Looking “Left of Bang” to Increase Situational Awareness
Published on January 5, 2023 | Last updated on September 18, 2025 | 2 min read

At Netenrich, part of what we’re doing is looking "left of bang." Bang (!) is geek speak for when we see detonation of malicious content. What happens before the compromise that makes us more likely to get hacked? We call it situational awareness. At any point along the way in a correlated series of events leading to a compromise, we can take action and remove the risk before bang.
Consider a few common scenarios where situational awareness and action prior to compromise could change the outcome:
- Per LexisNexis, your cleared employee just filed for bankruptcy.
- Your public-facing website has seven (7) critical vulnerabilities.
- Your company has 17 interns. One of them is a member of domain admins.
- Of your 1,500 ATM machines, one is running different software than the rest.
- Your production cloud environment has 15 different “containerized operating systems.”
- An employee starts publicly posting hundreds of very nasty things about your company.
- A key employee is uploading or emailing resumes.
- A point-of-sale machine has zero free disk space and CPU utilization is at 90% — and your biggest sale of the year starts in an hour.
- The events per second count from a critical log source went to zero or spiked to 300% more than normal.
- A device is communicating on a never-before-seen port or on an insecure port (69, 20/21, 23, 25 | SFTP, FTP, Telnet, SMTP).
Looking beyond risk — predicting likelihood
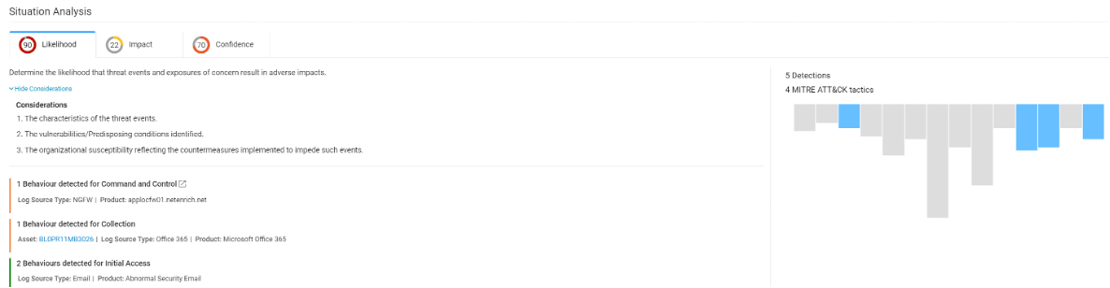
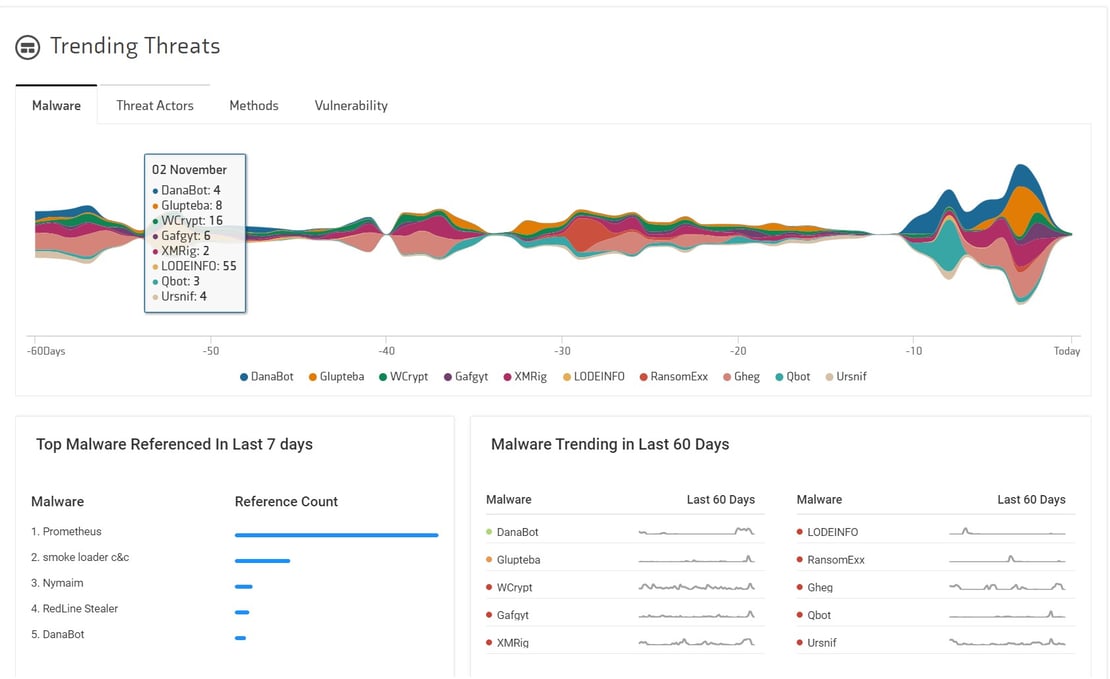
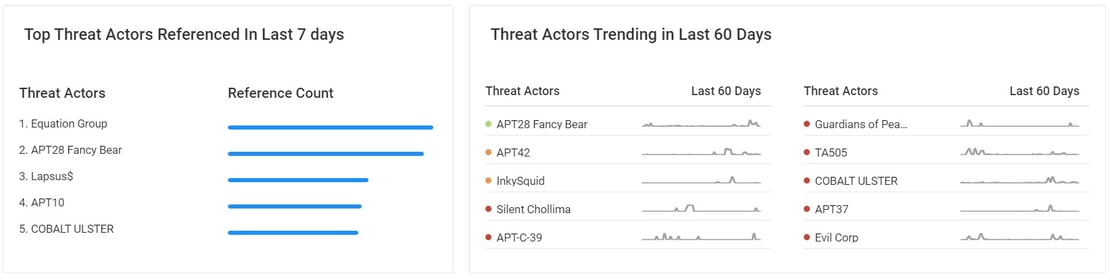
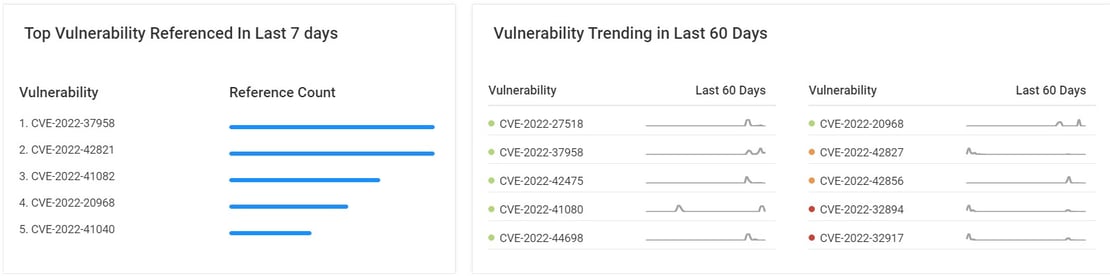
As we extend situational awareness and tie events to active threat campaigns and exploits known to be in the wild — see Netenrich Knowledge Now (KNOW) for a free “trending threats” feed — we go one level deeper and can predict the “Likelihood” of an exploit.
How? By combining knowledge about the asset, its vulnerabilities, the number of exploits in the wild that leverage those vulnerabilities, and the actors and campaigns using those exploits. We can even map a customer’s business type to the campaigns targeting that vertical.
Knowledge Now (KNOW): Real-time global threat intelligence
Attack Surface Intelligence uncovers hidden risks and exposures
Netenrich combines auto-discovery of assets linked to a domain, vulnerabilities, and public information into Attack Surface Intelligence (ASI)* to surface public security risks and exposures prior to exploit.
