Automate the Known.
Discover the Unknown.
End the reactive cycle of tool and alert fatigue. Automate your response so your team can focus on proactive discovery, a stronger posture, supercharged risk coverage, and measurable outcomes.
Shift to AI-powered, Adaptive Security Operations | Powered by Google SecOps
Prepared Isn’t a Buzzword. It’s Measurable.
See what happens when your SecOps shifts from reactive firefighting to proactive, intelligent defense with Netenrich.
Delivering Real-world Outcomes for Global Enterprises
Don’t take our word for it – hear directly from our customers about how we transformed their security operations.
"Netenrich has transformed our security operations by delivering meaningful and measurable results. Their Adaptive MDR solution slashed our annual security costs by over 50% while reducing our response times to an impressive 15 minutes. With enhanced detection performance and a scalable framework, we are better equipped to safeguard our business and proactively adapt to future security demands."
Andy Nallappan
President and COO, Cloud Software Group
"Netenrich brought unparalleled clarity and control to our once-complex security environment. By consolidating over 40 playbooks into just three streamlined workflows and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-driven approach has ensured our operations align seamlessly with our growth strategy."
Kumar Palaniappan
CISO
"Netenrich’s Adaptive MDR has fundamentally improved our security performance, drastically reducing manual interventions from nearly 2,000 incidents per month to fewer than 10! Their advanced threat detection and automation capabilities allow us to scale securely while proactively addressing threats."
Mohan Sekar
Sr. Director, Head of Product Security




Netenrich Adaptive MDR
Security without limits, without complexity, without disruption
Netenrich Adaptive MDR delivers AI-powered, expert-led security that evolves with your business. Gain complete visibility, simplify operations, and manage risk across your existing tools through a unified security operations platform. We help you ingest everything, detect what matters, and respond with confidence. Reimagine your SOC with Netenrich and Google SecOps.
Unified Visibility & Context
Break down silos across SecOps, DevOps, and CloudOps to understand your environment, from CI/CD to APIs.
Smarter, Faster Response with Adaptive AI
Detect and respond in real time with AI that learns from behavior and relationships, not just static rules.
Proactive Risk Reduction
Uncover hidden threats and strengthen security posture with always-on analytics and threat intel from Mandiant, Google, and more.
Efficient, Scalable Security Ops
Automate playbooks, workflows, and response actions with built-in SOAR capabilities.
Clarity Backed by Experts
Stay ahead with real-time dashboards and 24/7 support from our detection and investigation teams.
.png?width=500&height=500&name=Untitled%20design%20(3).png)
Unifying Forces: Netenrich and Google Cloud Security
The Google tech stack is more than just tools - it’s a strategic foundation for enterprise security. Netenrich combines agile engineering, deep data science, and Google’s elite SecOps stack, including Gemini AI and real-time threat intelligence. We deliver cloud-native security that scales with your business and drives measurable outcomes across cloud and hybrid environments.
By integrating Google's advanced AI infrastructure with our data-driven security operations, we deliver a collaborative ecosystem of tools and controls to secure a modern, distributed enterprise.
Check how we Power the Modern SOCUpgrading your SOC with Google SecOps?
Supercharge Your Security Operations with Netenrich SecOps Solutions
Adopt, optimize, and scale Google SecOps at cloud speed. From seamless migration to continuous detection and automated response, Netenrich delivers expert-led, intelligence-driven security.
.png?width=379&height=117&name=Group%20757%20(1).png)

SecOps Implement
One-time implementation & migration engineering for Google SecOps
- Seamless SIEM migration
- All-inclusive security engineering
- Rapid deployment
SecOps Operate
Annual engineering for implementing & operationalizing Google SecOps
- Derive continuous SIEM value
- Proactive security engineering
- Strategic security planning
The Netenrich Difference –
Make Data Your Security Advantage
Transform fragmented data into actionable insights and make smarter security decisions. Netenrich reduces risk, boosts operational efficiency, and delivers scalable SecOps outcomes aligned with your business priorities.
Reduce Noise. Prioritize What Matters
Ingest, normalize, and enriches all entities, assets and security telemetry from diverse sources to protext everything.
Intelligent Data To Analytics
Continuous signal analytics, detection lineage, ensures organizations proactively uncover and defend against latest threats and know security health over time.
Bridge the Unknown Threat Gap
Behavioral and anomaly-based detection, entity enrichment, and threat impact modeling for proactive, adaptive SecOps
From Code to Cloud to SecOps
Unifies DevOps and SecOps to enchance security, speed threat detection, reduce risk, and ensure compliance-without slowing innovation
Featured Resource
A CISO Playbook for 2025 and Beyond Reactive Security
Security operations can’t run on hope, SIEMs, or spreadsheets anymore. This guide equips executive leaders to drive outcome-focused SecOps: powered by AI, contextual risk, and cloud-native data strategies.
