Netenrich Adaptive MDR
Switch to an MDR That Adapts, Aligns Better, and Proves It’s Working
Go beyond reacting to alerts. Continuously engineer coverage, detection, and response to reduce real risk and deliver measurable security outcomes.
- Deeper Visibility
- Supreme Efficacy
- Streamlined Performance
Top Security Teams Are Going Beyond Traditional MDR Now
Alert fatigue remains a core challenge.
Most MDR providers continue to flood security teams with low-context signals, overwhelming analysts and obscuring real threats.

Situational awareness is missing by design.
Most MDRs don’t align/unify threat, asset, and control data, making it impossible to detect what matters or respond in context.
.png?width=75&height=75&name=Missing%20Awareness%20(1).png)
Proving what’s actually protected is still out of reach.
Legacy MDRs lack full asset and detection coverage, making it impossible to validate posture or demonstrate ROI.
.png?width=75&height=75&name=Unproven%20Protection%20lert%20Fatigue%20(1).png)
Outsourced detection alone no longer delivers value.
When MDR fails to align with an organization’s environment or business priorities, it's just another vendor, not a strategic partner.
.png?width=75&height=75&name=Outsourced%20Inadequacy%20(1).png)
The MDR benchmark has changed.
Static rules and disconnected playbooks don’t cut it. Leading teams demand MDR that learns, evolves, and drives measurable progress.
.png?width=75&height=75&name=Evolving%20Benchmarks%20(1).png)
Netenrich Enabled Citrix Boost & Align their SecOps to Business Growth
Netenrich brought an unparalleled clarity and control to our once-complex security environment. By consolidating over 40 playbooks into just three streamlined workflows in Google SecOps and boosting detection coverage by a remarkable 147%, they’ve enabled us to respond with better speed and precision. Their data-driven approach has ensured our operations align seamlessly with our growth strategy.
Kumar Palaniappan | CISO, Cloud Security Group (Citrix)
Read Case Study
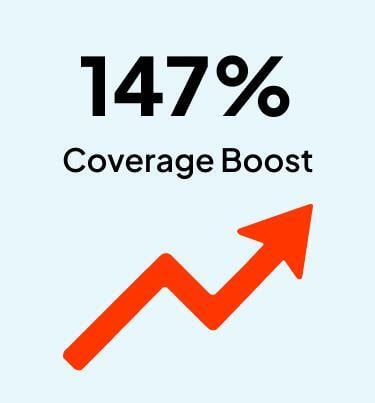
Proven Outcomes of Netenrich Adaptive MDR
reduction in manual incident handling
Less noise, more focus through automation and high-fidelity detections.
faster Mean Time to Respond
Context-driven playbooks and escalation paths accelerate resolution.
improvement in detection coverage
Mapped to MITRE ATT&CK and aligned to your real risk surface.
reduction in security operations cost
Engineering-led MDR eliminates inefficiencies and tool sprawl.
What Powers Adaptive MDR
Adaptive MDR brings together expert-led operations, structured response workflows, and an integrated technology stack - combining scalable telemetry, behavioral analytics, and AI-powered automation - to strengthen your security operations and keep business moving.
.png)
More Than a Name - Here’s What “Adaptive” Really Means
Adaptive MDR is not a static managed service. It’s a continuously evolving security system engineered to improve, tune, and align itself to your environment, risks, and outcomes.
.png)
Continuous Coverage Intelligence
- Signal analytics reveal what's working and what’s not
- Coverage maps and drift tracking identify blind spots before they become problems
- Posture recommendations delivered monthly to keep your defenses sharp
Detection and Response That Learn Over Time
- Detection rules are continuously tuned based on data quality and behavioral context
- SOAR playbooks are validated end-to-end every month, with automation usage tracked
- Custom detections and behavioral models evolve with each ActOn triggered
Data and Signal Health Monitoring
- Real-time validation of log ingestion quality and data completeness
- Issues like timestamp drift, parsing errors, or MITRE misalignment are flagged and fixed
- Ingestion trends inform detection strategy and tool optimization
Alignment With Business and Risk
- Coverage is mapped not just to MITRE, but to region-, industry-, and asset-specific threats
- Controls are prioritized based on critical assets and their real-world exposure
- Output is continuously tied to outcomes for different personas (CISO, engineering, operations)
Operational Feedback Loops
- KPIs like MTTD, MTTR, signal-to-ActOn ratio, fidelity trends, and more are tracked
- Monthly reviews and QBRs surface blockers, gaps, and emerging priorities
- Delivery adjusts dynamically based on your environment’s pace and changes
Adapt to Any Challenge, Secure All Fronts
Explore how we bring Adaptive managed detection and response services to life across modern hybrid cloud environments.

