The Goldilocks Principle for Accurate Security Data Collection
Published on November 2, 2022 | Last updated on September 24, 2025 | 3 min read

Strategy 6 of MITRE’s 11 Strategies of a World-class Cybersecurity Operations Center focuses on cyber threat intelligence (CTI) data. Strategy 7, on the other hand, discusses log and sensor data — in other words, the largest chunk of data a SOC collects.
At its core, strategy 7 is about balance. First through totality; and then, specificity. Let me explain.
MITRE Strategy 7: Select and collect the right data
CHALLENGE: Most constituencies generate more digital data than a SOC can possibly process and act upon.
When it comes to data selection and collection, MITRE states it’s important to “consider the trade-offs of too little data (and therefore, not having the relevant information available) and too much data (such that tools and analysts become overwhelmed).”
Ugh. Trade-offs.
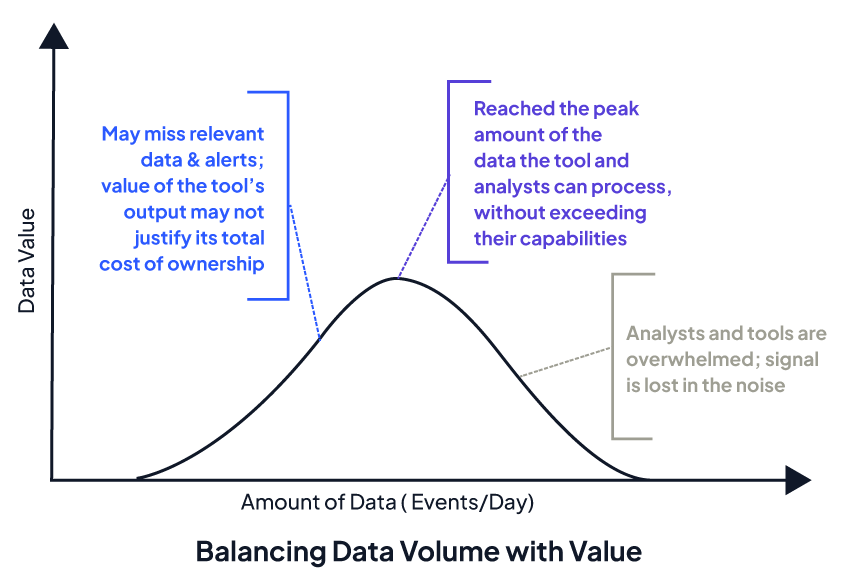
Figure 1 Finding the right balance. Source: 11 Strategies of a World-class Cybersecurity Operations Center, MITRE, 2022.
Most companies are either collecting too much or too little data — the right balance seemingly as elusive as a perfect porridge. But what if, like Goldilocks, you could get data collection just right? No trade-offs, no concessions. Just the right data at the right time in the right context.
It is possible.
All data sources are not created equally
MITRE also says, “For both detecting and confirming intrusions, data and instrumentation from endpoints are generally considered more informative and provide more clarity than data from network traffic.”
In short, you have to carefully consider data sources.
Regardless of whether you’re an enterprise, MSSP, or MDR services provider, if you’re collecting network telemetry, for example, from a network detection and response (NDR) solution, an endpoint detection and response (EDR) platform, or a web application firewall (WAF), you need to collect the right information. For example, if you’re a financial institution, you need to know that the tools you have in place are providing adequate coverage and protection against adversaries targeting your specific industry.
But given the fast-evolving sophistication and relentlessness of threat actors, you don’t necessarily know in advance what data is most relevant. Clearly, if you filter the data you collect and/or don’t store it for enough time, you risk important data gaps that disable you from detecting patterns in that data. Trust us, threat actors love to hide in these data gaps.
Why limit the security data you collect? Typically, it’s because of budget and technology. When your costs soar as you ingest more data and store it for longer, you have to impose limits.
There’s also the issue of managing and making sense of unlimited data. Most teams don't have the necessary data science skills. Many tools don’t help — they’re notoriously slow for large queries required for threat hunting and threat detection. Or the data isn’t real time. So, you’re late to the party before you even get started.
What if you could easily and cost-effectively collect all your data so you knew you had the right data over sufficient time? And what if you had the technology to make sense of all that data — without having to hire a team of security experts with PhDs in data science?
Unlimited but cost-effective data collection
With Resolution Intelligence Cloud, you can have your data and eat it, too — that is, you can make sense of it to accomplish your security goals. Ingest any amount of data you need from any source. Store it hot for a year. That means storing data from across all security and digital operations without penalty — either in terms of ingestion expense or analyst overload.
Get sub-second response on petabytes and run data analytics out-of-the-box without hiring data scientists. Benefit from a no-code machine learning toolkit. The platform enables your existing team to do even more because they have the actionable insights, evidence, and information they need at their fingertips.
With the correct data volume and right tooling, you can start to see the big picture — especially if you leverage Resolution Intelligence Cloud.
The platform uses 13 machine learning algorithms to connect the dots and display an organization’s detection coverage on a heat map, identify risky behaviors, and discover situations — before they become incidents. The platform prioritizes these pre-incident situations by risk to the business based on impact, likelihood, and confidence. This way, you and your team know where to focus to keep digital operations secure.
Again, it’s all about balance. Too much data = too hot. Too little data = too cold. Resolution Intelligence Cloud = just right.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







