From Data to Decisions: Enhancing Situational Awareness in Security Operations with Data Analytics
Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
4 min read
![]() Netenrich
:
Tue, Feb 16, 2021 @ 11:17 PM
Netenrich
:
Tue, Feb 16, 2021 @ 11:17 PM
 How Attack Surface Exposure (ASE) accelerates resolution of digital risks. Pen testing? Pfftt! Try ASE and say goodbye to pen-testing. Forever. ASE was awesome before, but it’s now running on steroids. Risk scores, risk rules, recommendations, and auto-closures now make staying ahead of attackers so much easier. See the difference.
How Attack Surface Exposure (ASE) accelerates resolution of digital risks. Pen testing? Pfftt! Try ASE and say goodbye to pen-testing. Forever. ASE was awesome before, but it’s now running on steroids. Risk scores, risk rules, recommendations, and auto-closures now make staying ahead of attackers so much easier. See the difference.
JACK, short for Just Another Company for Kicks, a very real brand — just kidding — and a Netenrich customer, probabilistically speaking, have relied on ASE to measurably reduce their attack surface for a few months now. Their top need has been finding and fixing vulnerabilities in their assets exposed to the Internet. Our analysts, working with their IT guys, have helped them fix those vulnerabilities in record time, of course, but they have often said their own teams should be more enabled to do it all themselves. With ASE’s features and some much-needed enhancements to existing ones, now they can. Let’s see how.
Attack Surface Exposure for Dummies ![]()
![]()
Curious what Attack Surface Exposure is and how the defending duo of Threat and ASE help you stay ahead of attackers all the time? Read the free Dummies book by Ed Tittel to learn why Netenrich’s ASE solution powered by our native threat intelligence helps enterprises find risks before hackers and fix them quickly.