Comprehensive, proactive data analytics approach to risk management
The growing volume and complexity of data flowing in and out of organizations have created new challenges in managing digital risk. Existing SIEM solutions cannot scale with the velocity of data growth, without taxing security budgets and draining existing resources.
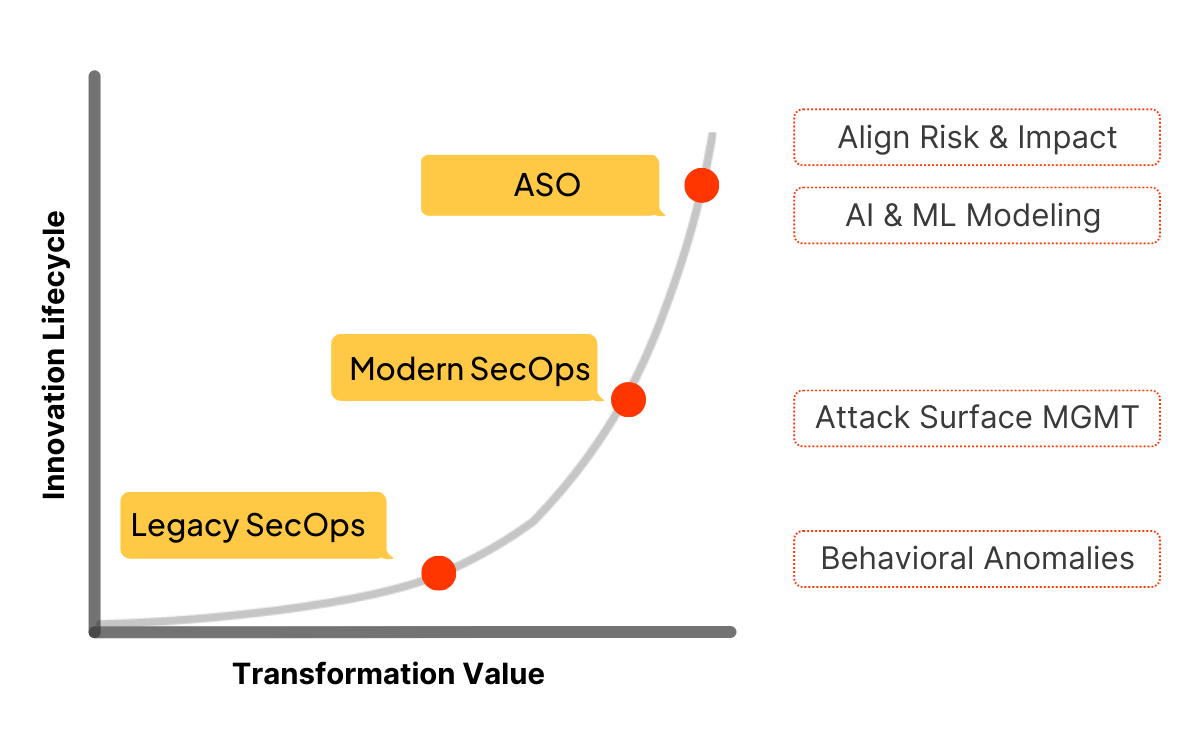
How to achieve ASO with Resolution Intelligence Cloud
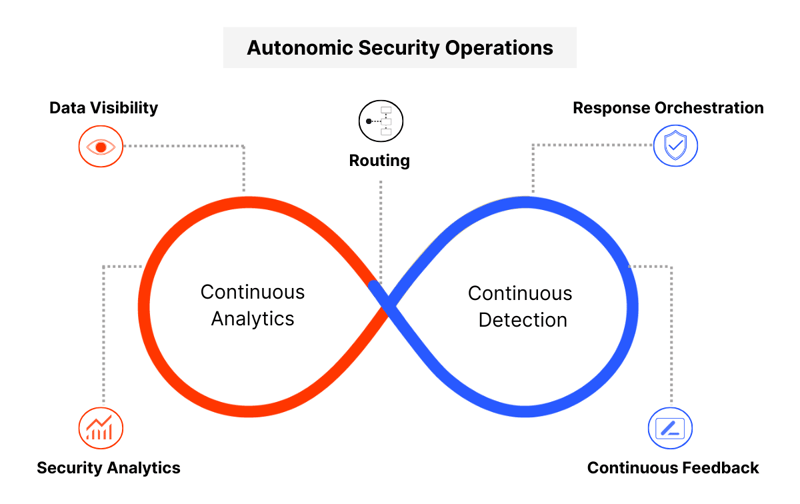
Reinvent security operations — to reduce noise, raise fidelity through continuous adaption and redesign
Autonomic Security Operations is a continuous “discovery, analysis, routing, resolution, and improvement” loop enabled by Resolution Intelligence Cloud.