Unify Security Across Hybrid and Cloud Environments
Eliminate blind spots across your digital estate. Our Cloud MDR ensures 360° threat coverage across hybrid, multi-cloud, and on-prem environments. With scale-ready pipelines and deep data normalization, you gain unified visibility and real-time insights, no matter where your assets live.
Proactively Hunt and Neutralize Advanced Threats
Go beyond reactive alerts. Our 24/7 SOC blends AI-powered detections, threat intelligence loops, and expert-led hunting to detect and contain advanced threats. With threat coverage mapped to 92% of the MITRE ATT&CK framework , our 24/7 SOC experts don't just find threats, they anticipate them, providing you with a proactive and aggressive defense posture.


Drive SecOps Efficiency with AI-Powered Automation
Streamline operations and reduce analyst fatigue. Our managed detection and response solution leverages Google SecOps to consolidate playbooks, enrich detections, and drive risk-tuned automation. That’s how we cut manual incidents by 95% and boost playbook efficiency by 90%, allowing your team to focus on strategic initiatives.
Tailored MDR Services Because One-size-fits-all Doesn’t Work Anymore
Our MDR services are customized to your environment, ensuring scalable protection, faster response, and clear outcomes.
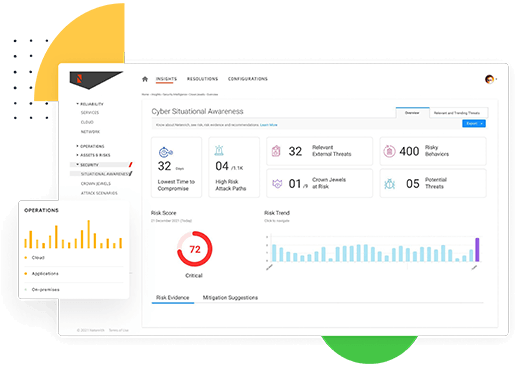
Situational Awareness That Drives Response
We don’t just monitor alerts, we understand what matters. By aligning threats, assets, and controls, we help your team respond based on real business impact, not just technical signals.
Risk Posture Alignment, Not Just Reports
We go beyond reporting. We help you track how detection coverage, control effectiveness, and risk posture evolve over time. Every update helps you improve, not just observe.

Custom MDR Dashboards
Access customized dashboards that surface the metrics that matter. Track threat activity, KPIs, and security posture in real time.

SLAs You Can Count On
Gain confidence with clearly defined SLAs for detection and response. Know exactly what’s covered, and how quickly action will be taken.

A Dedicated Security Partner
Work directly with a Customer Success Manager or Engineer. They ensure ongoing tuning and alignment to your evolving needs.

Strategic Security Reviews
Stay ahead with expert-led monthly or quarterly reviews. Identify gaps, track maturity, and drive continuous improvement across your SecOps lifecycle.

