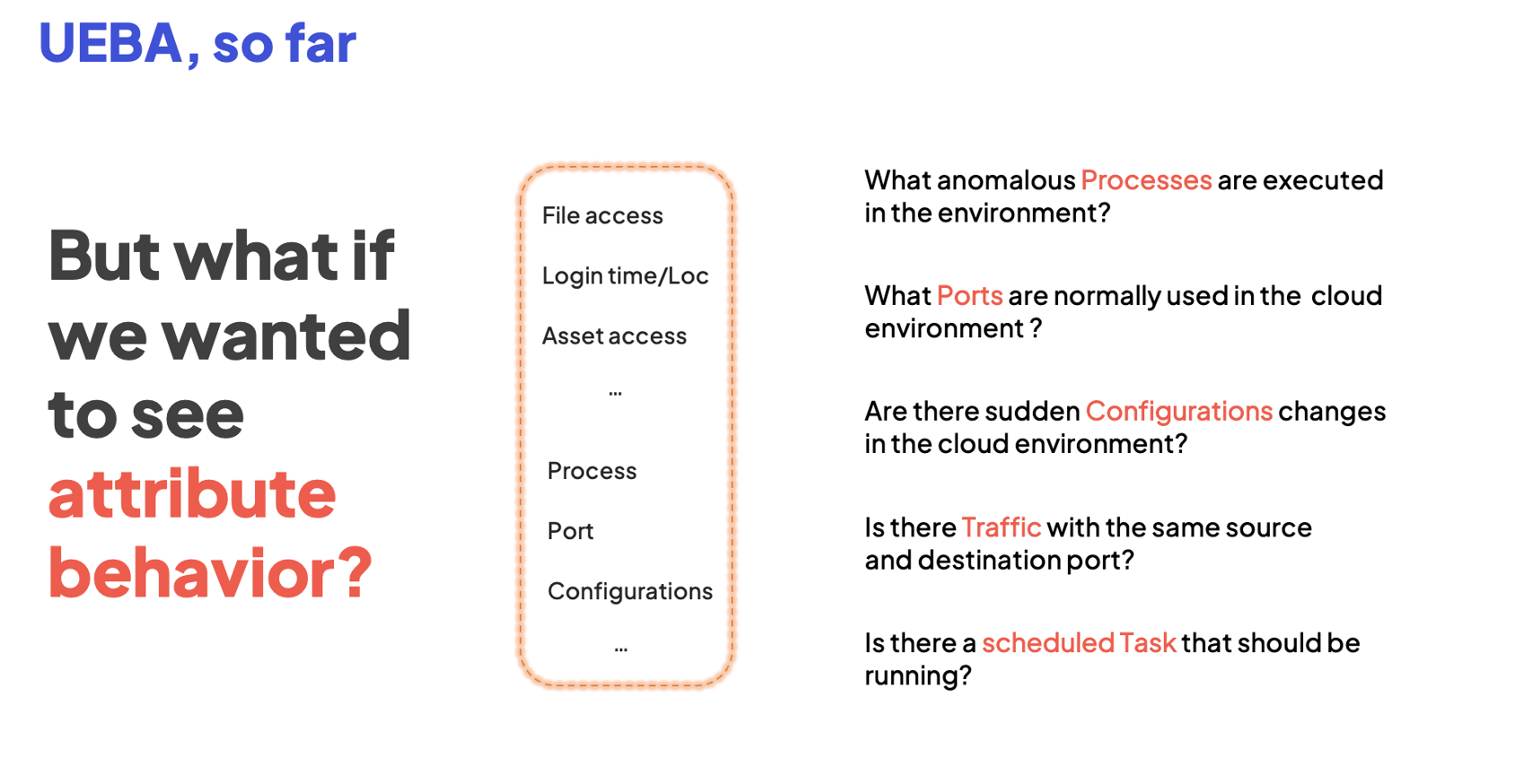
By contrast, Resolution Intelligence Cloud’s behavioral analytics innovation — think UEBA + a whole lot more — enables behavior tracking for an attribute at any level: environment, user, IP, machine, account, etc.