It starts with data visibility (what’s in the environment) and continues with security analytics (what’s it doing), intelligent routing (who should care), response orchestration (what to do), and continuous feedback (how to make it better).
- Ingest all security and operations data.
- Gain situational awareness and a complete operational picture.
- Quantify and prioritize risk of digital services based on impact.
- Provide key stakeholders with timely, actionable intelligence.
- Automate low-level tasks.
- Quickly and efficiently respond to security incidents.
- Discover patterns and risky behaviors before incidents occur.
- Proactively address risk and minimize impact.
- Conduct root cause analysis, and validate models, parsers, rules.
- Facilitate a culture of control engineering.
Accelerate time to value now
Align security operations to your business
Insights to act on
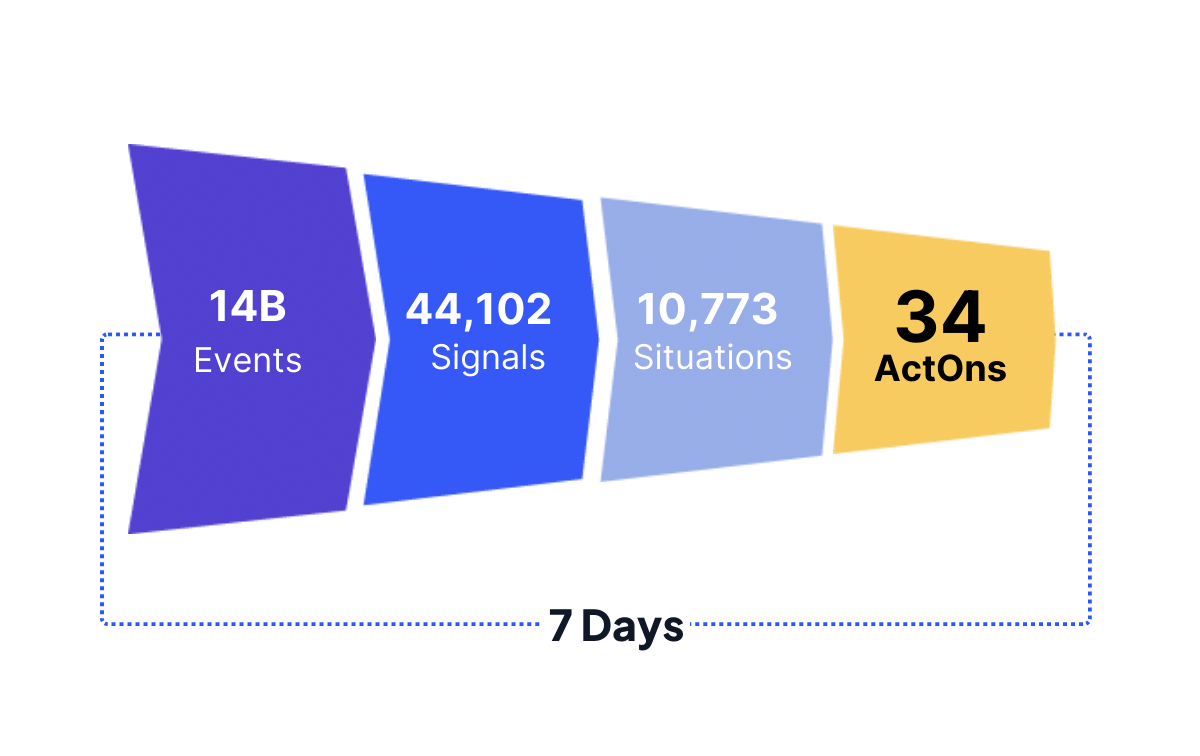
Stop the barrage of alerts. ActOns correlate alerts with asset and user data so you can act decisively on what matters now.
Prioritize by business risk
Save time and sanity: know where to focus and stop chasing false positives with priority scores aligned with business risk.
Advanced analytics
Detect unknowns with advanced anomaly detection, analytics, and ML across real-time data from hybrid cloud environments.
Collaboration war rooms
Create secure war rooms to collaborate with colleagues, customers, and others in a single place with extensive context.
Threat intel & detection
Discover top vulnerabilities and map threat trends with Threat Analytics Services, vulnerability disclosures, and advisories.