Frequently Asked Questions (FAQs)
-
What is MDR in cyber security?
MDR (Managed Detection and Response) in cyber security is a service that combines threat detection, 24/7 monitoring, and expert-led incident response to protect organizations from cyber attacks. It helps detect threats faster, reduce alert fatigue, and improve overall security posture.
-
How does Adaptive MDR differ from traditional MDR solutions?
Traditional MDRs flood your team with low-context alerts, lack visibility into what’s truly protected, and rarely improve over time.
Netenrich Adaptive MDR is engineered for outcomes, not just outsourcing. It continuously adapts to your evolving environment, aligns to your assets, controls, and risks, and delivers measurable improvements, such as a 95% reduction in manual incidents and 147% boost in detection coverage for customers like CSG.
-
What role does Google SecOps (Chronicle + SOAR) play in your MDR service?
Google SecOps (Chronicle + SOAR) is the foundation of our Adaptive MDR service. With 200+ successful implementations, we’ve engineered repeatable outcomes on top of this stack. A classic example is how we consolidated 40+ playbooks into just 3 streamlined workflows for one of our customers.
We leverage Google’s powerful data lake, SOAR, and threat intel tools to drive AI-driven detections, context-aware response, and structured workflow automation that scales.
-
Can your MDR scale across hybrid and multi-cloud environments?
Absolutely. Our architecture is built to deliver 360° threat coverage across hybrid, multi-cloud, and SaaS environments.
We support diverse telemetry ingestion pipelines (across on-prem to cloud-native) and normalize data at scale to maintain consistent visibility, control coverage, and threat detection regardless of your infrastructure complexity.
-
What kind of detection engineering do you provide?
We deliver continuous, adaptive detection engineering tailored to your environment. Our approach combines AI, curated rules, up-to-date threat intel, behavior and situational awareness models to produce high-fidelity detections mapped to attacker behaviors.
Our customers consistently achieve >90% ATT&CK coverage, and each detection is engineered with context from assets, users, and controls, so signals aren’t just timely, but truly relevant.
-
How does Netenrich MDR reduce alert fatigue and improve signal-to-noise ratio?
We reduce alert fatigue by transforming raw data into rich, contextualized intelligence. Our pipeline normalizes telemetry, adds asset and user context, and filters out noise through AI-driven detections and behavioral analytics.
The result: analysts receive fully correlated, high-fidelity incidents, not noisy alerts, customers have usually experienced a 95% drop in manual incidents per month.
-
What visibility and reporting will my team have?
You’ll have complete transparency and real-time situational awareness.
Our unified dashboards surface what matters most: threats, KPIs, posture trends, and response metrics. You’ll also receive consistent reporting with clear audit trails, posture reviews, and insights that align to your business and compliance needs.
Elevate your Google SecOps experience
For visionary CISOs, CIOs, and cybersecurity executives, the Google SecOps tech stack is more than a collection of tools — it's a strategic investment in robust enterprise security.
If you’ve embraced Chronicle SIEM, SOAR, and Mandiant breach analytics, you’re already on the path to success. Let us be your expert guide along that journey.

Featured report
Read the Predict 2025: There Will Never Be an Autonomous SOC report by Gartner, to explore how leading organizations strike the right balance between AI and human expertise.
Work from a common operational view
Siloed security and digital ops leads to gaps and inefficient duplication of tools, processes, and people. Resolution Intelligence Cloud provides a common operational view and situational awareness aligned to business risk. And it facilitates collaboration within and between teams.
- Strengthen your security posture
- Improve performance and up time
- Boost analyst effectiveness
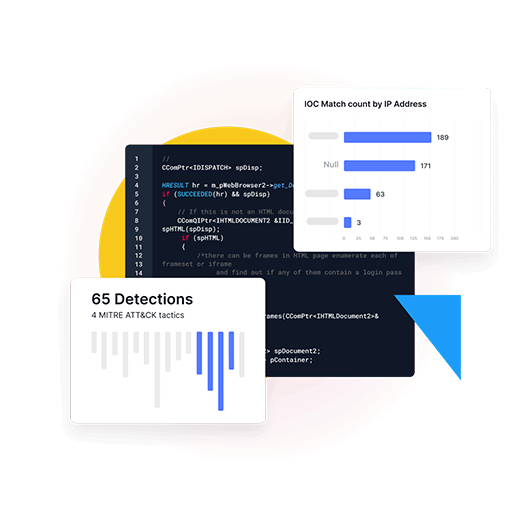
Out-innovate hackers with anomaly detection & situational awareness
Hackers are relentlessly innovative. It's futile to fight them with traditional, reactive methods.
- Identify unknowns without detection rules with advanced anomaly detection (think next-next-gen UEBA)
- Be proactive with actionable insights from data over time, correlated and mapped to the MITRE ATT&CK framework
- Identify and resolve what matters most to the business — stop wasting time on alert noise
- Communicate across functions and coordinate response fast





_2013-11-24_16-00.png?width=1024&height=293&name=1024px-Tibco_logo-_Palo_Alto%2c_CA_company-_(PNG)_2013-11-24_16-00.png)





