Security Data and Context is All that Matters
Jonas Kelley, Google Cloud's Head of MSSP Partnerships, shares his thoughts on the importance of context and data in security.
Watch nowNetenrich delivers complete Resolution Intelligence to transform digital operations into smarter business outcomes. The solutions integrate with more than 140 market-leading IT and security applications to drive digital transformation, mitigate brand exposure, increase efficiencies, and bridge skills gaps.
Jonas Kelley, Google Cloud's Head of MSSP Partnerships, shares his thoughts on the importance of context and data in security.
Watch now
Jonas Kelley, Head of MSSP Partnerships, Google Cloud, answers John Pirc, VP of Product Marketing at Netenrich, about the top threats organizations...

The Head of Product Marketing at Google Chronicle, Sharat Ganesh, offers his forecasts for the most important security concerns in the year 2023.

Sharat Ganesh, Product Marketing Head at Google Chronicle, highlights the significance of bridging the IT-security operations gap. He underlines the...

Sharat Ganesh, Head of Product Marketing at Google Chronicle, asks John Pirc, VP of Product Marketing at Netenrich, about their partnership with...
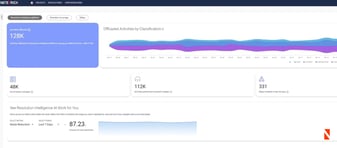
Resolution Intelligence Cloud boosts digital ops productivity with AIOps and automation while giving you comprehensive observability across IT and...
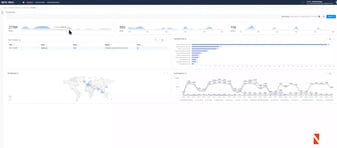
Join David Swift, Netenrich's Principal Cybersecurity Strategist and Platform Evangelist in this feature walkthrough of Resolution Intelligence...

Many organizations overlook too many of their digital assets when it comes to managing your security perimeter. Does your perimeter include your...
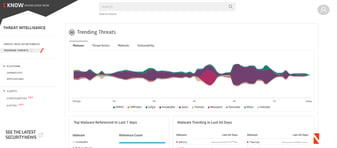
Simon Aldama, a Netenrich Advisor, demonstrates Resolution Intelligence's Cyber Situational Awareness modules in this demo.

Netenrich's Resolution Intelligence streamlines incident management to avoid future disruptions and provides cyber resilience for digital operations.
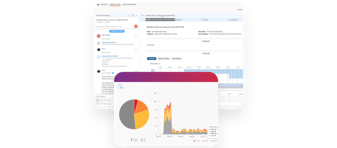
Continuing to buy more tools and hire more people does not necessarily lead to better security. While it may improve security postures in the...

John Bambenek, Principal Threat Hunter, explains how low-detection phishing kits are being utilized to circumvent multifactor authentication (MFA).
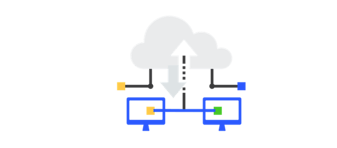
SOC teams are suffering from overwork while threats, infrastructure, data, and business transformation continue to expand. Relief is here. Join this...

















The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.