From Data to Decisions: Enhancing Situational Awareness in Security Operations with Data Analytics
Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
4 min read
![]() Liza Kurtz
:
Tue, Oct 26, 2021 @ 10:33 AM
Liza Kurtz
:
Tue, Oct 26, 2021 @ 10:33 AM
Newly available survey results from Dimensional Research confirm the growing need—and appetite—for security operations (SecOps) to become more proactive and risk-driven. This sounds obvious in theory if not in practice.
The more interesting and promising findings seem to indicate that this vital shift may now be occurring, or at least imminent. Here’s why we think so . . .
Risk is bad, ransomware is off to the races, and Work From Home made everything worse. But what does that really mean and what will it take to fix it?
For starters, 83% of survey respondents from companies of all sizes said their business would incur major damage if an outage lasted more than 24 hours. Sixty percent (60%) believed they would experience significant loss within just 8 hours.
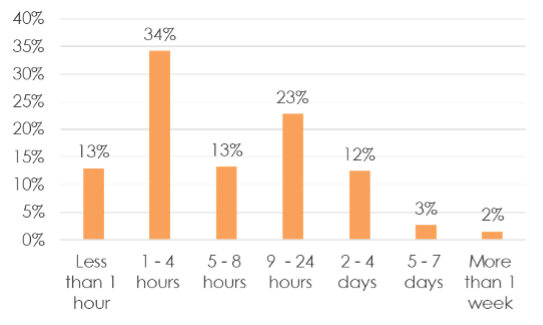
How long can your company be down from an outage before experiencing major damage to your business?
Despite that stark realization, nearly 60% of respondents said 30% or less of their IT budget currently focuses on security. Worse yet, the majority do not foresee major budget increases in the wake of the pandemic.
So, if risk is accelerating while budgets flatline by comparison, how do we bridge the gap and align risk with operations once and for all?
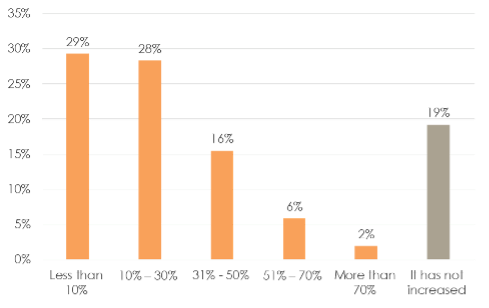
How much of your security budget increased as a result of Covid?
When asked how they plan to improve cybersecurity, participants’ number one response was “upgrade tools” (67%). That said, most report serious issues around tool integration and a lack of skills to integrate and manage them.
Again, barely a third (35%) plan to invest to fix the problem by hiring more experienced staff. We can attribute this to several factors – the low budget growth described above, an overall dearth of available talent, and perhaps the growing realization that more is not better. Doing the same things in the same ways we’ve been doing them for decades won’t solve The Tool Problem, or make companies notably safer.
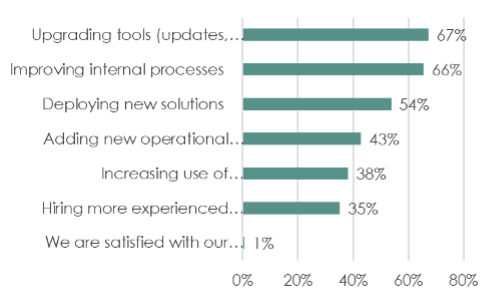
How is your company planning on improving its cybersecurity posture?
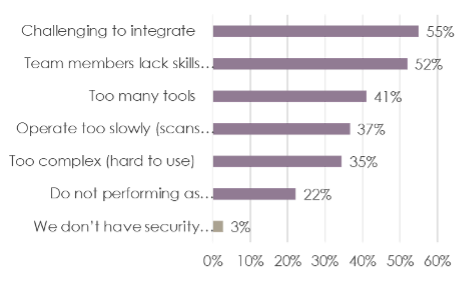
What are your company’s biggest pain points with security tools?
