Five Times You Should Attack Your Attack Surface
Published on May 4, 2021 | Last updated on September 23, 2025 | 3 min read

Short answer: all the time. Since that doesn’t happen, there are some powerful “inflection points” for taking stock of your digital attack surface and implementing new techniques that are both practical easy enough to do regularly.
Attack Surface Management (ASM) represents one such affordable, efficient, and convenient approach. The term attack surface management describes the continuous assessment of your digital external exposure. Situations that could cause a spike or anomaly in external risk include:
- Migrating to cloud
- Mergers and acquisitions
- Dealing with Shadow IT
- Gauging third-party risk
- Preparing for cyber audits
Let’s take a quick look at a few of these.
#1 Migrating to the cloud
While migrating apps and services from physical systems to the cloud, your security team faces two formidable obstacles:
- Loss or lack of visibility
- The dynamic nature of cloud
Attack surface management targets some major hazards of cloud migration:
- Hosted cloud infrastructures spinning virtual machines (VMs) up and down
- VMs that once served a purpose but get left running when no longer needed
- Multi-cloud environments that add to the chaos
ASM should continually detect publicly accessible unauthenticated services within 24 hours.
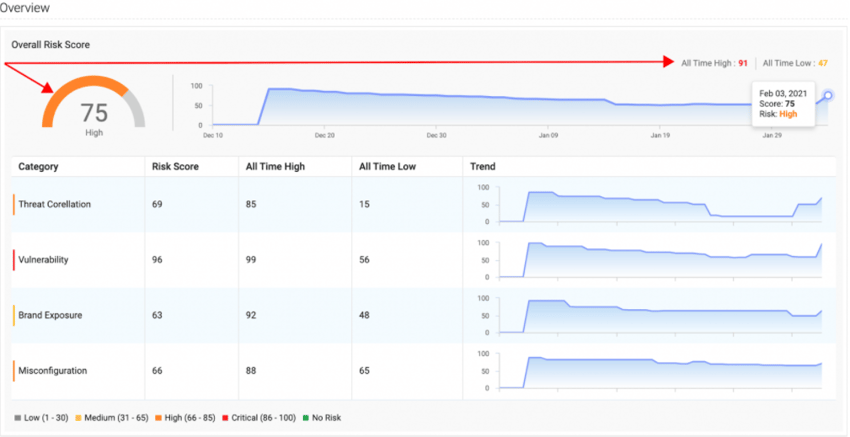
Netenrich Attack Surface Intelligence (ASI) quickly detects a wide variety of threats and exposure and analyzes the impact of vulnerabilities lurking in your attack surface before they become a problem.
#2 Mergers and Acquisitions
Cybersecurity issues may creep up during mergers and acquisitions. When a bigger company acquires a smaller one with less mature cybersecurity defenses and best practices, IT, and security teams in particular, may not get brought in early enough to avert unnecessary risk. If the team gets handed a mess after an acquisition has been publicly announced, automating and operationalizing insight around external brand risk speeds the cyber due diligence.
Attack surface management can help assess the target company’s overall security posture and find significant gaps in defenses quickly.