Jill, an IT admin at JACK, logs into Netenrich's Resolution Intelligence Cloud™ and heads over to ASE. When earlier she would just see a bunch of existing and fixed risks, she now sees an overview dashboard with a very orange risk score — 75, which is too close for comfort to their all-time high of — 91, immediately telling her it’s probably prime time in Hackers’ Haven.
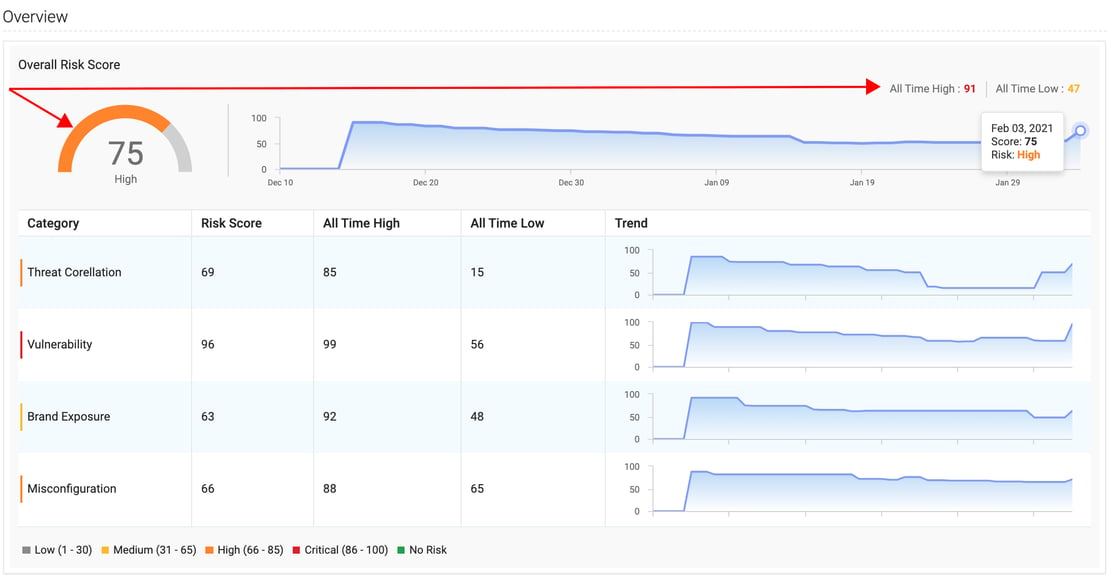
ASE now features a risk score for all your org’s external risks and plots them in an easy-to-use chart over eight weeks. Worried, she hovers over the chart next to the score and sees a spike on February 03, 2021.
“Interesting new feature, but why the spike,” she wonders.
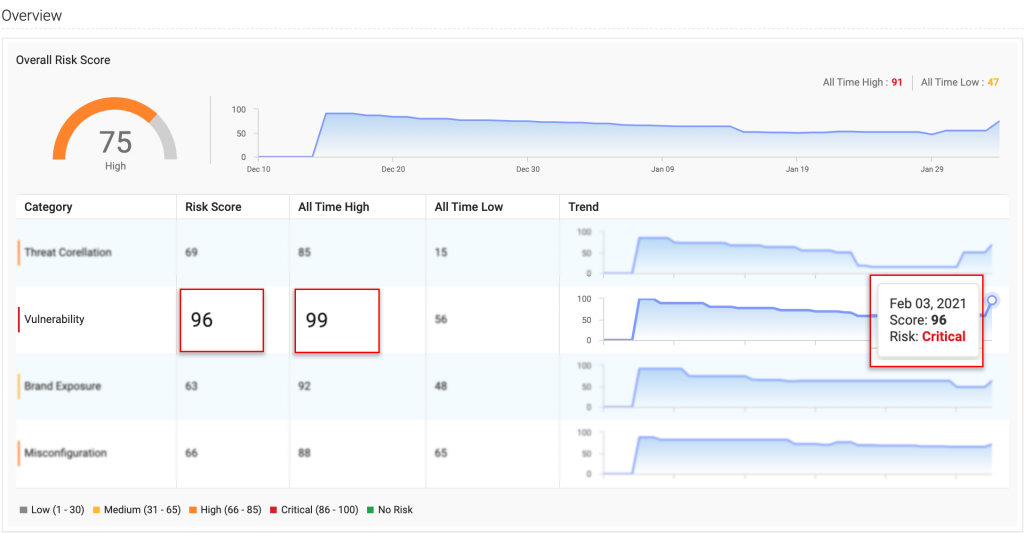
Quickly scrolling down the breakdown by the type of threats auto-categorized by ASE, she spots a similar spike in Vulnerabilities on the same day.
This new feature from ASE tells her visually and without thirty-thousand clicks which type of threat is affecting her risk score. Her next obvious step is to click through to Risks Discovered from Vulnerabilities and intuitively find that one critical risk amongst 17 others.
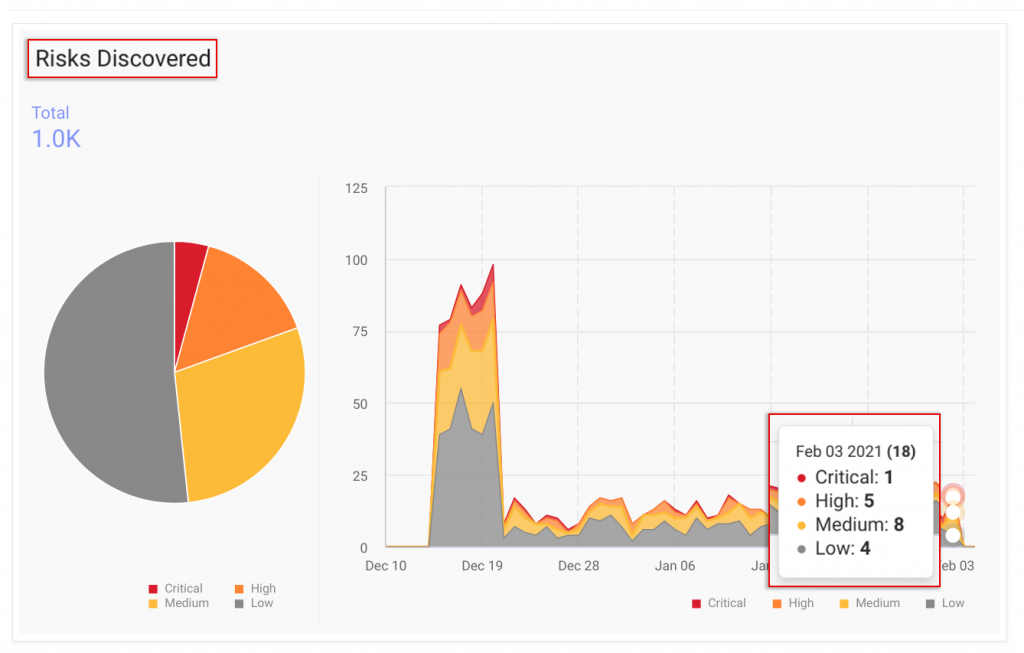
Categorization of risks by severity across four new levels in ASI — Critical, High, Medium, and Low — lets you see risks that matter the most without going through alert contexts and lines of text.
Curious about this particular risk, Jill then flips to the Overview section—note how ASI has automatically bumped up the Vulnerability risk type to 96—to find the Vulnerable Services Check crying bloody murder, an apt exaggeration for some high-risk alerts that are demanding attention. She notes 61 vulnerabilities across 453 services—read: apps—remain unpatched.
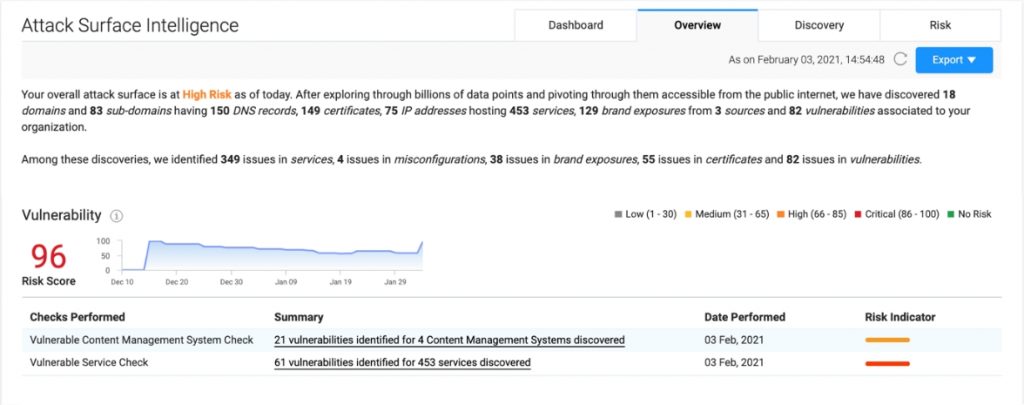
One more click, and she is now looking at the suspect caught red-handed in a list of medium-to-low-risk alerts. Or red barred. Literally. There’s one lonesome red alert on the list that’s tripping up JACK’s entire Risk Score, something Jill notes is too dangerous to let slide.