The Definition of Insanity.
The sum total of these trends – huge impending risk from security outages, modestly increasing budgets, lack of available skills, and perennial tool challenges – points to an obvious and urgent to do something different. Survey findings imply the shift might include pivoting from reactive, alert-driven security operations (SecOps) to adopt a more proactive, risk-driven stance.
While the value of understanding risk seems clear, less than one-third of respondents believe IT and security operations are completely aligned with regard to managing risk. So, how do we do it and what should that alignment look like?
Respondents expressed a strong desire to spend more time managing risk (number 1 answer), researching incidents, and modeling threats. Doubling down on traditional SecOps tasks like patching and analyzing alerts holds less appeal, partly because these activities prove tedious, and perhaps also because their value can be hard to quantify.
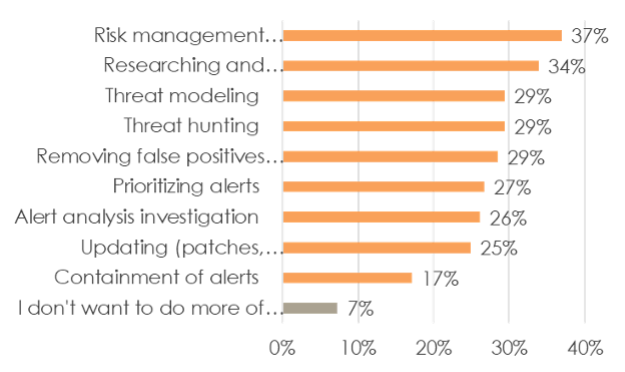
Which of the following security tasks do you personally want to do more of?
Being able to prioritize threats according to their potential impact on the business goes a long way toward managing risk. Among the impact they fear most respondents cited loss of data and weakening customer relationships. This, combined with the aforementioned findings about outages leading to significant damage very quickly makes a strong case for improving resilience with a focus on high-value assets.
Netenrich Resolution Intelligence solutions for cyber resilience begin by helping organizations identify and mitigate risk to their most critical business assets and functions (the “crown jewels” of the organization if you will). Our approach includes modeling threats and emulating adversaries to quantify the predictable Time to Compromise (TTC) high-value assets. Doing so over time keeps risk aligned with available cybersecurity resources and equips defenders to intercept and disrupt the most devastating attacks first.
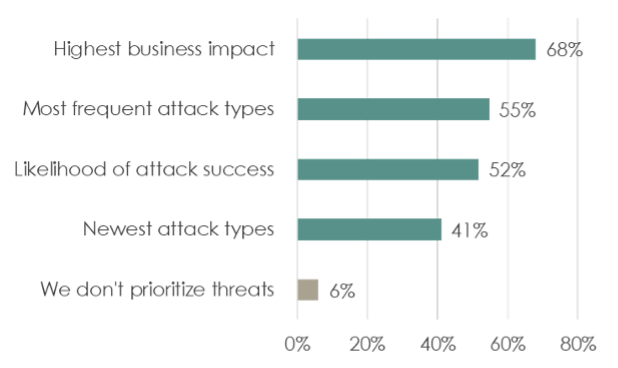
Respondents agree that the ability to prioritize in this way is key, but detailed questions about SecOps reveal they’re not yet well-positioned to do so.
Developing a rich, continuous threat modeling practice marks a powerful juncture in pivoting from event- or alert- to risk-driven cybersecurity. When asked to elaborate on the value of threat modeling, respondents expressed a clear desire to become more proactive and to determine the likelihood and cost of an attack succeeding.
