Attack Surface Management during Mergers & Acquisitions and Cloud Migrations
Published on June 22, 2021 | Last updated on September 23, 2025 | 3 min read

Cybersecurity risks often go through the roof when your organization goes through mergers & acquisitions (M&A) and cloud migrations. However, proper Attack Surface Management (ASM) can help mitigate this risk by giving you easy-to-implement actionable remediation steps.
Why mergers & acquisitions are a cybersecurity nightmare
Including cyber risk protocols and cybersecurity leaders earlier in the M&A lifecycle can be a significant step in assessing potential risks of integrating systems and better gauge the time and effort needed to do it safely. Failure to understand how a merger or divestiture impacts operational risk exposure detracts from future value realization.
More often than not, a bigger company acquires a smaller one with less mature cybersecurity defenses and less developed best practices. Finding severe threats in the early stages won’t affect the decision to move forward with the acquisition but help judge upfront costs and empower the CIOs and CTOs to be prepared about potential issues.
Let’s face it, if your team gets handed a mess after an acquisition has been publicly announced, automating and operationalizing insight around external brand risk speeds the cyber due diligence.
So, how can ASM help here?
- Assess the target company’s overall security posture and find major gaps in defenses quickly.
- Rank critical exposures to focus and fast-track the clean-up campaigns.
- Identify the most pressing cybersecurity issues and receive actionable insight with good indications of where to go next.
- See what the other company might be missing or that problems have persisted well beyond the normal time to remediate.
- Make sure that the acquired company’s assets and processes don’t introduce risk — or work — into the acquirer’s incumbent environment.
- Look up breached email IDs and show whether specific usernames and passwords have already been compromised.
For example, Netenrich’s Attack Surface Exposure (ASE) will show instantly whether domains that look like the acquired company’s public sites exist, who they’re registered to and whether the sites are actually active.
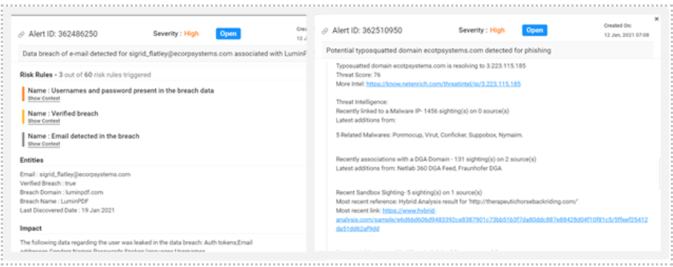
If you find someone mimicking your brand, you might want to drill down a bit to see what risk rules got triggered during discovery. A quick correlation with threat intelligence drives valuable context around whether the IP a domain is resolving is known to be associated with malicious activity and should be tackled first.
Cloud migration will always be an issue
While migrating apps and services from physical systems to the cloud, your security team often faces two obstacles:
- Loss or lack of visibility
- The cloud’s dynamic nature
In events like annual sales, you need your servers to scale up exponentially to handle this sudden escalation in demand. However, this could lead to a lot of unforeseen risks. Continuous attack surface monitoring helps you stay on top of exposed or unauthenticated services and publicly exposed storage, even if one or more of your cloud providers has gaps. ASM helps steadily improve best practices and lets you see what matters as soon as it changes.
So, how can ASM help here?
ASM targets the major hazards of cloud migration, which include:
- Hosted cloud infrastructures spinning virtual machines (VMs) up and down.
- VMs that served a purpose once and are left running when no longer needed.
- Multi-cloud environments add to chaos.
- Find critical risks that may arise simply from services being left unauthenticated.
- Detect code left exposed in public repositories and recommend appropriate action.
- Help ensure assets and your digital footprint do not unknowingly become exposed without the proper security controls being put in place.
- Dynamically test security controls.
- ASM increases security earlier in the migration or DevOps lifecycle and throughout the coding process by offering an easy, always-on safeguard to help keep you current and in control.
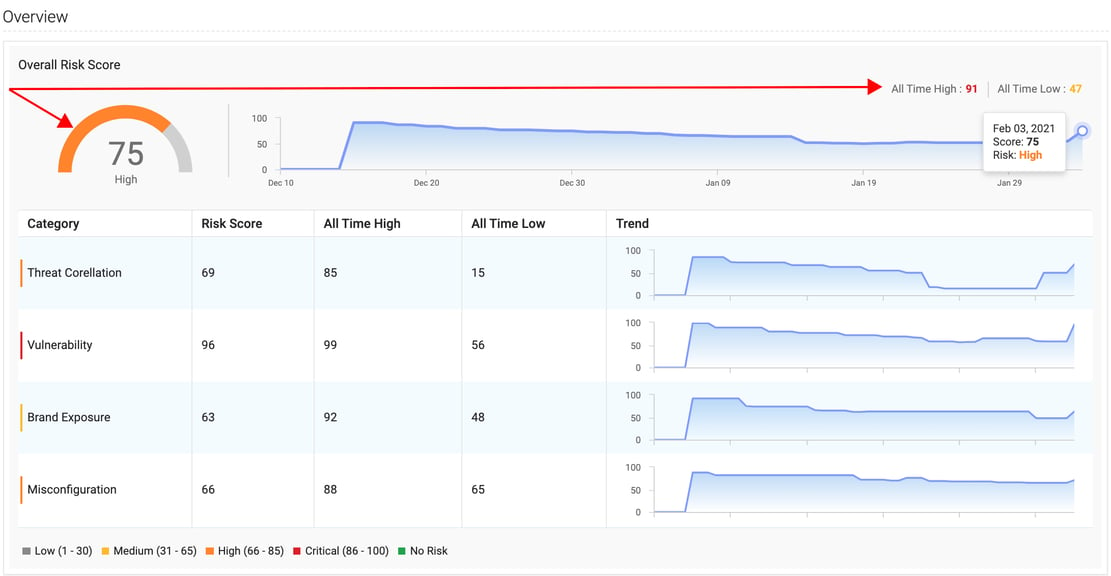
Without an automated “heads up,” finding these misconfigurations as they occur is virtually impossible at worst and daunting and time-consuming at best. Quickly detect a wide variety of threats and exposure and perform thorough investigations and analyze the impact of vulnerabilities lurking in your attack surface before they become a problem.
Conquering cloud migrations, M&As, and everything else…
Continuous testing of your company’s attack surface is the best way to fortify your cybersecurity posture. Check out the eBook, 7 Times to Attack Your Attack Surface in 2021, for a more in-depth look and detailed examples of how ASE takes your SOC and security experts from discovery to analysis to remediation in little to no time.
Empower your team to become more proactive and fix the holes in your organizational attack surface before they get exploited. Reduce toil and increase productivity with Netenrich’s Attack Surface Exposure.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