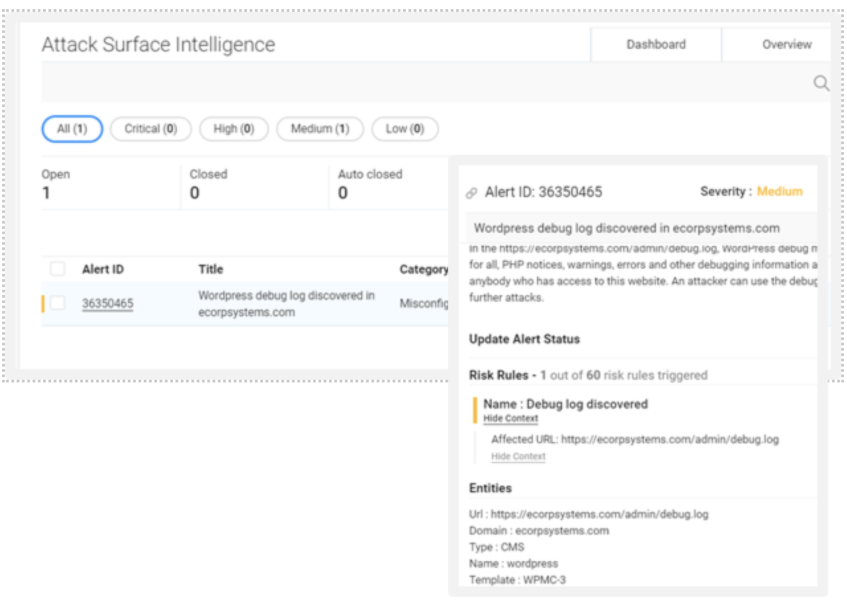
#3 Shadow IT
The increased presence of shadow IT in your organization’s ecosystem puts security at equal or greater risk than phishing attacks and other cyberattacks. For example, your marketing team or one of its agencies may have hosted web-based events or content that did not pose much of a threat in and of themselves. But someone might forget to renew a domain name only to have an adversary hijack the URL for use in a phishing campaign.
Cloud storage processes, IP addresses, and services all may contribute to Shadow IT at one time or another. A proper Attack surface management can discover many things quickly. The dashboard below shows one instance in which Netenrich Attack Surface Intelligence (ASI)* discovered unexpected assets in Azure when, having migrated, IT would expect to see only Amazon Web Services (AWS).
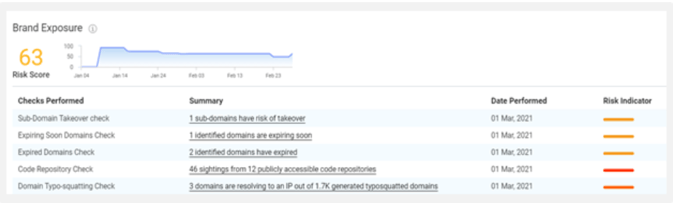
#4 Third-Party Risk
While you cannot control everything that happens on the public Internet, you must continually seek it out, monitor, and address your risk in relation to it. ASM can play a role in a multi-pronged strategy to spot and find and eliminate risk from third-party services
Having integrated with Google Cloud Platform (GCP), Azure, AWS, and other leading public infrastructures, Netenrich ASI offers quick context that speeds resolution. ASI keeps a constant watch over your cloud footprint, flagging anomalies like public-facing Amazon S3 buckets within the “Brand Exposure” category.
#5 Cyber audits
A lot goes into preparing for any audit, and attack surface management can help focus efforts such as pen testing and vulnerability management — a huge plus. Solutions like Netenrich ASI offer evidence that may help satisfy auditors that you’re monitoring specific elements of individual cybersecurity frameworks and mounting an aggressive defense overall
Justifying your security spend
ASM plays an increasingly vital role in preventing that from happening, delivering fast, ongoing coverage and investment value. Moreover, you can demonstrate that you’re eliminating exposure—and work—as time goes on to avoid risk in the first place. Though harder to quantify than the value of analyst time saved, lessening your appeal as a cyber target is a valuable indicator in assessing ROI on security investments.
ASM dashboards afford an easy way to show a steadily shrinking attack surface or that you’ve got things covered during predictable spikes like holiday shopping, market fluctuations, healthcare crisis, and the like.
The “secret sauce . . . ”
The five common events described here are only the tip of the iceberg for when, where, and why continuously reducing risk from your digital attack surface should be top of mind. Check out the eBook, 7 Times To Attack Your Attack Surface in 2021. for a more in-depth look and detailed examples of how ASI takes your SOC and Security experts from discovery to decisive action in a fraction of the time, it takes now.
Download Guides | 7 Times to Attack Your Attack Surface
Download
You’ll see how ASI uniquely equips your team to become more proactive and predictive about preventing exposure that creates more work in terms of detection, recovery, and resilience efforts—and, how to try it risk-free. Would you rather talk to one of our representatives?
*Please note, Attack Surface Intelligence (ASI) is now known as Attack Surface Exposure (ASE). For more information, please contact us.
Get in touch
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.






