Table of Contents
- Introduction
- Align risk with operations to protect what matters
- Insight to action in a fraction of the time
- The metric that matters: Quantify Mean Time to Compromise (MTTC)
- Staying aligned — less risk with less effort
- Resolving for resilience
- Start today. Scale tomorrow
- Features and benefits
- DOWNLOAD A PRINTABLE VERSION
This guide helps CISOs, CIOs, and their boards to manage cybersecurity risk and, in the process, reduce exposure to harm.
Align cyber risk with operations
and protect what matters
|
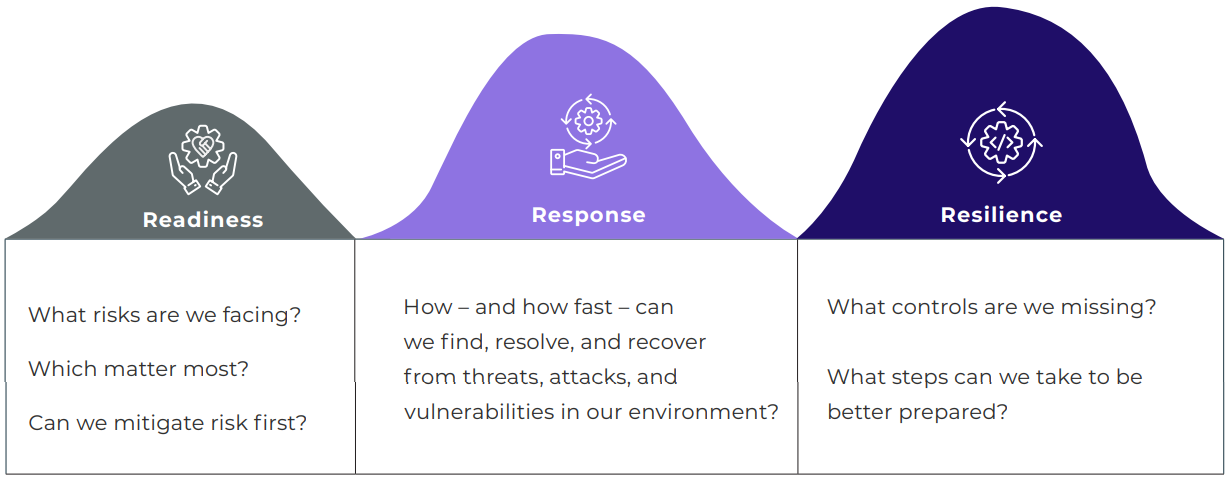
How do you improve cyber resilience across an ever-changing threat landscape? Keeping security operations (SecOps) aligned to risk gives your business a lasting advantage over ransomware, malware, and other devastating cyberattacks. Netenrich Resolution Intelligence Cloud creates ongoing situational awareness based on potential impact so you can strengthen resilience while reducing complexity. |
.webp?width=341&height=212&name=align-risk-with-operations-to-protect-what-matters%20(1).webp)
|
|
We operationalize cyber risk management to deliver actionable insight that helps ensure availability, improve response, and maximize return on cybersecurity investments (ROI). Predictive analytics and actionable context help resolve customer issues quickly while keeping SecOps aligned to risk as your threat landscape changes. |
Insight to action in a fraction of the time
|
Netenrich's Resolution Intelligence Cloud platform leverages machine learning (ML) and 14+ years’ ops expertise to drive awareness when or even before you need it. Our platform takes in and enhances data from multiple sources to illustrate fast-changing dynamics between your business assets, security controls, and the various techniques attackers use to steal data and hijack operations. Our ongoing process combines:• Asset management |
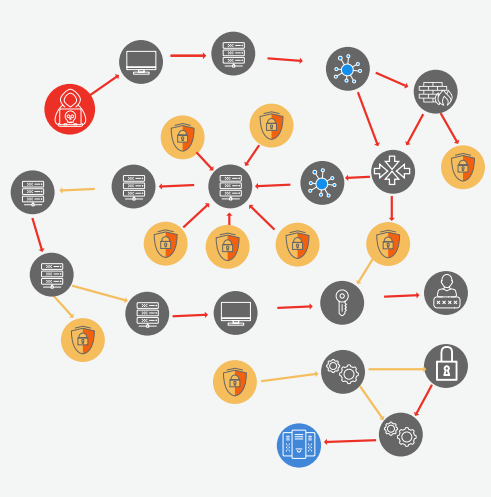
Advanced threat modeling charts the various paths attackers can take to compromise assets, operations, and data. |
We quantify cyber risk and deliver rich context, prioritization, and recommended steps to mitigate and avert risk. Prescriptive insights drive smarter, faster threat hunting, detection, response, and resolution out of the gate and over time.
