From Data to Decisions: Enhancing Situational Awareness in Security Operations with Data Analytics
Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
4 min read
![]() Netenrich
:
Wed, Jan 05, 2022 @ 12:00 AM
Netenrich
:
Wed, Jan 05, 2022 @ 12:00 AM
Digitalization initiatives evolved faster than digital operations in 2020, and 2021 widened the gap even further. But maybe that was a good thing.
Accelerated transformation made some things crystal clear, like the fact that the old approach to IT and security operations (SecOps) – buying more tools and hiring more talent – is no longer an option. Most companies have more than enough tools and too few qualified experts to run them as it is.
Once we accept that the old approach has hit the wall, CIOs and CISOs can take a step back and contemplate the best way forward. Clearly, the new approach must be rooted in data that lets us drive greater value from existing investments while making life better for business’s unsung heroes, our digital ops experts.
At Netenrich, we’ve been coming up with new ways to up-level ops for years, with a focus on making things “just work,” and work harder, for your business. As we roll out our Resolution Intelligence platform, we wanted to share some New Year’s resolutions that might prove useful in keeping your business, risk, and ops aligned (we especially like number 7).
Here goes:
You bought the tools, you get the alerts, maybe you built your own SOC or called in experts to run tests and identify problems. The question now becomes: what should you do, and do first, with all this great data? AI helps tamp down the noise, automation helps reduce the workload, but are all the machines really making you safer at the end of the day?
Now more than ever, strategic SecOps requires focus that only comes from understanding your true situation with regard to risk. Think of this as the relationship between your assets, exposures, and security controls at any given time.
Look to approaches rooted in ongoing cyber situational awareness to help shift your ops focus, if needed, from one that revolves around incidents and events to one that revolves around business risk and impact.
To keep ops aligned with risk, you first need to understand what, when, and where your most valuable assets might become compromised. The first step is identifying and ranking your high-value assets.
Next you need a timely, comprehensive view of your internal and external exposures – vulnerabilities, exposed services, typosquatted domains, compromised emails, remote user devices, and others. Here’s where the models come in.
Defenders need a consistent, highly automated means of charting the paths attackers might take from an individual internal or external exposure to reach specific assets. Threat modeling continues to rise in appeal within organizations of all sizes as a way to prioritize efforts ranging from patch management to threat hunting and incident response.
You can never have enough models, but the real gold lies in pulling all the models together into a single view and using the resulting situational awareness to apply or adjust controls. Spending more time with models lets you make and keep another valuable resolution . . .
The traditional approach to SecOps heavily emphasizes time to respond, but this becomes somewhat of an arbitrary metric unless you know how fast you need to respond to avert calamity. With the onset of RiskOps, the “true north” metric for security must become mean time to compromise (MTTC).
How long will it take, or how much time do you have to act before an attack progresses to the point of compromise? Threat modeling plays a key role in understanding, quantifying, and actioning time to compromise to ruin an adversary’s day.
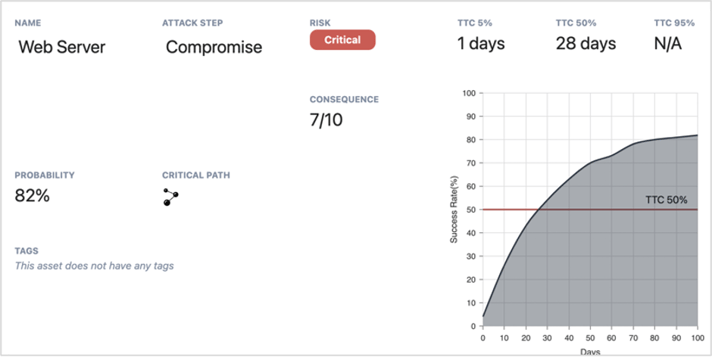
The result of comprehensive modeling, the dashboard shown above tells defenders there is a 50% chance of a known exposure leading to a web server becoming compromised within 28 days – if the team takes no action. Drilling down to see the pathway along which said attack would progress lets responders jump in and take steps to extend time to compromise.
Once you understand MTTC, your team can make attackers’ jobs harder and defenders’ jobs easier. Ideally, your environment becomes less attractive and profitable as a target (hackers’ time is money, too!) and the bad guys just move on.
The sad but undeniable reality of cybersecurity has always been that there’s not enough time to do everything. Ever.
Understanding MTTC also makes it easier to prioritize your team’s efforts. Seeing that there’s only an 8% chance of a particular compromise taking place within one day might suggest prioritizing other efforts to mitigate risk that might escalate much faster.
Defenders’ only hope of catching and or keeping up with accelerated digitalization is being able to prioritize efforts around what matters most. And where necessary . . .
A recent Dimensional Research survey shows a high percentage of enterprises have adopted a hybrid approach to SecOps by engaging managed security service providers (MSSPs) to complement or offload certain functions from internal IT teams. We expect this model to grow rapidly as enterprise security budgets remain effectively flat, skills in short supply, and digital attack surfaces ballooning through the clouds and into the stratosphere.
For mid-market organizations in particular, success will hinge upon defining when and what to outsource to increase ROI on existing investments, strategically apply automation, and free L1 and L2 engineers to progress to L2 and L3 activities.
And the overall business to . . .
Security vendors (rightly) have been saying for years that it’s not a question of whether you’ll get breached, but when. The question then becomes: how badly will you be hurt before you get back up and running? Or, “how fast can we get back up?”
Wildly accelerated digitalization makes being able to answer this question an actual thing. You can’t order a grilled cheese in a pub these days without pulling up the menu on your smartphone, let alone deliver a stable user experience to remote workers worldwide.
Digital resources need to stay up, period, and your business is only as resilient at its IT environments and operations. Improving resilience should be our primary goal for 2022, enabled by the preceding five, with a new echelon of data-driven analytics helping to raise the bar for monitoring, detection, and response.
We could have ended with any number of buzzwords – availability, uptime, tool rationalization – or platitudes about attitudes. Instead, we’ll suggest doing what you can to keep risk aligned with ops and to improve the “day in the life” of your front-lines IT and security professionals.
Automating or offloading L1/L2 efforts to whatever degree makes sense goes a long way and we’d be happy to hook you up with one of our awesome partners. Even so, coffee remains a staple of digital operations – so buy the best.
As for the chocolate, well, consider it a Zen thing; small pleasures and what have you. If you’ve made a conflicting resolution to cut down on sugar, let us know. Palatable, low-risk options (that don’t taste like dust mites) pop up all the time. Also, dark chocolate is good for you.
Whatever your goals for 2022, Netenrich would be happy to hear more and help advance the ones that can benefit through effective, risk-aligned digital ops.
We’ll bring the coffee.
Netenrich Contributors: Chris Morales, Simon Aldama and John Bambenek.
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.

Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
Security leaders today aren’t just defending infrastructure. They are protecting business continuity, customer trust, and innovation at scale. The...

April 28 – May 01, 2025 | San Francisco, CA | Moscone Center Booth #6376 | North Expo. AI could not get here fast enough. By 2028, humanity's...