From Data to Decisions: Enhancing Situational Awareness in Security Operations with Data Analytics
Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
Visit Netenrich at booth #4241 in Moscone South Expo during RSAC in San Francisco on April 24 - 27, 2023. Netenrich will present and demo Resolution Intelligence Cloud™, our cloud-native data analytics platform for managing secure operations at the scale and speed of Google. See how Resolution Intelligence Cloud transforms your security data (Cloud, data center, on prem) into intelligence you can act on — before critical issues occur.
Check out our RSAC welcome page with helpful info and links.
Register here for a free expo hall pass using code 52ENETENRXP or get a $150 discount on a full conference pass using code 52FCDNETENR.
Mingle with security’s finest from Netenrich, Google Chronicle, and more. Join us after hours on Wednesday, April 26th from 6:00 p.m. - 9:00 p.m. at Nightingale, a retro-cool San Francisco bar just a short walk from Moscone.
RSVP here, and we’ll send your confirmation for entry.
Our security experts have decades of experience with all the cybersecurity tech out there. They know what works and what doesn't, especially when it comes to security at scale. Meet with them and learn how Resolution Intelligence Cloud, leveraging Google Chronicle, changes the game with Google scale and speed. Request a meeting here, and we'll pair you with the right expert to answer your questions. You're always welcome to drop by booth #4241 anytime.
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.

Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
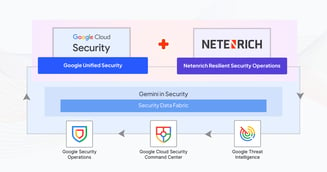
Security leaders today aren’t just defending infrastructure. They are protecting business continuity, customer trust, and innovation at scale. The...

April 28 – May 01, 2025 | San Francisco, CA | Moscone Center Booth #6376 | North Expo. AI could not get here fast enough. By 2028, humanity's...