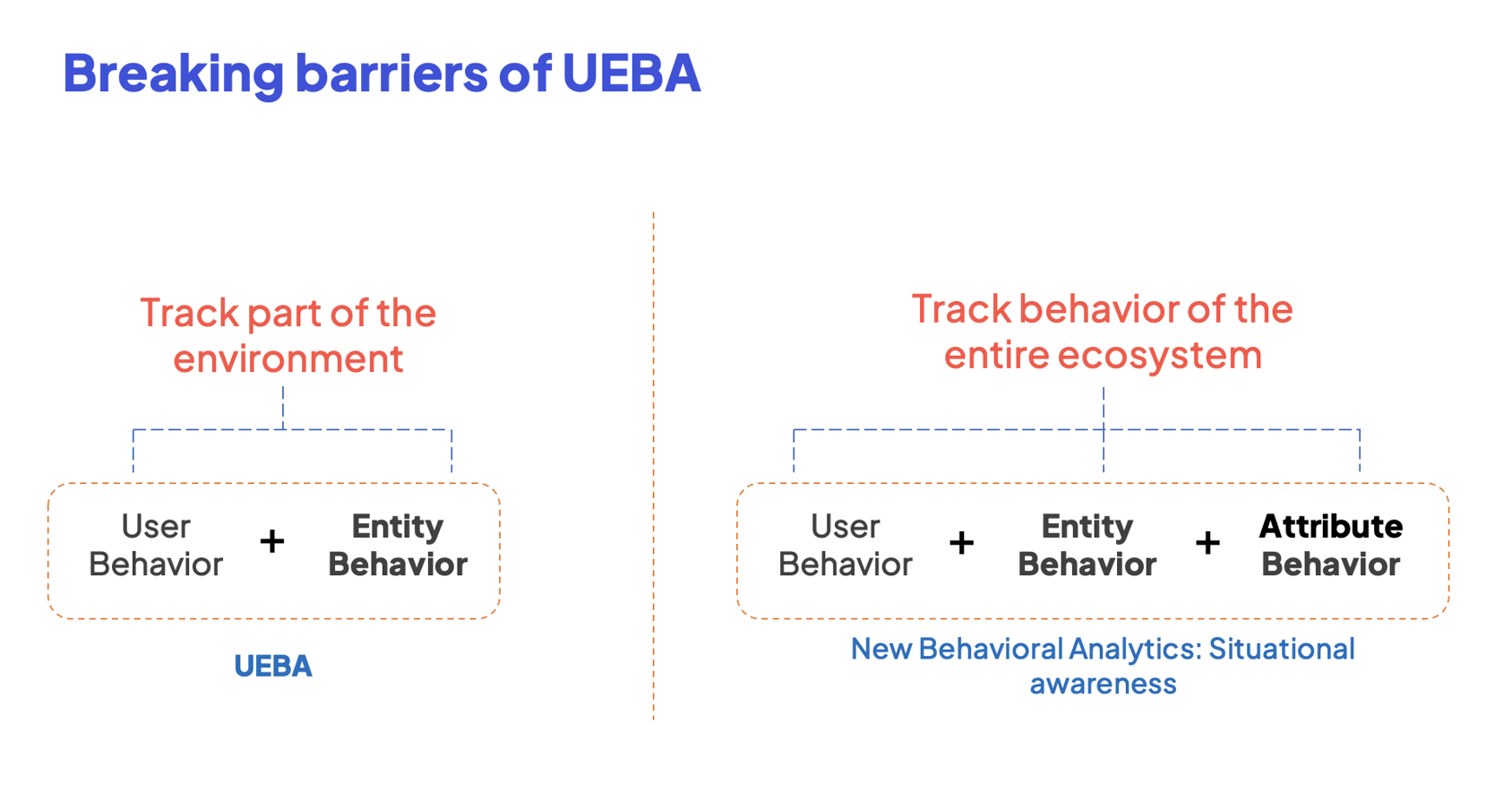
Now, users can expand the scope of behavior analytics, going from conventional to comprehensive monitoring across various attributes to gain situational awareness and a deeper understanding of their operations.
Revolutionizing data interaction with conversational artificial intelligence
Traditionally, data analysis has required slicing and dicing of data points. But as data continues to increase in complexity and volume, this process won’t scale to keep pace.
Resolution Intelligence Cloud’s behavioral analytics' innovation more than reimagines this process. With conversational artificial intelligence (AI), it revolutionizes how SOC teams analyze and interact with behavior data. Instead of needing to slice, dice, pivot, and run complex queries, these teams can now ask questions in plain language; and the system will automatically execute the necessary steps to generate insights.
