Netenrich Hybrid SOC and Security Tools Strategy Report 2024: Six Key Takeaways
Published on July 16, 2024 | Last updated on September 24, 2025 | 2 min read

In an era of escalating cyber threats, understanding the evolving landscape of security operations is crucial. Our recent Hybrid SOC and Security Tools Strategy Report 2024 delves into the heart of this matter, surveying over 200 tool procurement decision-makers from U.S.-based organizations with 500+ employees. Participants included chief information security officers (CISOs), vice presidents/directors of information security/security operations, security architects, and InfoSec managers.
Our goal? To uncover what’s working, what’s not, and what’s on the horizon for them for cybersecurity practices and strategies. While the survey was comprehensive, we’ve distilled the findings into six key insights. How do these align with your experience in the field?
1. The adoption of hybrid SOC models

Many organizations are shifting towards a hybrid Security Operations Center (SOC) model, which combines in-house security operations with outsourced services to balance control and cost-effectiveness. According to the report, 33% of respondents use a hybrid model for round-the-clock coverage, while 60% manage their SOC entirely in-house. Only 7% fully outsource their SOC, indicating a preference for maintaining control and flexibility. This trend indicates a preference for balancing control and flexibility with external expertise.
2. The risk triangle of hazard, exposure, and vulnerability looms large
Security risks continue to evolve, with decision-makers focusing on the interplay of hazard, exposure, and vulnerability. Key concerns include operational disruption, revenue loss, and reputational damage. To mitigate these risks, organizations must proactively review and update their security measures, addressing vulnerabilities across all aspects of the risk triangle.
3. Overcoming reactive security approaches
Many organizations struggle to access real-time insights from enterprise telemetry. Their reliance on siloed tools and manual processes makes it difficult to identify unknown risks, preventing them from becoming proactive with risk mitigation.
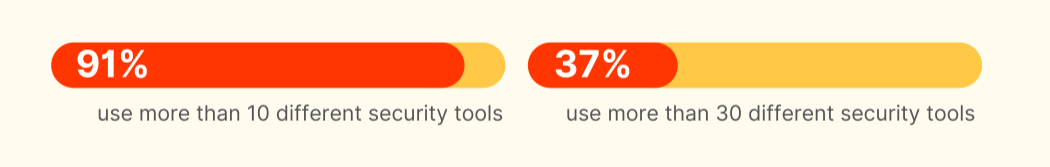
4. Security tool proliferation shows no signs of slowing down
A staggering 91% of respondents use more than 10 different security tools, with 37% using more than 30. Despite these investments in these tools, over half of the respondents still face challenges with data engineering and detection engineering.
5. Top security tool investments: SIEM, cloud security, SOAR
Respondents are prioritizing their investments in these three areas.
- Security information and event management (SIEM). There is a noticeable shift from legacy, on-premises SIEMs to cloud-native SIEMs and security data lakes. This transition offers cost-effective data ingestion and rapid threat detection capabilities.
- Cloud security. The widespread adoption of public cloud services has led to increased vulnerabilities and breaches. So, in response, security teams are heavily investing in cloud security tools to protect cloud-native workloads.
- Security orchestration, automation, and response (SOAR). For many, SOAR tools are becoming essential for automating incident response and minimizing the impact of security breaches.
6. Tool stack optimization is a priority
Before investing in additional tools, 36% of respondents plan to optimize their existing tool stack. They evaluate the effectiveness of current tools by analyzing metrics such as the reduction in security incidents, response velocity, and incident recovery time. This focus ensures that future investments are targeted and effective at enhancing overall security posture.
Ways forward: Key actions for security leaders
As a security leader or practitioner, you can transform your current challenges into opportunities by shifting security operations from reactive to proactive and adaptive. Consider these actionable strategies.
- Focus on outcomes aligned with business goals. Shift your focus from managing tools to achieving business outcomes.
- Prioritize and monitor critical assets. Identify and categorize assets based on their business impact.
- Leverage data analytics, AI, and automation. Enhance security operations through refined data and advanced data analytics.
- Strategically consolidate tools. Improve visibility and integrations while cutting costs.
Dive deeper: Access the full report
Our Hybrid SOC and Security Tools Strategy Report 2024 comprehensively analyzes how organizations adapt their security strategies to address emerging threats and operational challenges. Gain valuable insights to help you navigate the complex security landscape with enhanced defenses.
Don't miss out on these crucial insights – download the full Hybrid SOC and Security Tools Strategy Report 2024 now and stay ahead in the ever-evolving world of cybersecurity.
Related Articles
Subscribe for updates
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.