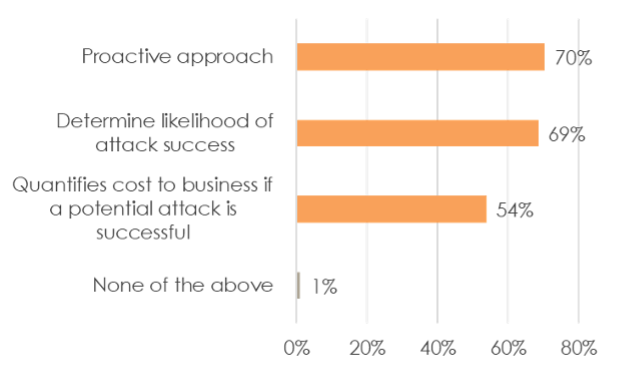
Which aspects of threat modeling would be beneficial for your company?
Despite the perceived benefits, less than 40% of respondents say they currently use threat modeling to manage their dynamic digital attack surface. More than half say their company only performs threat modeling on a monthly (or even less frequent) basis, and 15% have not yet adopted the practice at all.
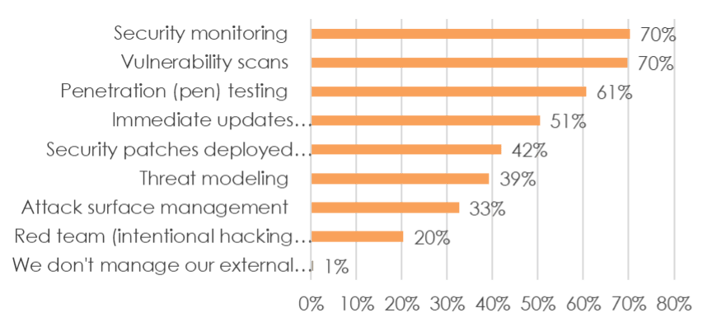
Forty-seven percent (47%) of respondents have engaged managed service providers (MSPs) to help run security, but just 17% say MSPs are engaged in threat modeling. And last but not least, only a third of respondents currently leverage external attack surface management (ASM) which plays a critical role in focusing proactive threat modeling efforts.
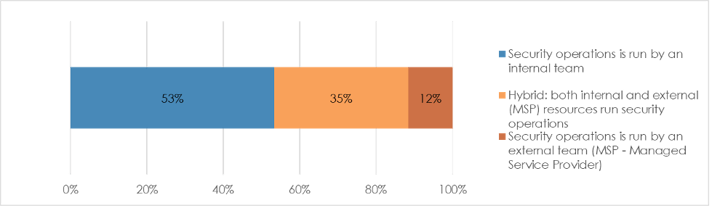
For the moment, the current approach is . . .
Or at least, too slow and sporadic. Forget about defining a new “gold standard;” keeping risk aligned with SecOps practices needs to become the norm, right now.
But there’s no need to go it alone. Increased use of automation and MSP partners to offload repetitive, time-consuming tasks like patching and removing false positives should free up internal cycles so defenders can pursue higher-value efforts such as threat hunting, threat modeling, and ASM – or these too can be offloaded.
Whether an internal or hybrid approach is used, Risk Posture Management must be cohesive and continuous. Netenrich maintains a focus on keeping threats, assets, and defenses aligned by correlating asset profiles with threat and attack surface intelligence so defenders understand risk in context and get alerted when their dynamic threat landscape changes.
We’ll be delving deeper into best practices for threat correlation and modeling, adversary emulation, and prioritization mitigation strategies in the weeks to come. In the meantime, check out the full report for more detail about what types of threats defenders fear most and how they are (and aren’t) preparing for them.
Netenrich cybersecurity and threat modeling experts would welcome the chance to explore your unique threat landscape and how and our approach lets you make hackers work harder while defenders work smarter.
Netenrich’s John Bambenek talks more in-depth on the need for a risk-aligned security approach in an upcoming webinar with David Gehringer, Dimensional Research analyst, on Wednesday, November 10, 2021, at 10 AM (PT). Download the executive summary by Dimensional Research.
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.

Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
Security leaders today aren’t just defending infrastructure. They are protecting business continuity, customer trust, and innovation at scale. The...

April 28 – May 01, 2025 | San Francisco, CA | Moscone Center Booth #6376 | North Expo. AI could not get here fast enough. By 2028, humanity's...