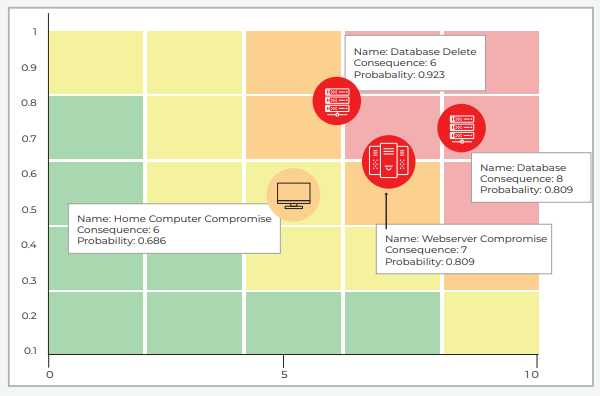
Graphical heat maps show which assets are easiest to compromise so IT and security teams can prioritize mitigation and be more proactive.
The metric that matters: Quantify Mean Time to Compromise (MTTC)
No security team can chase every alert or block every attack, but you should always know where to start. Resolution Intelligence Cloud for situational awareness quantifies and scores risks based on likelihood, confidence, and impact of a potential threat or attack. This way, your defenders can better predict, intercept, disrupt, and prioritize response to attacks.
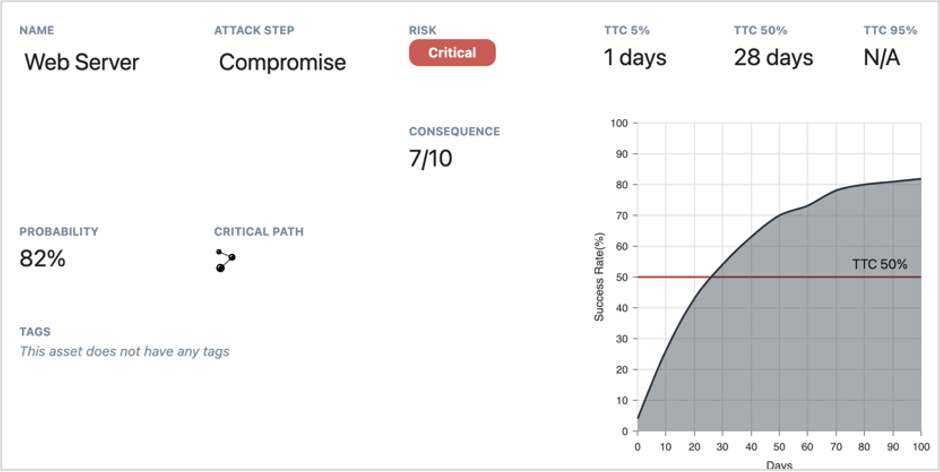
The process starts with identifying your organization’s crown-jewel assets — the data, systems, operations, and processes the business cannot run without — and modeling step-by-step pathways to reach them. The Netenrich solution measures the likelihood of attack and applies trending threat intelligence about your environment to calculate attackers’ mean time to compromise (MTTC) — a meaningful “true north” metric by which to manage SecOps.