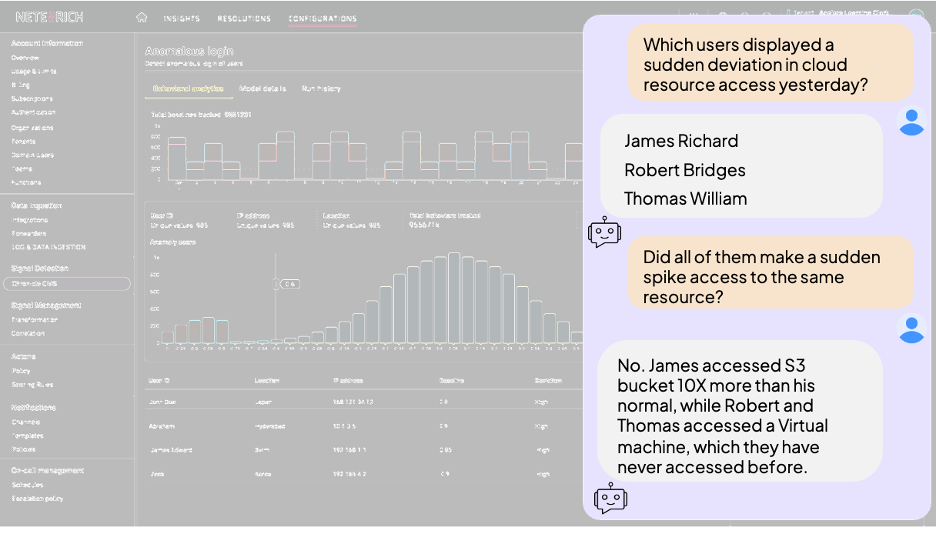
Here, the behavior model is tracking anomalous access to cloud resources. In plain text, it’s easy to ask the system to:
- Identify anomalous behavior based on recent user activity
- Specify the activity - no pivots or analysis necessary.
The language model will simply and automatically identify the right group by, joins, and computations to execute.
Conversational AI overcomes the limitations of technical jargon and complex queries, giving SOC teams unparalleled convenience in making faster, more informed decisions that enhance overall productivity.
Tracking both upshift and downshift in behaviors
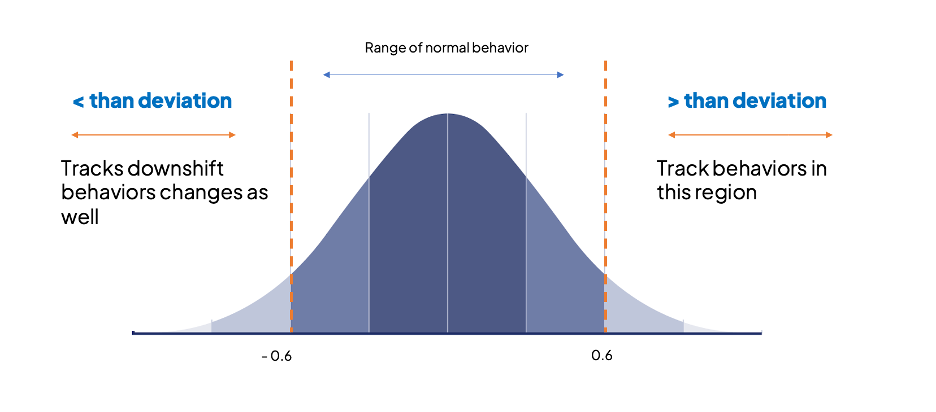
Current practices only identify anomalous activities when they deviate higher than normal. Unfortunately, there are plenty of instances where a decrease in activity can also indicate anomalous behavior. For example, a sudden drop in the number of transactions in a financial system may point to fraudulent activity or an exploit.
To address this gap, Netenrich also developed bidirectional behavior tracking. This new feature identifies both upward and downward shifts in anomalous behavior to create an additional layer of detection that helps organizations become more proactive and accurate in identifying potential threats.
Tuning behavior models with “what if” analysis
Finally, our new “what if” analysis feature lets users simulate situations and adjust deviations in a behavior profile and see outcomes before making actual changes to the profile.
