Build, Withstand, Recover: A Strategic Framework for Cyber Resiliency
For CIOs, CISOs, and Security Leaders Who Need to Ensure Business Continuity, No Matter the Threat
Discover how to prepare, withstand, and recover from cyber incidents with resilience-first strategies that go beyond traditional security.

Shift from Reactive Security to Proactive Resilience
In a world where cyberattacks are inevitable, resilience is non- negotiable.
This guide will empower security leaders to reframe their approach threats with a focus on operational continuity, advanced threat anticipation, and adaptive response.
Cyber resiliency is not just about prevention, it’s about ensuring operational continuity despite an attack.
Christopher Morales, CISO & Head of Security Strategy, Netenrich
What does this guide cover?
- A cyber resilience framework including peacetime and wartime strategies
- The evolving regulatory landscape (CRA, DORA, etc.) and its implications
- Tactical approaches to ensure continuity through attacks
- Real-world case examples, actionable insights and metrics to measure success beyond basic security KPIs
Traditional Security Isn’t Enough
1,876
attacks per week globally in 2024
GenAI-based
threats
are evolving faster than ever
$4.88M
average cost of a data breach, up 10% YoY
It’s time to go beyond "protect and detect." You need resiliency built into every layer of your operations.
What will you experience
during the event
Executive Roundtable: Evolving Security Operations
Discuss security metrics, the role of automation, cloud security challenges, and the shift from reactive to proactive security operations.
Executive
Networking
Engage in candid discussions with industry peers, gain strategic insights from experts, and explore innovative approaches to fortify your organization’s defenses.
Adaptive MDR & Google Cloud Security Integration
See Netenrich’s Adaptive MDR in action. Built on Google SecOps,experience how Netenrich’s next-gen approach reduces risk and improves SOC efficiency.
Unlock New Perspectives and Solutions
The interactions from this workshop will be instrumental in boosting security operations by providing intelligent threat detection & response
Topgolf Experience & Informal Networking
After the workshop, unwind with interactive golf games, casual competition, and informal discussions.
Agenda
01
Executive Welcome & Opening Remarks – Set the stage with key insights from industry leaders.
02
Interactive Roundtable Discussions – Engage in peer-led discussions on security metrics, AI-driven automation, cloud security strategies, and proactive security operations.
03
Security Operations & Technology Insights – Explore real-world use cases and best practices, including Netenrich's Adaptive MDR and Google Cloud Security.
04
Networking & Topgolf Experience – Unwind with interactive golf games, casual networking.
What makes this Guide Unique and a must-have?
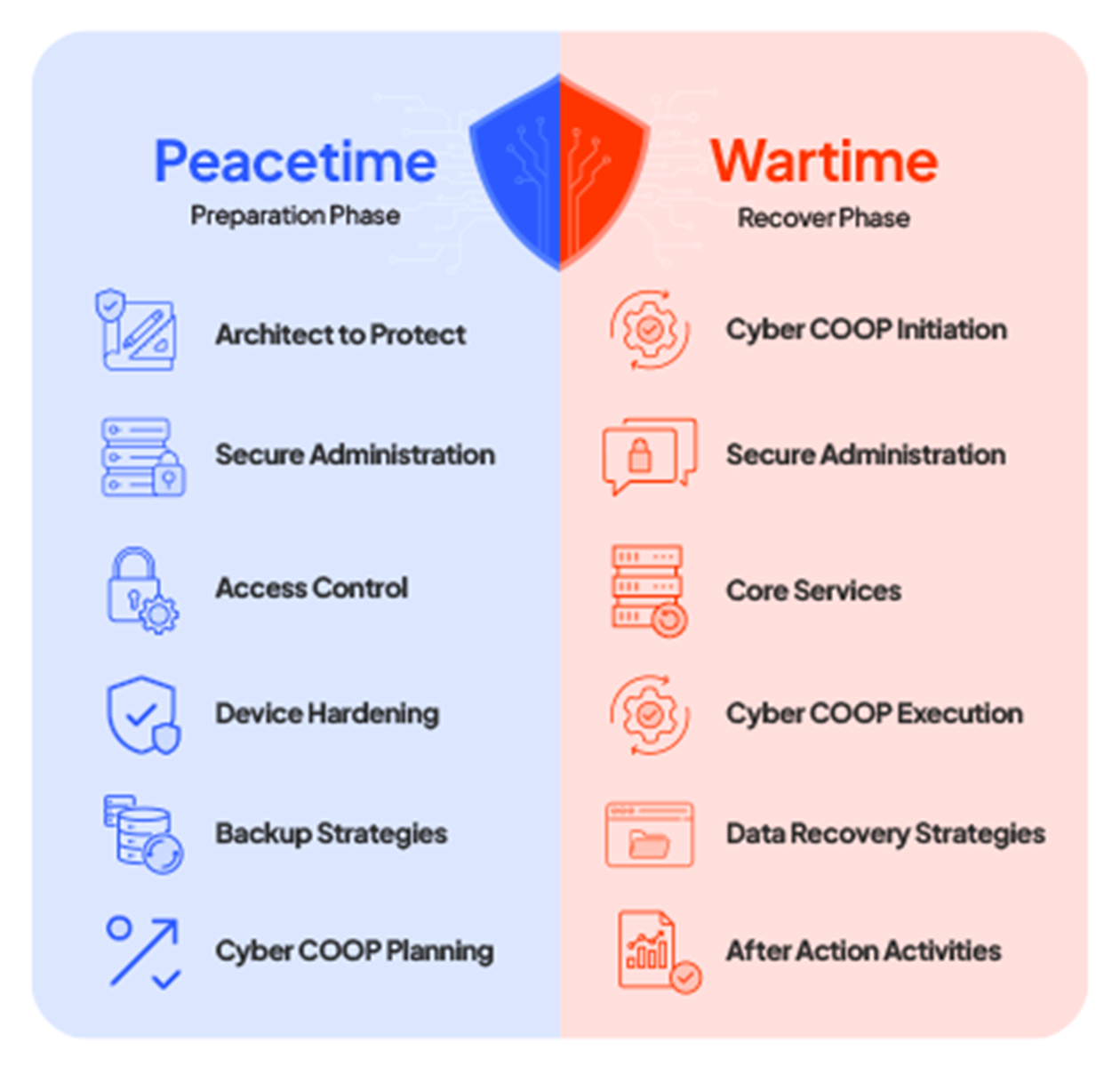
Cyber COOP Framework
6 Peacetime and 6 Wartime activities to keep your business running, even under attack
Battle-Tested Techniques
Including deception, adaptive response, segmentation, unpredictability, and more
Blueprint for Resilience
A strategic model to Understand, Prepare, Continue, Constrain, Transform, and Re-architect your security program

Who must read this guide and why?
For CIO and CTOs to Ensure Operational Continuity
Build resiliency into your digital and cloud strategy to reduce downtime and protect core business systems.
CISOs & Security Leaders to Strengthen SecOps
Go beyond threat prevention; implement adaptive defense and recovery strategies aligned to business impact while meeting evolving regulations.
IT & Risk Management Teams to Align Tech with Business Risk
Use practical COOP models and compliance-ready tactics to maintain up-time and meet evolving regulations.
Ready to Build True Cyber Resilience?
Get your copy of The Essential Guide to Cyber Resiliency and lead your organization with confidence, clarity, and continuity.
Download Guide Now