MTTC – Cybersecurity’s new “True North”
The Resolution Intelligence Cloud dashboard shows that the probability of a web server being compromised within one day is 6 percent. If the attack path goes unaddressed for 28 days, the probability of an attack succeeding rises to 50 percent.
Emulating adversary behaviors shows defenders how — and how quickly — intruders might navigate from various entry points to steal data or shut down operations. Even with unprecedented insight into attack probability, your defenders need to know more, like what steps to take and when something changes. Netenrich reports and dashboards feature recommendations on what to do — and do first — to disrupt malicious behaviors. Ongoing discovery detects events that automatically trigger additional threat modeling and adversary emulation.
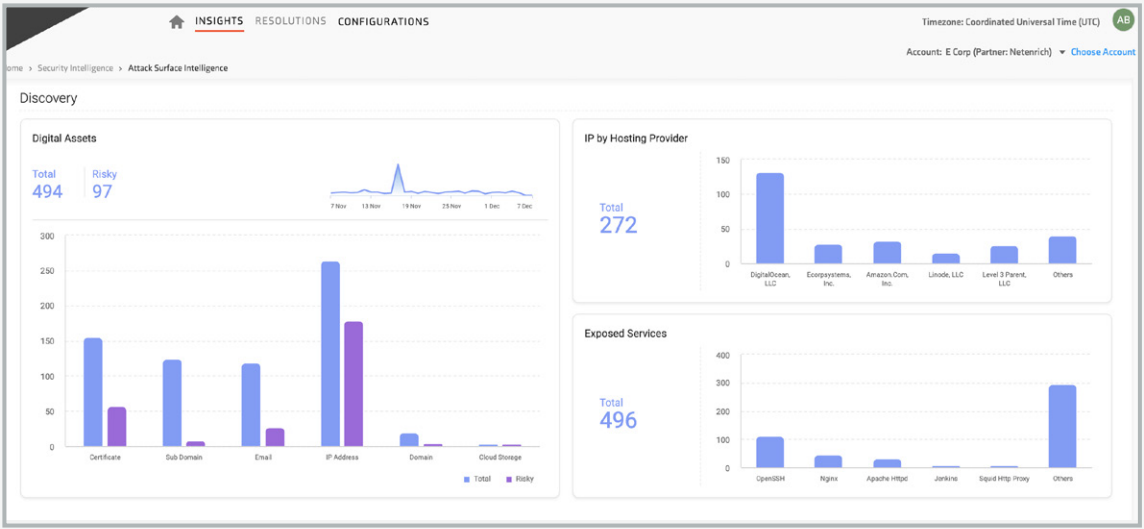
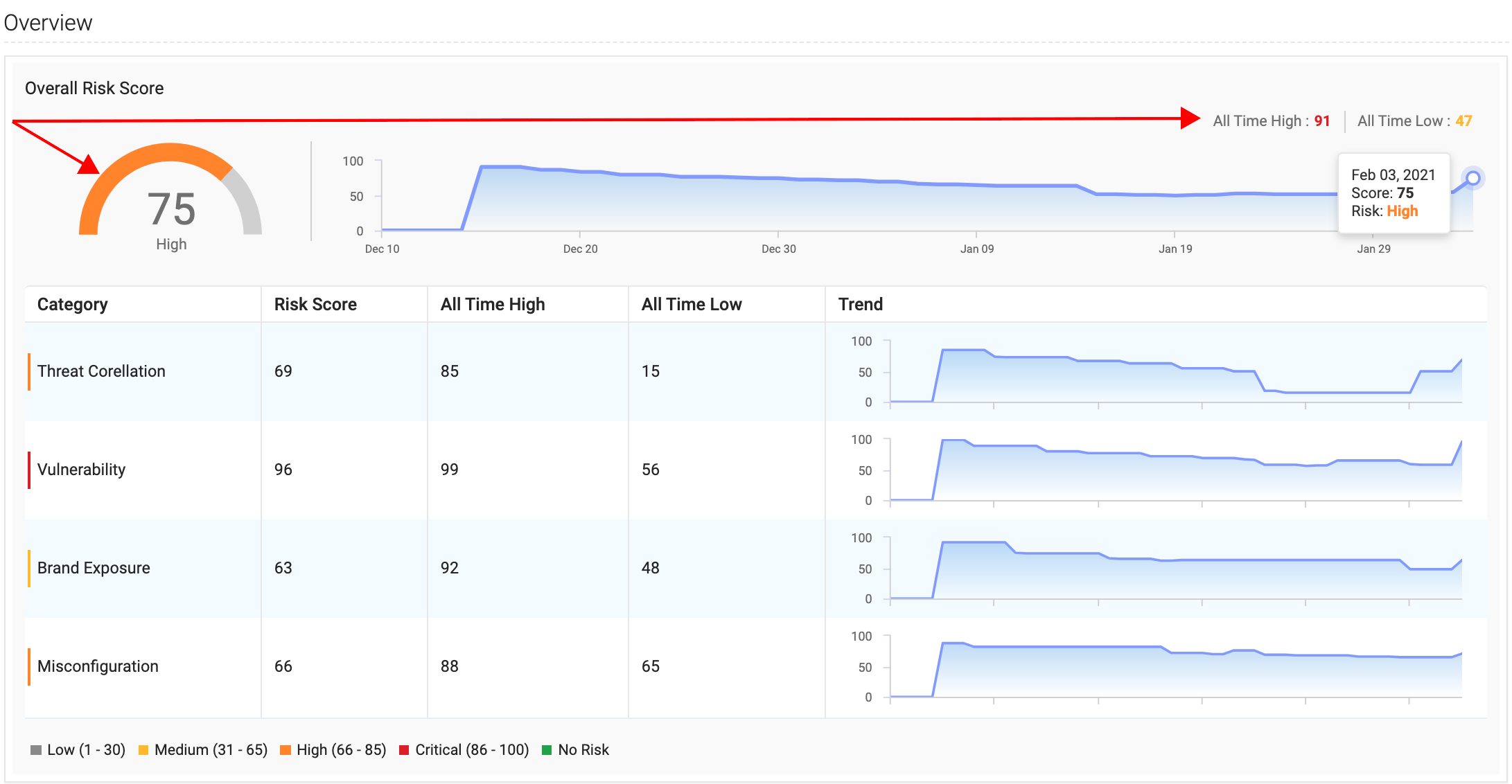
Netenrich Attack Surface Exposure (ASE) automatically discovers risk from brand and domain exposure (for example, sub-domains, websites, certificates, content management systems, etc.), unpatched vulnerabilities, and misconfigurations. Analysis and prioritization take place continuously with easy drill-down investigation into individual risks uncovered.
Compared with penetration tests, red teams, and security ratings that provide only point-in-time perspective, Netenrich ASE delivers ongoing coverage and assessment of brand risk from domains, cloud exposure, unpatched vulnerabilities, common misconfigurations, and shadow IT.
Staying aligned — less cyber risk with less effort
To achieve resilience, SecOps must stay aligned with cyber risk. Netenrich Resolution Intelligence Cloud brings together the right technology, automation, people, and processes in one powerful software-as-a-service (SaaS) platform to promote better collaboration across IT, security, and cloud operations. Sharing a common analytics platform helps to democratize security so all teams make better decisions to drive resolution in a fraction of the time.

If, after aligning risk with operations, you need help with execution, Resolution Intelligence Cloud for threat detection can drive higher efficiencies within your security operations center (SOC). Our solutions span vulnerability management, detection and response, patching, and attack surface management on an ongoing basis.
Resolving for cyber resilience
Netenrich Resolution Intelligence Cloud adds predictive analytics that help slow attacks and speed response based on risk and business impact.