In this example, the behavior model is tracking bytes of user activity. Any deviation from learned behavior greater than 0.8 or lower than -0.6 is deemed anomalous.
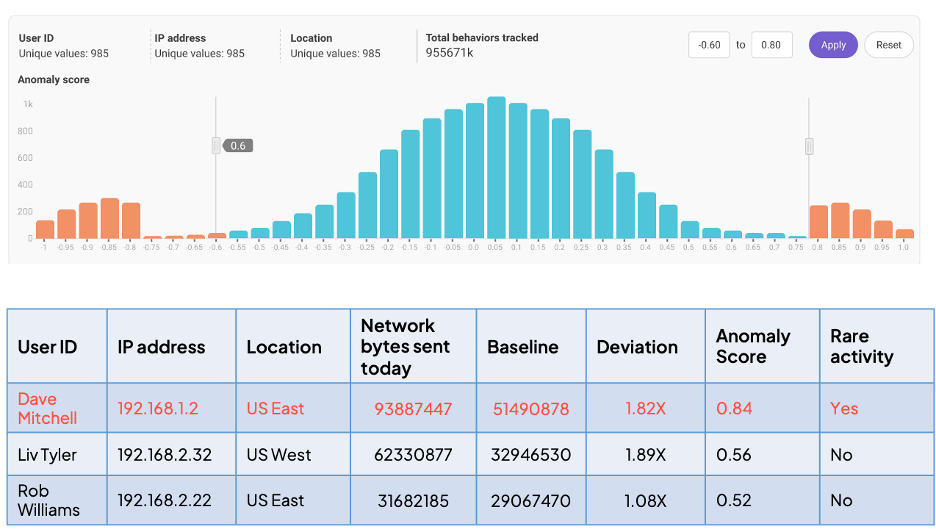
To identify users whose behavior deviates, for example, beyond -0.45 and 0.55, it’s easy to adjust the deviation range markers in the histogram and let the model calculate the corresponding data points.
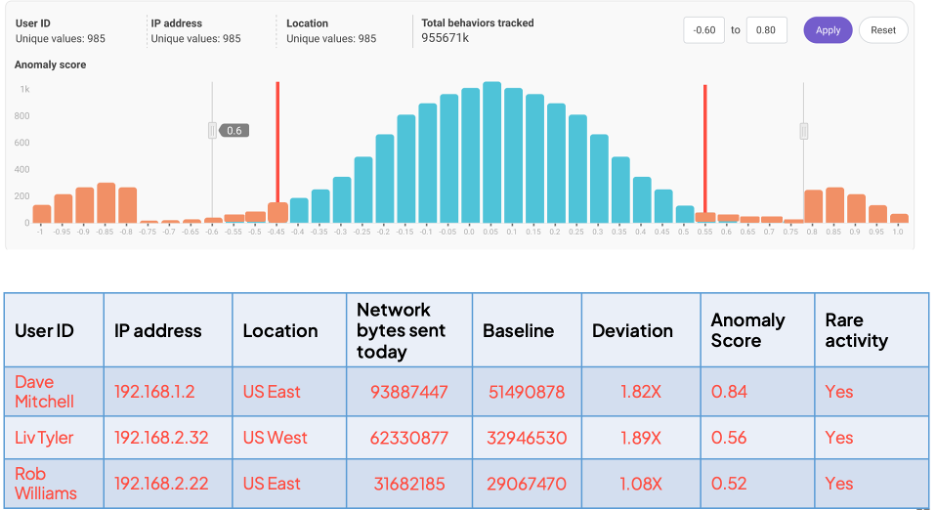
This diagram shows which behaviors become anomalous for the new range of deviation values. Users can leverage this information to fine-tune models, reduce false positives, and minimize the risk of flagging legitimate behavior as anomalous.
Ultimately, "what if" analysis is a powerful tool for SOC teams to improve the accuracy and effectiveness of behavior models and achieve highly-fidelity situational awareness.
Resolution Intelligence Cloud’s behavioral analytics is now available to a limited group of beta customers. If you’d like to take part in this exclusive group and experience the benefits of this new technology, please contact your Netenrich sales rep. Or, if you'd simply like to know more about how advanced behavioral analytics and AMTD tie into a well-thought-out cybersecurity mesh architecture (CSMA) that's flexible, adaptable, and key to future-proofing your security posture, we're here to help.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.






