3 min read
Agentic AI for SecOps: Turbocharge Your Security Operations
The Rise of AI Agents for Cybersecurity in 2025
Cybersecurity in 2025 faces an unprecedented wave of AI-augmented threat actors. Attackers leverage...
Read More3 min read
The Rise of AI Agents for Cybersecurity in 2025
Cybersecurity in 2025 faces an unprecedented wave of AI-augmented threat actors. Attackers leverage...
Read More
6 min read
Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
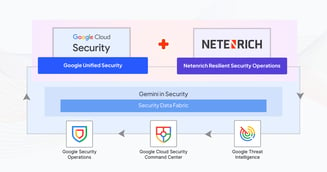
3 min read
Security leaders today aren’t just defending infrastructure. They are protecting business continuity, customer trust, and innovation at scale. The...

2 min read
April 28 – May 01, 2025 | San Francisco, CA | Moscone Center
Booth #6376 | North Expo.
AI could not get here fast enough. By 2028, humanity's...

1 min read
Google Cloud Next ‘25 is where innovation in the cloud takes center stage, and Netenrich is set to steal the show. If you’re looking to...

2 min read
Security teams drowning in alerts and starving for insights? DevOps slowed down by security roadblocks. Cloud environments still feel like the...

5 min read
The rise of sophisticated attack vectors, such as advanced persistent threats (APTs), ransomware, and zero-day exploits, has completely transformed...

3 min read
We believe the latest research by Gartner has made one thing clear: the vision of a fully autonomous SOC remains unrealistic. Although automation...

6 min read
The Chief Information Security Officer (CISO) role has transformed from being purely technical to becoming a strategic business leader. Today's CISOs...

4 min read
The increasing complexity and scale of cyber threats—fueled by AI and sophisticated tactics—have forced organizations to rethink how they secure...
















The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.