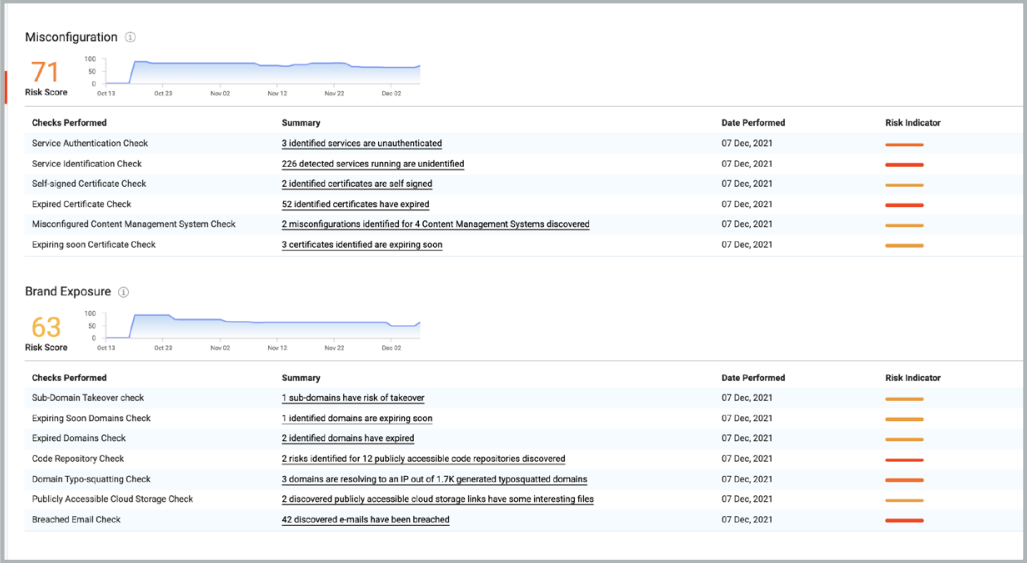
Inadvertently or accidentally leaving company assets exposed — having code available in public repositories or accessible via public cloud storage — contributes to risk.
Start today. Scale tomorrow.
|
Try Netenrich Resolution Intelligence Cloud to gain situational awareness and streamline SecOps, shrink your attack surface, and strengthen your cyber risk posture within weeks. Flexible pricing tiers are based on the number of licenses, assets, and expert evaluations your environment requires. Try it risk freeThe missing piece. Complete, ongoing cyber situational awareness pulls together data, intelligence, and processes to document the relationship between your critical assets, internal and external risk, and IT and security controls. |
|
Features and benefits
| What you get | What you gain |
| Automated asset and privileged access discovery |
• Visibility and control of users with privileged
access to valuable assets
• Discover shadow IT and deprecated assets • Eliminate manual asset discovery |
| High-value asset discovery | • Visibility and understanding of high-value assets • Risk-driven prioritization • Leverage controls in the attack path |
| Threat modeling and adversary emulation |
• Map, rank, and shut down potential paths to
attack high-value assets based on impact and likelihood
• Align ops to mitigate the most critical threats first • Increase time to compromise assets • Threat intelligence contextualizes adversary emulation |
| Quantify Mean Time to Compromise (MTTC) |
• Proactive risk mitigation
• SecOps aligned around meaningful “north-star” metric • Contextualize and prioritize mitigation efforts |
| Regular/on-demand threat briefing calls |
• Expert insight into how trending threats affect your
business and critical assets
|
| Attack Surface Exposure (ASE) |
• Discover external risk from publicly exposed or typo-
squatted domains, compromised email credentials in
breached databases, exposed credentials in public code
repositories and public cloud storage, unauthenticated
services, content management systems (CMSs), expiring
or abandoned certificates
• Speed and prioritize threat hunting, detection and response efforts
• Maintain situational awareness across dynamic a threat landscape
• Alert threat modelers to changes in the external attack surface
|