ASE now makes it easy to see which alerts are critical in a list with visual cues that range from very-light orange to bloody mu… er, dark and deep red.
Viewing the details of the alert is a one-click affair. Soon as Jill does that, a world of insight meets her. She can now see an Apache service running on an IP she is familiar with has a vulnerability with the ID CVE-2017-7679.

She also sees a bunch of risk rules triggered that show a high CVSS score, and an exploit — a way for hackers to use the vulnerability to hurt JACK. This lends credibility to the red alert and the bumped-up score of Vulnerabilities in Overview. She then sees a recommended fix for the risk, courtesy, our analysts who vet all critical alerts and team up with our machines to offer these recommendations at scale. The fix will have to wait, though. She has a little more digging to do.

ASE now shows the risk rules that get automatically triggered, courtesy, our machine learning algos, that contribute to alert status and offer additional context for prioritization
For the same IP there were other non-critical vulnerability alerts as well as seen in Alerts view. Wondering, “Why now,” she looks up the IP in ASE’s native Discovery search. Turns out, the asset at that IP was hosted on JACK’s web servers and had been alive for a while, but the Apache Web Service running on it was exposed to the Internet just a day before.

Powerful search helps you look for anything across all your data within ASE without switching screens.
Jill is riddled with questions.
She will have to park these questions later for IT and reach out to our SOC analysts for help with additional help, but for now, she has to go about upgrading the Apache Web Service to the latest version.
When she’s done, she will wait for ASE to tell her if the issue has been resolved for real or if there are niggling problems with it. Thankfully, when she does come back just a day later, she will find ASE’s found the fix good and auto-closed the alert, dipping the score of Vulnerabilities and overall org risk.

Auto-closure not only saves you the additional task of closing a ticket, but also serves as a confirmation of fixes.
In summary, for JACK to defend against the dark arts, it took a diligent Jill to fix a rather nasty risk that could have led to much damage later. A diligent Jill, less than ten clicks, and a smart patronus called ASE.
When we launched ASE, we had maybe three prospects interested in it. Today, more than twenty U.S. and global enterprises use ASE to consistently reduce their attack surface and stay ahead of hackers. We already see over forty brands in trial at a time. Our projections for this year nearly doubles that number. No-brainer then that we rely on our in-trial and paying customers to drive our roadmap toward world domination.
This major release folds a bunch of our customers’ most popular asks into five new features and enhancements that should help make ASE more DIY — our mid-term vision for the product — and super-simple to read insights, take actions, and fix risks — our immediate goal with this release.
So chill like Jill
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.

Threat actors have continued to bypass advanced security tooling despite the forecast for enterprises worldwide to spend $212 billion on defensive...
Security leaders today aren’t just defending infrastructure. They are protecting business continuity, customer trust, and innovation at scale. The...

April 28 – May 01, 2025 | San Francisco, CA | Moscone Center Booth #6376 | North Expo. AI could not get here fast enough. By 2028, humanity's...