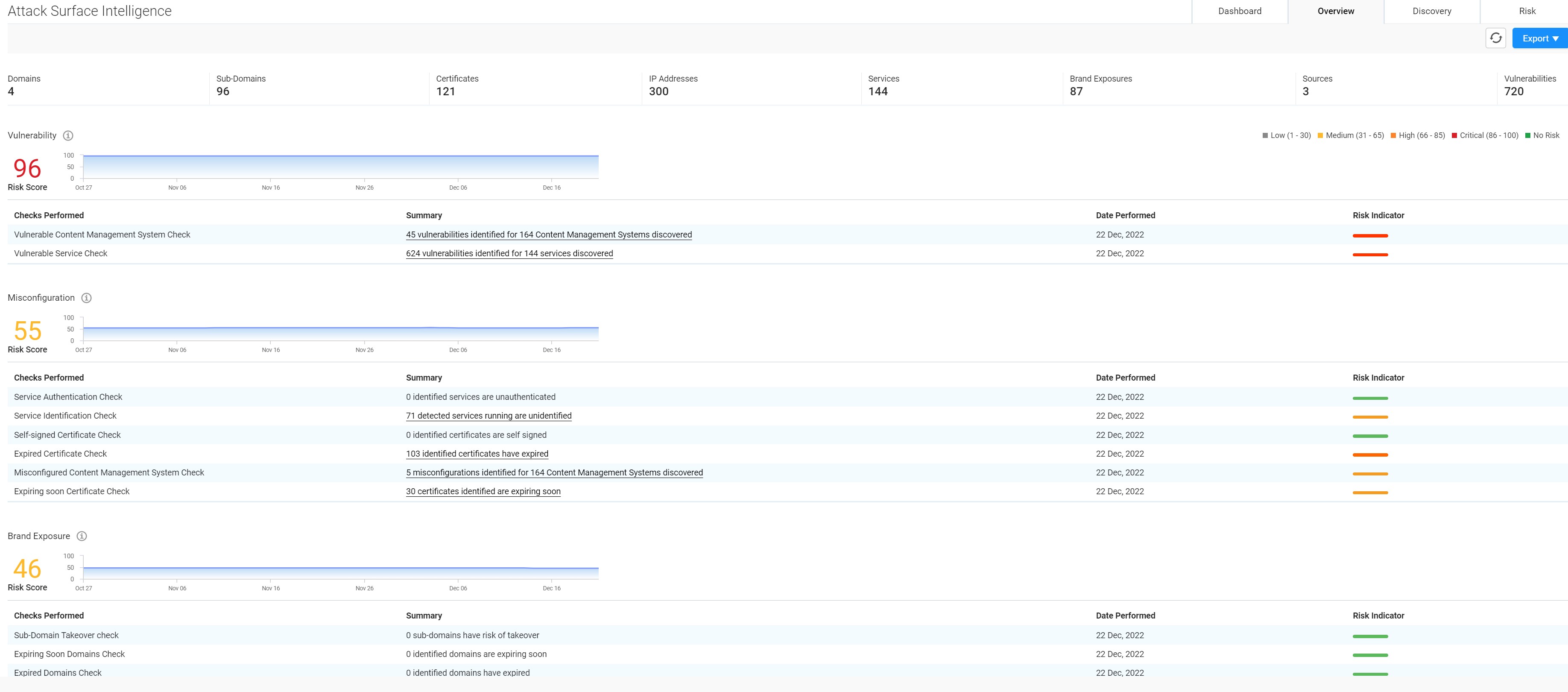
And if you need help, we offer vulnerability management services (vulnerability scanning/asset discovery) and digital management services (patch management and proactive asset resolution).
And compliance says?
On the CIS 18 Critical Security Controls list, asset inventory ranks as the #1 and #2 top priorities. If you don’t have a plan for asset discovery, inventory, and risk profiling — in other words, a “left of bang” plan to improve situational awareness — you might get burned by your auditors or have a cybersecurity insurance renewal or claim denied because you didn’t follow best practices. And that’s even if you don’t get hacked.
In the next installment in this series, I’ll lay out some common threat scenarios and show what we can detect.
*Please note, Attack Surface Intelligence (ASI) is now known as Attack Surface Exposure (ASE). For more information, please contact us.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