Fast resolution
Automate investigation and remediation tasks while providing your SOAR and ITSM with enriched context for faster resolution.
“Whether it’s identifying potential vulnerabilities in the environment, accurately tracking assets of all shapes and sizes, or responding to suspicious activity with detailed, automated actions, Resolution Intelligence Cloud combines the functionality of Extended Detection and Response (XDR); Security Orchestration, Automation, and Response (SOAR); Security Information and Event Management (SIEM); and asset management platforms all in one place.”
“We are finally able to scale our security operations and can now focus on what matters most: turning data into prioritized action. The platform gives us a new way to use data analytics and automation to improve how we manage risk and secure the business.”
“This new and modern ASO approach with Netenrich will allow us to scale more efficiently while also increasing customer satisfaction and accelerating business growth.”
Finally, more data is good
When CIOs and CISOs hear “more data” they think “higher cost” – but those days are over. So stop limiting data ingestion. Don't miss important signals. Stop usage-based costs that skyrocket unpredictably. Stop the flood of alerts and constant firefighting.
With Resolution Intelligence Cloud, more data is great.
- Ingest all your data across security and digital ops for comprehensive observability
- Detect patterns, issues, and important anomalies faster
- Threat hunt
- Have the right context to take action on what's most important
- Eliminate noise
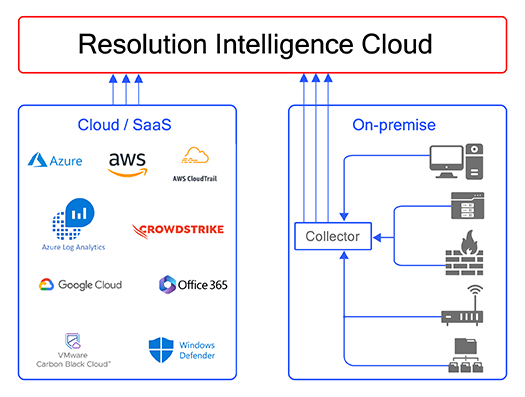
Work from a common operational view
Siloed security and digital ops leads to gaps and inefficient duplication of tools, processes, and people. Resolution Intelligence Cloud provides a common operational view and situational awareness aligned to business risk. And it facilitates collaboration within and between teams.
- Strengthen your security posture
- Improve performance and up time
- Boost analyst effectiveness
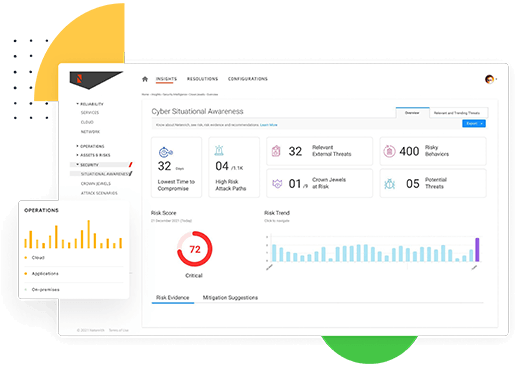
Out-innovate hackers with anomaly detection & situational awareness
Hackers are relentlessly innovative. It's futile to fight them with traditional, reactive methods.
- Identify unknowns without detection rules with advanced anomaly detection (think next-next-gen UEBA)
- Be proactive with actionable insights from data over time, correlated and mapped to the MITRE ATT&CK framework
- Identify and resolve what matters most to the business — stop wasting time on alert noise
- Communicate across functions and coordinate response fast
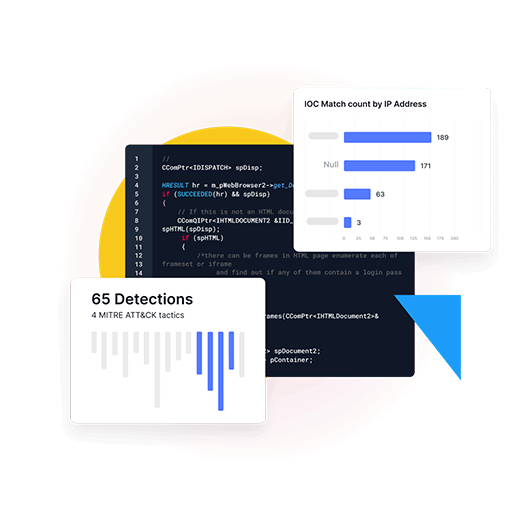
Outcomes: Improved SLAs and metrics
Lower Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) with Netenrich AI-enhanced Intelligent SOC, offering 95% SLAs
From events to signals to situations to incidents, Netenrich AI-enhanced Intelligent SOC crunches the numbers, pinpoints focus.