1 min read
Redefining Cybersecurity ROI: From Tool Accumulation to True Resilience
In the ever-evolving landscape of cyber threats, it's not surprising that organizations are expanding their cybersecurity budgets to fortify their...
Read More1 min read
In the ever-evolving landscape of cyber threats, it's not surprising that organizations are expanding their cybersecurity budgets to fortify their...
Read More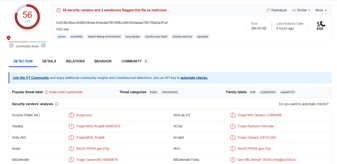
8 min read
This article is not an in-depth reverse-engineering analysis of a ransomware variant. Rather, it discusses the methods and different techniques...
3 min read
Beaconing attacks can be difficult—but not impossible—to detect. The more you know about these stealthy attacks, the better you’ll be able to...
2 min read
With the rise of generative AI models, the threat landscape has changed drastically. Now, recent activities on the Dark Web Forum show evidence of...
1 min read
Netenrich has entered into a strategic partnership with Cybriant, a leading managed security services provider (MSSP) that serves more than 1,400...

3 min read
To keep an enterprise up and running, security is essential—and no doubt, why security teams keep more than busy. Day in, day out, they are...

2 min read
The internet is a goldmine — but also a jungle — of threat intelligence. You can certainly turn to it to track exploits, vulnerabilities, and...

2 min read
Detection engineering is the process of designing and implementing systems, tools, and processes — for example, security information and event...

3 min read
User entity and behavior analytics (UEBA) has been great at solving some significant shortcomings of SIEM (security information and event management)...

4 min read
According to the Gartner report, “Automated moving target defense (ATMD) technologies are paving the way for a new era of cyber defense...
















The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.