6 min read
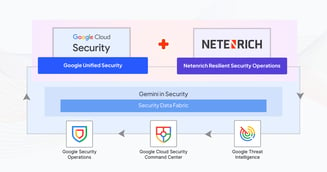
From Data to Decisions: Enhancing Situational Awareness in Security Operations with Data Analytics
Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
Read More